Malware authors keep testing the vigilance of Android users by sneaking disguised mobile banking Trojans into the Google Play store. We’ve recently analyzed a set of 29 such stealthy Trojans, found in the official Android store from August until early October 2018, masquerading as device boosters and cleaners, battery managers and even horoscope-themed apps.
Unlike the increasingly prevalent malicious apps relying purely on impersonating legitimate financial institutions and displaying bogus login screens, these apps belong to the category of sophisticated mobile banking malware with complex functionality and a heavy focus on stealth.
These remotely controlled Trojans are capable of dynamically targeting any apps found on the victim’s device with tailor-made phishing forms. Aside from this, they can intercept and redirect text messages to bypass SMS-based two-factor-authentication, intercept call logs, and download and install other apps on the compromised device. These malicious apps were uploaded under mostly different developer names and guises, but code similarities and a shared C&C server suggest the apps are the work of a single attacker or group.
The 29 malicious apps have all been removed from the official Android store in the meantime after ESET and fellow researchers notified Google of their malicious nature. Before being pulled from the store, however, the apps were installed by almost 30,000 users in total.
How do they operate?
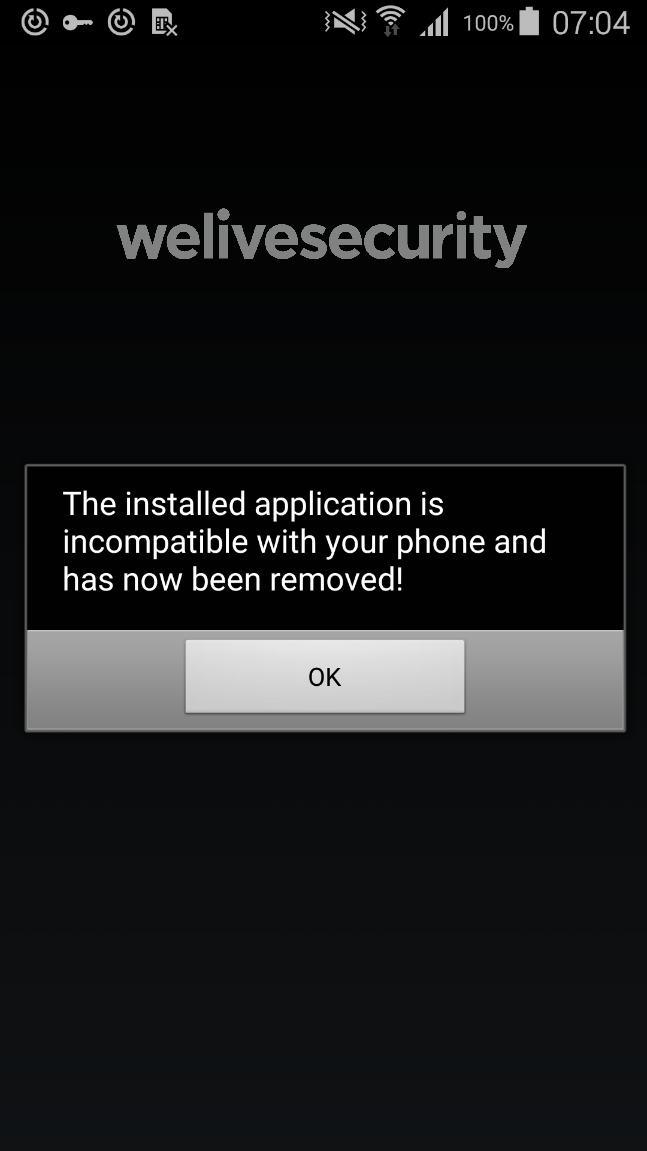
Once launched, the apps either display an error claiming they have been removed due to incompatibility with the victim’s device and then proceed to hide themselves from the victim’s view, or deliver the promised functionality – such as displaying horoscopes.
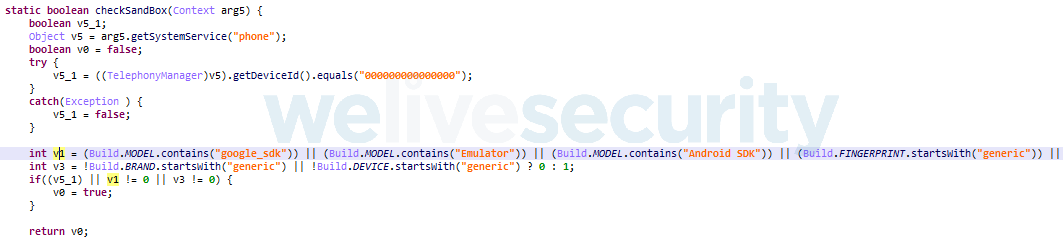
Regardless of which of the preceding activities one of these apps displays, the main malicious functionality is hidden in an encrypted payload located in each app’s assets. This payload is encoded using base64 and then encrypted with an RC4 cipher using a hardcoded key. The first stage of the malware’s activity is a dropper that initially checks for the presence of an emulator or a sandbox. If these checks fail, it then decrypts and drops a loader, and a payload that contains the actual banking malware. Some of the apps we analyzed contained more than one stage of such encrypted payloads.
The functionality of the final payload is to impersonate banking apps installed on the victim’s device, intercept and send SMS messages, and download and install additional applications of the operator’s choice. The most significant feature is that the malware can dynamically impersonate any app installed on a compromised device. This is achieved by obtaining the HTML code of the apps installed on the device and using that code to overlay legitimate apps with bogus forms once the legitimate apps are launched, giving the victim very little chance to notice something is amiss.
How to stay safe
Fortunately, these particular banking Trojans (the full list can be found in the IoCs section) do not employ advanced tricks to ensure their persistence on affected devices. Therefore, if you suspect you have installed any of these apps, you can simply uninstall them under Settings > (General) > Application manager/Apps.
We also advise you to check your bank account for suspicious transactions and consider changing your internet banking password/PIN code.
To avoid falling victim to banking malware, we recommend that you:
- Only download apps from Google Play; this does not ensure the app is not malicious, but apps like these are much more common on third-party app stores, where they are rarely removed once uncovered, unlike on Google Play
- Make sure to check the number of downloads, app ratings and the content of reviews before downloading apps from Google Play
- Pay attention to what permissions you grant to the apps you install
- Keep your Android device updated and use a reliable mobile security solution; ESET products detect and block this threat as Android/TrojanDropper.Agent.CIQ.
Special thanks to Nikolaos Chrysaidos for bringing some of these malicious apps to our attention.
Indicators of Compromise (IoCs)
| App name | Package name | Hash | Installs |
|---|---|---|---|
| Power Manager | com.puredevlab.powermanager | 7C13ADEFC2CABD85AD8F486C3CBDB6379811A097 | 10+ |
| Astro Plus | com.astro.plus | 24D2ED751A33BD965A01FA87D7A187D14D0B0849 | 0+ |
| Master Cleaner - CPU Booster | bnb.massclean.boost | 101DA4333A26BC6D9DFEF6605E5D8D10206C0EB4 | 5,000+ |
| Master Clean - Power Booster | mc.boostpower.lf | E5DC8D4664167D61E5B4D83597965253A8B4CB3B | 100+ |
| Super Boost Cleaner | cpu.cleanpti.clo | 33D59A70363857A0CE6857D201B764EF3E8194DD | 500+ |
| Super Fast Cleaner | super.dupclean.com | E125AC53050CAFA5A930B210C8168EA9ED0FD6F1 | 500+ |
| Daily Horoscope For All Zodiac Signs | ui.astrohoro.t2018 | C3C45A7B3D3D2CB73A40C25BD4E83C9DA14F2DEA | 100 + |
| Daily Horoscope Free - Horoscope Compatibility | com.horochart.uk | CD5817AB3C2E4AE6A18F239BDD51E0CC9D7F6E25 | 500+ |
| Phone Booster - Clean Master | ghl.phoneboost.com | 9834B40401D76473D496E73884947D8A9F1920B3 | 1,000+ |
| Speed Cleaner - CPU Cooler | speeeed.cool.fh | 7626646C5C6D2C94B9D541BD5A0F320421903277 | 100+ |
| Ultra Phone Booster | ult.boostphone.pb | 6156081484663085B4FC5DEAEBF7DA079DD655C3 | 1,000+ |
| Free Daily Horoscope 2019 | fr.dayy.horos | 4E7F12F07D052E7D1EFD21CD323D8BAD9A79933B | 50+ |
| Free Daily Horoscope Plus - Astrology Online | com.dailyhoroscope.free | c0be22c44e5540322e0ffbf3a6fe18ce0968d3b5 | 1,000+ |
| Phone Power Booster | pwr.boost.pro | FCB8E568145AF2B6D8D29C0484417E51DD25717F | 1,000+ |
| Ultra Cleaner - Power Boost | ua.cleanpower.boost | CB37C8C44750874BA61F6F95E7A7C29073CB51DC | 50+ |
| Master Cleaner - CPU Booster | bnm.massclean.boost | 63E1C18D87F41ABF9956FC035D29D3C2890453EE | 5,000+ |
| Daily Horoscope - Astrological Forecast | gmd.horobest.ty | 90f41c64b3ab3f3b43e9d14b52f13143afb643da | 1,000+ |
| Speed Cleaner – CPU Cooler | speeeed.cool.gh | 56be07b21c9992a45c3b44b2e8a26b928e8238e2 | 0+ |
| Horoscope 2018 | com.horo2018i.up | c8dc0e94f38556cd83ca6a693fa5b6d7ae3957f7 | 1,000+ |
| Meu Horóscopo | my.horoscop.br | 92808ca526f8e655d8fa8716ab476be4041cd505 | 1,000+ |
| Master Clean - Power Booster | mc.boostpower.cf | ab88a93b0e919e5e07cf867f4165f78aa77dc403 | 50+ |
| Boost Your Phone | boost.your.phone | 5577c9131f026d549a38e3ce48c04a323475927e | 1,000+ |
| Phone Cleaner - Booster, Optimizer | phone.boost.glh | 988AB351549FEB2C1C664A29B021E98E3695A18A | 1,000+ |
| Clean Master Pro Booster 2018 | pro.cleanermaster.iz | b9d32241d169dfd4ca5674dffa357796b200bc2f | 10+ |
| Clean Master - Booster Pro | bl.masterbooster.pro | bcb9ef41fea8878eb10f4189dd55bfe1d03a64b3 | 5,000+ |
| BoostFX. Android cleaner | fx.acleaner.e2018 | 99bff493d201d42534eec9996fd0819a | 50+ |
| Daily Horoscope | day.horocom.ww | 971a0cf208f99c259966b20aa10380c1 | 1,000+ |
| Daily Horoscope | com.dayhoroscope.en | 25e95b32832a491108835b382c4f14aa | 1,000+ |
| Personal Horoscope | horo.glue.zodnow | 0dcaf426bbc3b484aa4004f5c8e48a19 | 1,000+ |
You might also be interested in the following articles:
Fake finance apps on Google Play target users from around the world
Fake banking apps on Google Play leak stolen credit card data
Android users: Beware these popularity-faking tricks on Google Play