On Monday, October 22nd, a disruption action involving law enforcement bodies worldwide targeted “3ve”, a major online ad fraud operation. Today, on November 27, 2018, a 13-count indictment against eight defendants was unsealed. Out of these eight defendants, three are in custody and awaiting extradition. Ad fraud campaigns have plagued the internet advertising ecosystem for years, syphoning ad revenues away from legitimate companies. The basis of the fraud is always the same: software mimics user behavior to make it seem as if real people are clicking on links or viewing online ads, although this is all automated, malicious behavior. Other strategies exist: another major ad fraud campaign was Stantinko, which hijacked users’ clicks to redirect them to ads of their fraudsters’ choosing. In the case of 3ve, it was navigating through ads without the affected users’ knowledge.
One critical aspect to make such schemes work, and bypass existing ad fraud protection measures, is to make sure the faked requests are coming from legitimate users through a large pool of IP addresses. 3ve relied on at least two different botnets to have access to such a pool: Boaxxe and Kovter. Since ESET researchers actively investigated both of these botnets in the past, we were able to help the operation against 3ve by providing technical data to law enforcement. Of course, an operation of this scale requires collaboration from different industry partners, each providing their own expertise to better understand and stop the threat.
The US-CERT has published an alert highlighting the 3ve’s botnet-mediated behavior and how it interacts with Boaxxe and Kovter botnets. It also lists precautionary measures to avoid getting afflicted in the first place by these last two malware strains. If you are worried that your Windows system might be compromised by this threat and are not an ESET customer, you can download and use the free ESET Online Scanner, which will remove any threats, including Kovter and Boaxxe, that it might find on your system.
In this blog post, we will detail how we obtained the technical data on the Boaxxe and Kovter infrastructure needed to help the disruption operation.
Boaxxe
We have already published a detailed analysis of this ad fraud botnet in a two part article in 2014. Back then, Boaxxe, also known as Miuref, was rerouting real user traffic to links it controlled. More specifically, when a victim was looking for a particular keyword in a popular search engine, it would redirect the victims search result click to a website it controlled instead of the websites returned by the search engine. This was made possible by using a Firefox or Chrome browser extension or by using Internet Explorer in embedded mode. However, a Boaxxe-compromised system has the ability to proxy traffic, making it look like it is originating from it. 3ve is using this capability to perform its ad fraud scheme.
Boaxxe’s proxy functionality is quite simple: it receives an RC4-encrypted DNS or HTTP request from its C&C server, decrypts and executes it, and finally sends the result back to the C&C server. A classic, decrypted, HTTP request coming from 3ve towards a compromised Boaxxe system looks like this:
GET /banners/ajtg.js HTTP/1.1
Host: img.1rx.io
Connection: keep-alive
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.110 Safari/537.36
Accept: */*
Referer: http://eatingwell.com/recipes/17986/side-dishes/
Accept-Encoding: gzip, deflate, sdch
Accept-Language: en-US,en;q=0.8The compromised system would make this request, effectively “visiting” the page hosting the advertisement, and send back the response to its C&C server. This is how 3ve leveraged Boaxxe-compromised systems to perform its ad fraud operations. Interestingly, we have witnessed similar requests as the one above sent to Boaxxe-compromised systems since at least early 2016. At that time, only Boaxxe bots with US IP addresses were used as proxies, suggesting the 3ve operators were mainly interested in ad traffic from that region of the world.
Kovter
ESET first detected Kovter in 2014, when it was ransomware. The Kovter malware family has evolved quite a bit since then to become ad fraud malware. Some of the most notable features that were added throughout the years include deception and stealth. Noteworthy in terms of deception is its ability to send fake traffic if it detects a network monitor and to terminate its own spawned process if Windows Task Manager is started. It is now even stealthier than before, using so-called “fileless” persistence by storing its malicious payload encrypted in the Windows registry. Moreover, it makes sure to perform ad fraud only when the system is unused or the display is powered off. It has also the ability to mask all visuals or sound effects when viewing advertisements to make its activities unnoticeable to the user.
3ve operators leveraged the Kovter botnet differently than the Boaxxe one. A compromised Kovter system can receive a task from its C&C server and directly execute it using a hidden Chrome Embedded Framework browser. We have been tracking the Kovter botnet for more than two years through our botnet tracker platform. This system enables us to track the most prevalent botnets in real time. Analyzing the data obtained through it, we can: map the botnet network infrastructure; track its different configuration files; download its malware updates; see which commands it receives; and, see which other malware families it installs. ESET’s platform’s main purpose is to help maintain the best levels of protection for our users and to enrich ESET Threat Intelligence feeds. However, it can also be used to provide technical data in disruption operations, such as those we took part in against Dorkbot in 2015 and Andromeda/Gamarue in 2017.
Kovter, just like Boaxxe, has been delivered to unsuspecting victims in a number of different ways, including spam, drive-by downloads and pay-per-install schemes. One interesting detail is that both of these malware families have been installed using Nemucod while the 3ve operation was active.
As stated earlier, the first signs we saw of the 3ve operation was through our Boaxxe monitoring, where compromised systems located in the US were used to proxy ad fraud requests. Looking at our Kovter telemetry, we can see that the Kovter botnet has mainly targeted North America.
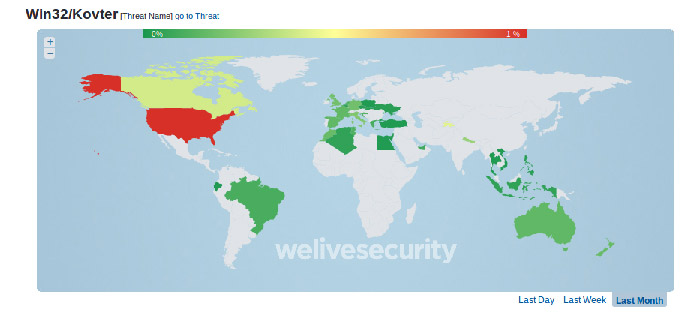
Figure 1 Kovter Telemetry in October 2018
Kovter C&C servers work in layers. First, the Kovter bot will retrieve its static configuration stored in its resource section. The configuration file is stored encrypted using the following format:
<16 bytes reversed RC4 key><base64–encoded, encrypted data><16 bytes of padding>
This configuration file contains, among other things, a list of first level C&C servers as well as the RC4 key required for network communication.
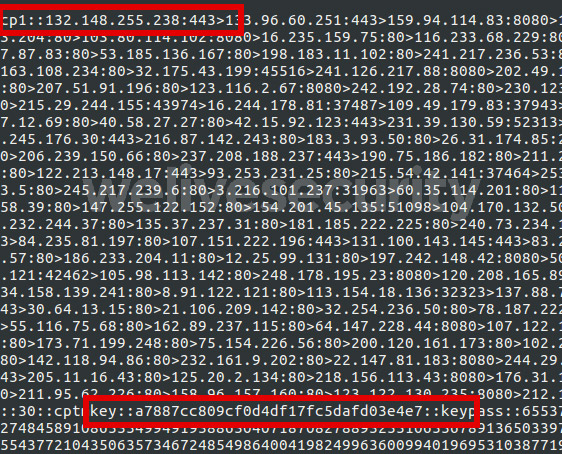
Figure 2 Decrypted Kovter static configuration file showing the first level C&C server IP addresses section (“cp1”) and the RC4 key section (“key”)
To retrieve the second level C&C servers, the bot sends an HTTP POST request to the first level C&C servers with the following format:
RESP:BOT|c:IPS|vsn:1|<random hex string>
The hex string is composed of random hexadecimal characters [0-9a-f] and its length is between 32 and 128 characters. The POST request is encrypted using a random RC4 key. This random key is appended to the packet and the overall message is encrypted using the RC4 key found in the static configuration file. The resulting communication is sent through a raw socket directly to the first level C&C server. The server response contains the second level C&C servers. These are responsible for handing over the ad fraud tasks to the bot.
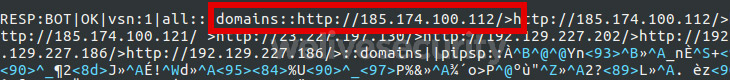
Figure 3 Decrypted response from Kovter first level server showing the second level C&C server IP addresses section ("domains")
Through our Kovter tracking, we were able to identify several first level and second level C&C servers. These data were passed to law enforcement to help with the disruption operation.
Interestingly, since the disruption operation, we have seen a shift in the behavior of the current first level C&C servers. They are now returning the conventional “localhost” IP address (i.e. 127.0.0.1) as their second level C&C servers. Of course it is impossible for us to know the reason behind this change, but it is likely they have done this to put their botnet on hold while they figure out what has hit them.
Closing remarks
Ad fraud botnets have been around for a long time and have cost a significant amount of money to advertisers worldwide. Being able to fight back and have the ability to disrupt operations on the scale of 3ve by striking at various aspects of its operation is vital to the internet ecosystem’s integrity. ESET is proud to be able to make a difference and provide law enforcement assistance whenever possible.
If you believe that you are infected with Boaxxe or Kovter, we have a free tool for you. ESET Online Scanner detects and removes malware, including thousands of variations of the Boaxxe and Kovter modules.
For more details on the 3ve ad fraud mechanisms, you can read the Google and White Ops white paper on this operation here.
Special thanks to Matthieu Faou, Juraj Jánošík, Viktor Lucza, Filip Mazán, Zoltán Rusnák and Richard Vida for their help in this research.