In my previous post, we examined a particular example of a sextortion scam, showing several indications that it was not a threat to be taken seriously. But that kind of analysis – point-by-point deconstruction – is relatively hard work, and perhaps not an exercise the reader would care to take when actually under fire. Whether or not – while it can be fun to detect all the "tells" in the attacker's attempted scam – we can use more general tools, which are both easier and lead to a quicker answer. Let's look at several of them:
After the fact
First, "Google.Is.Your.Friend™", at least for our purposes here. Or, if you prefer, Bing, StartPage, or DuckDuckGo, etc.
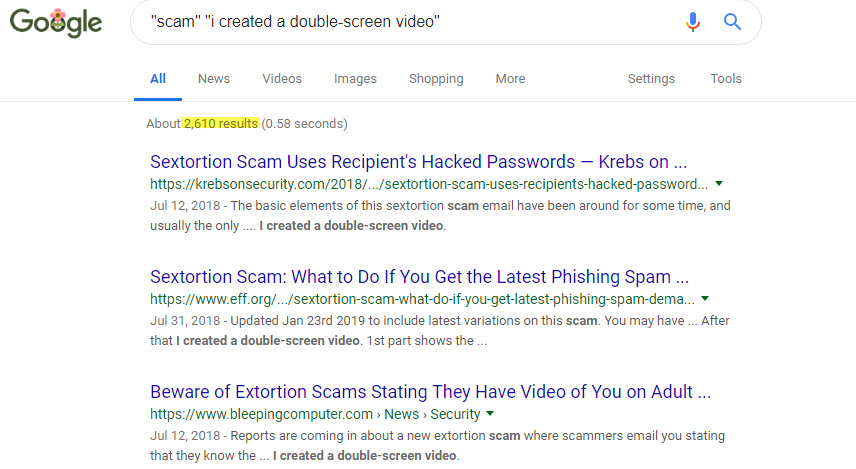
- Whatever your favorite search engine is, feed it the word scam in quotes, plus an interesting (unusual, perhaps unique) phrase from the suspect email. For example, using the sample in Tuesday's Vox post, let's select the phrase "I created a double-screen video" and see what we get:
That's a pretty good clue that it's a scam. Note that "About 2,610 results" actually is only 130 (or 236, with "omitted results included"). I didn't consider attempting to read them all, but even the last page of search results seem relevant. This huge amount of evidence should be very comforting.
- Let me point out that the "I created a double-screen video" text I selected for my search string was the first thing I tried – I didn't have to play around with a bunch of different attempts in order to find one that worked. Of course, I could have gotten unlucky and selected a "bad" text string that wouldn't have borne a helpful result, but remember: you don't have to search only once. If at first you don't succeed, search search again.
- If your first search fails, try using another "interesting text string" – repeat until you get good info, or you run out of good "interesting text string" candidates.
- If you run out of candidates, try using more general search terms – for instance: scanning for, in quotes, "scam" "email" "blackmail" casts a much wider net. Too wide, perhaps ("About 5,020,000", according to Google's first pass; actually, "only" 900), but if you don’t try this as your first search, you may find helpful information should your earlier searches not be fruitful. Also, you might choose to use a word other than "scam", depending on the situation. But I suggest you don't use words only from the email itself – use some kind of a qualifier to help discern whether it's true or false.
- In rare cases, a Google search may fail where another search engine returns helpful links. If your search engine brings you no joy, try another.
If your first search fails but a subsequent one succeeds, should you trust the failures or the success(es)? Remember that, in a court of law, if a witness is shown to have provided false testimony, all testimony from that witness is considered suspect and in need of independent corroboration. So trust the successes, particularly if they come from reputable sites like WeLiveSecurity, your computer security vendor, or e.g., krebsonsecurity.com. [Keep in mind that anyone can set up a website; while I am not aware of any cases to date for blackmail, cybercriminals certainly could set up a site or sites that try to convince potential victims that these scams are actually real. So be sure to look at the source to decide whether to trust it or not.]
Suppose that, perhaps because you have encountered a brand new blackmail scheme (or at least a brand new text for a blackmail scheme) that your (possibly repeated) searching doesn't turn up any reassuring findings at all. Fear not! There are other things to try.
Remember: the blackmailer has given you a window of opportunity (a day, 72 hours, whatever) to respond, so start the ball rolling at your earliest opportunity to determine whether the threat is real. Just in case it's not a scam. And do not delete the email: preserve the evidence!
- Contact law enforcement: they may have seen it, and be able to tell you that it is fake. Or, if they have not encountered it before, it's good for them to be made aware. No, they're probably not going to investigate your case, but the more they are aware of the magnitude of crime in cyberspace, the more justification there is to ask for, and to deploy, resources to fight such crime. Note: even if your search was successful in debunking the scam, you might consider contacting LE anyway: Again, helps them understand the "scope of the problem."
- Contact your computer security vendor: there's a very good chance that their tech support may know about it already, and that the company is preparing to block the next wave of such attacks if not blocking them already. And if they are not aware of this variant, they'll certainly want to know so that they may protect their customers. So while LE might not take action, your computer security vendor almost certainly will. ESET customers – in fact, non-customers as well – may submit suspicious samples via the procedure documented here; other vendors have similar file-submission capabilities. Note that if you submit a sample to an antivirus vendor, you probably won’t get a reply: they get hundreds of thousands of unique suspicious samples each day. But you can scan, after a day or so, with their scanner, to see if it is detected as something. If it's detected as a scam, well: there you are.Why didn’t your security solution block it? While security software can, and often does, block things it has never seen before (using e.g., heuristic techniques and machine learning), sometimes something brand new will get past the defenses. Maybe you were in that first wave of potential victims; you can help others by reporting this sort of thing. Crowd-sourcing works, and it helps protect YOU.
- Contact your email provider: Whether it's Gmail, Outlook, your company's IT department, or some other entity, it's not good to allow scams (one of many forms of spam) in their customers' Inboxes. So let them know, which will assist them to tweak their spam filters.
- If you like to bash your head against the wall, contact your legislators (federal, state/provincial, and local) to demand legislation to have international policing against this sort of crime, and to compel ISPs to scan email traffic "over-the-wire" and block anything malicious that they see en route. That won't help for encrypted traffic, but it’s a start. Note that you don't have to wait to receive one of these scam emails to contact your legislators – start now! [There. Now I don't have to mention this approach in the Preventative measures section also.]
- If you are of a technical bent, you might consider submitting the email to an online analysis service such as VirusTotal. This will give the results of a scan by each of many different security products – if a good number of products say it's a scam (or otherwise malicious), you can be pretty certain that it is. If only a few – or none – flag it, that doesn't mean it's innocent, though: it could be very new, or it could be that the scanning engines in use by VirusTotal are not the full-fledged ones used by the security products on endpoints, but rather the command-line ("DOS") scanner, which typically can't leverage the full power of the whole security suite.
- One last thing: you might wonder, "If my computer wasn't hacked, how did the attacker know my email address?" Well, first of all: you get spam, don't you? Hopefully most of it ends up in your junk mail folder, but the mere fact that there's anything in that folder means that your email address is "out there somewhere." But more to the point: the cybercriminal probably found your email address on one of the websites that catalogs the data exposed by one of the many security breaches; indeed, this was the modus operandi of our post last July, where the attacker offered, as "proof", a password associated with the victim in some unspecified way. So the attacker probably grabbed one of those data dumps and just spammed a bunch of the email addresses there with this blackmail scam. [It's a bit delicate to ascertain from these databases exactly what was compromised, based on only an email address and the data linked to it, so the mere fact that there's the victim's email address and a password known to the victim certainly does not necessarily mean that the attacker has a working email/password combination. We'll examine how to assess the true situation, carefully, in a future Vox]
Preventative measures
You don’t need to do all these things above to discern that something is a scam – though the more you do, successfully, the more likely you are to be convinced. But as you can see, this can take some time, so let's look at what you can do to be proactive, and help prevent the need to take remedial action in the first place. And here, I recommend that you implement as many of them as possible:
- Install/enable spam filtering
- on your email provider's server – some email providers allow you to turn off spam filtering which, in most cases, you do NOT want to do. Make sure it's on!
- on the server that hosts your Inbox, which might be different from the server used by your email provider. For example, suppose you forward some messages from your Gmail Inbox to your Outlook email address at work: you'd want spam filtering on both Gmail and on the Outlook Exchange server.
- on your devices – you want anything that got past the spam filters above to have one last chance to get caught. Typically, this will be by your computer security suite, but there are standalone spam filters for endpoints as well.
- Make sure that you use top-quality, up-to-date, updated computer security software. If you don’t know what products are top quality, there are several competent, independent security software testers out there; have a look at the Virus Bulletin VB100 Award, for example. Security suites update themselves automatically to detect the newest threats, but it's sometimes not obvious that one has the up-to-date product itself. Check your computer security vendor's website to make sure you're not using today's updates on a five-year-old version of the software!
- Of course, assuming you have these options enabled, security software will protect you from spam, including known sextortion scams. And often against unknown ones as well.
- Moreover, it will protect you against many other things – things that are far more dangerous, such as ransomware.
- Last but not least: if your security suite allows it, lock the settings so that a password is required to disable your protection. A strong, unique password. More on this below.
- If you do all these things, you'll know you're well-protected … which will make it less likely that, should you encounter one of these blackmail scams, you'll be inclined to believe it. The cybercriminals count on fear to make their potential victims act quickly and irrationally; by protecting yourself as well as possible, you reduce the efficacy of their tactics.
- It also belies, or at least puts in strong doubt, the claim that the cybercriminal installed malware on your computer.
- Similarly, make sure that your OS, be it Windows, macOS, or Linux, is up-to-date and fully patched. This probably won't prevent spam, but the more secure your systems, the better.
- Naturally, patching your apps, and using their current versions, helps as well.
- You've probably heard it a zillion times before, and hopefully you've listened and acted – but in case you have not already made sure that all your passwords are both unique and difficult to guess, PLEASE do so with all due haste. This has multiple benefits:
- If an account or computer is compromised, none of your other accounts or devices are at risk. Change the compromised password, clean up the system that used that password, and move on. No need to reset passwords on all your other devices and accounts (assuming you didn’t keep a spreadsheet with all your passwords, unencrypted, on the compromised machine!)
- If there is a breach at one of your financial (e.g., JP Morgan Chase), credit (e.g., Equifax), commercial (e.g., Target and Home Depot), health institutions (e.g., Anthem, Premara, Excellus), or whatever else, and the password database is stolen, and those data are put online: then if you check for your password being one of the ones compromised, you'll know exactly which one account is the problem. Note that in our post last July, the "proof" was that the cybercriminal "knew" your password. If your passwords are unique, then it's clear to which account the password belongs, and if that is not the same as the one as the email account used to "notify" you? The attacker's scheme is laid bare.Note: if, like me, you sometimes have to set up an account – typically with a retailer – that requires a password and also an email address to use to contact you: then if that site is hacked and the customer database stolen, the password won't match that for the email account. So again, the scam is exposed … assuming you have different passwords for each account!!
- If you are able, set up Two-Factor Authentication (or Multi-Factor Authentication) for as many accounts as you can ... preferably not using SMS, which is less secure than other 2FA methods. Then, even if an attacker gets your password, s/he can't access your account because logging on requires the 2FA authentication as well. And, for this example, you'll know that the attacker couldn't send email form your account, since that would require the 2FA authentication.
- Keep up with the literature: if you're interested in computer security, choose one or more security websites you trust and read whenever you can. If you can't spare the time to read everything (and who can?), just search the site(s) when you need to find something specific. Also, consider subscribing to the site's news feed; at WeLiveSecurity, just search for [Newsletter], type your email address in the box, and click [Submit] and you'll get regular announcements of our content – be it news of general interest, more technical summaries, or deep dives into highly technical material. Then read the articles of most interest to you.
What next?
Well, enough for today; in my next post, we'll examine specific examples of a bunch of these sextortion scams, which will wrap up this series. At least until the next interesting development!
About Vox
Got a computer security question that’s not product-specific? Leave us a comment here or use our AskESET form on the Contact Us page.