Picking up where we left off in Part 1, we will now look at how many US financial institutions apparently aim to attain ultimate safety for their critical account data. First, however, let us stop to consider what contributed to putting such considerations on the front burner.
Increasingly, some types of attacks have been trending towards outright destruction, as opposed to “mere” disruption or theft. A number of organizations have learned this the hard way in recent years, including Saudi Arabian state-owned oil and gas firm Saudi Aramco and entertainment company Sony Pictures Entertainment. They both saw tens of thousands of their computers wiped out in particularly destructive attacks.
The onslaught at Sony, in October 2014, was one of the first massive hacks of an American corporate infrastructure that was largely aimed at data destruction. As part of its toll, the attack completely erased half of the company’s servers and computers, reducing a number of employees to using pen and paper to do their jobs.
This incident raised concerns across the board. US banks, for example, took part in a series of regular cybersecurity simulation exercises between 2014 and 2016 that were aimed at testing their ability to ward off similarly destructive attacks. Lessons learned during these drills, known as the “Hamilton Series”, gave rise to a last-resort mechanism that is intended to further step up the banks’ game vis-à-vis data resilience.
“The significant other”
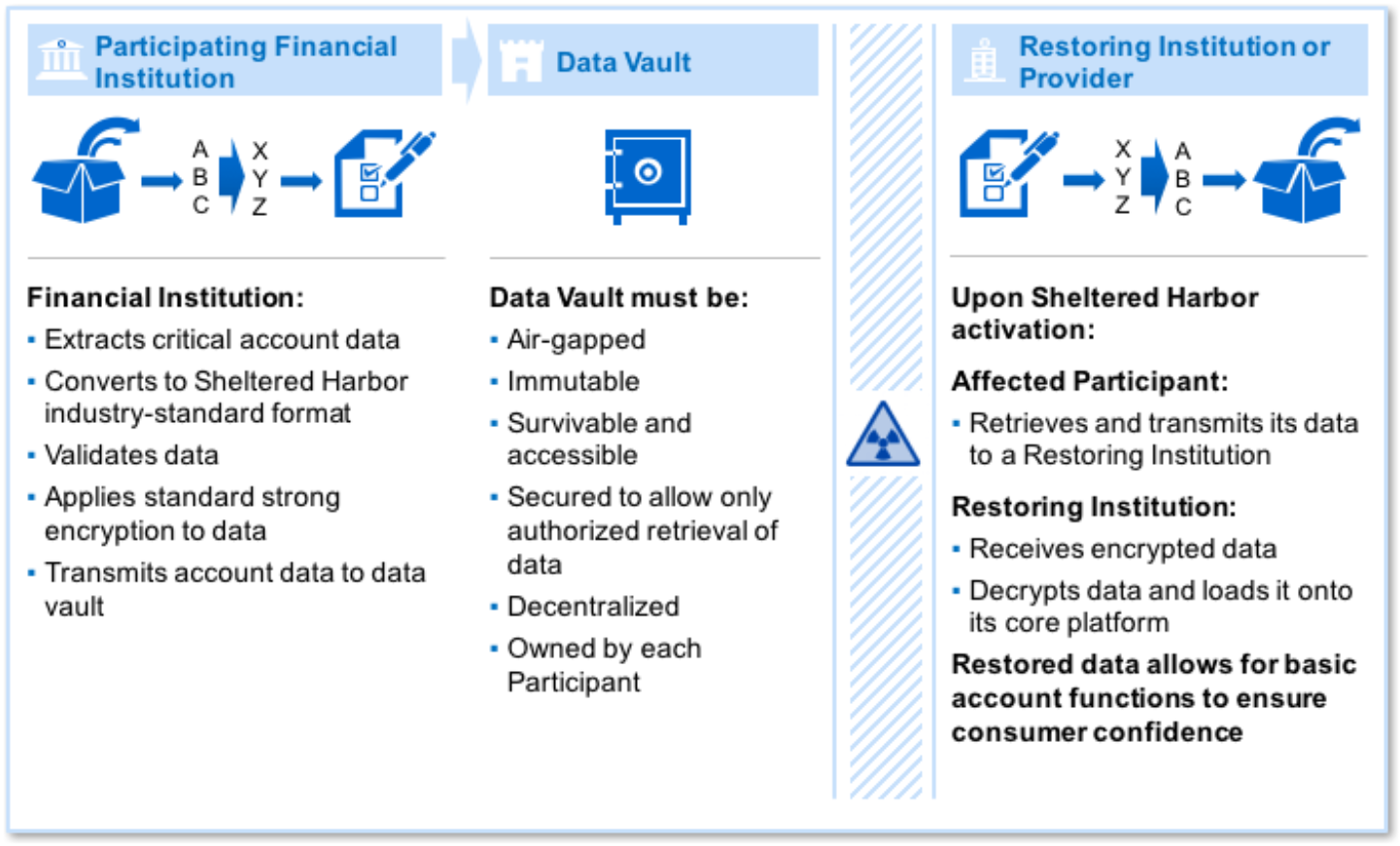
Enter an initiative dubbed “Sheltered Harbor”, which requires its participants to convert their up-to-date customer account and transaction information into a standardized format, before encrypting and placing it into secure, air-gapped and offsite “data vaults”. Also, according to the high-level overview of the program, the data must be unalterable and, if ever needed, must be retrieved from the “fallout shelter” exactly as when they were archived.
Crucially, the initiative seeks to add an extra layer of resiliency on top of the standard “restore and recovery” programs in that the affected institution would not be left to its own – at that time incapacitated – devices. Banks need to form pairs. If a member of the pair is unable to quickly restore normal service on its own, it can fall back on its backup peer, which loads the affected bank’s data into its own systems. This would be possible thanks to the standardized format required by the program.
However, focusing too much on a single bank would be missing the point. At the end of the day, the goal is not to salvage the hapless bank. The key idea is to ensure that if a bank crumbles under the weight of an egregious cyberattack or a particularly destructive accident, the incident won’t snowball. The ripple effects of such a scenario are all but impossible to predict. However, the main concern is that a particularly serious incident could spook the public and trigger a sweeping run on not only the impacted bank.
This is because, on top of downtime and financial fallout, attacks targeting the confidentiality, integrity or availability of critical bank account data share another possible consequence – the loss of consumer trust. That is saying something for a sector that is essentially predicated on consumer confidence. Trust is a fickle mistress, and we all know that its erosion can trigger a chain of events with hardly-predictable ramifications.
Collectively, the participating banks are said to hold some two-thirds of retail accounts in the US, and it’s claimed that a sizable portion of retail brokerage accounts are also being included. Having a contingency plan that involves industry-wide collaboration is particularly sensible in a sector in which the roof may cave in with a particularly loud bang.
Indeed, a solid backup and disaster recovery solution in general can ultimately mean a difference between a few days’ inconvenience and lost service (followed by months or years rebuilding trust) and total business collapse. In a way, then, Sheltered Harbor may be thought of as insurance that is good to have, but that nobody wants to ever use.
In conclusion
All told, the value of a reliable backup plan in general is especially apparent when dealing with a situation that is not entirely under our control. Data may be lost or corrupted in various ways, but successful recovery is conditional on a dependable backup strategy. There is no denying that the current cybersecurity climate dictates paying increasing attention to data restoration and recovery, which are themselves intrinsic to the cybersecurity defense playbook.
Although World Backup Day comes only once a year, we all know that both individuals and organizations need to create their backups much more often. Implementing a solid backup routine clearly goes a long way towards bolstering our data defenses. And while we're at it, we should not forget that ensuring that we're actually able to restore data from a backup is equally as important. Happy World Backup Day!