WannaCryptor, also known as WannaCry, is said to have reared its ugly head again, striking a Boeing production facility in North Charleston, South Carolina, on Wednesday, the Seattle Times reports.
Unlike in May 2017, however, the new attack doesn’t appear to have inflicted any significant damage. Regardless, the mere fact that the feared ransomware may have reappeared was enough to trigger some alarm at the aircraft manufacturer and beyond.
The outreak was revealed in a memo that Mike VanderWel, chief engineer at Boeing Commercial Airplane production engineering, is believed to have distributed to staff, calling for “all hands on deck.”
“It is metastasizing rapidly out of North Charleston and I just heard 777 (automated spar assembly tools) may have gone down,” The Seattle Times quoted VanderWel as having written . He went on to voice concern that the malware could compromise equipment used in functionality tests of airplanes and potentially even “spread to airplane software”.
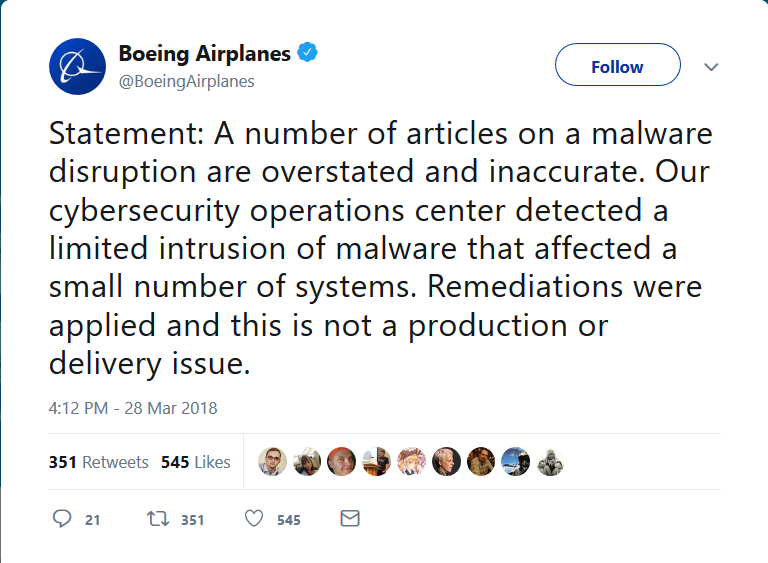
Once the dust settled, however, Boeing issued a statement that shed some more light on the issue. Calling the news accounts “overstated” and “inaccurate”, the company essentially indicated that the infestation had been nowhere near as severe as initially reported and that the concerns had been unsubstantiated.
The newspaper also quotes Linda Mills, the head of communications for Boeing Commercial Airplanes, as saying that “to the best of our knowledge, the crisis is over and the attack did no significant damage”.
CBS News quoted another Boeing official as saying that a patch had been applied to fix the company’s computer system and that the malware had “impacted a limited number of older systems”.
WannaCry (detected by ESET as WannaCryptor.D and also known as Wcrypt) gained infamy after an attack that began on May 12 of last year. Spreading like wildfire, it ended up affecting around 300,000 computers in approximately 150 countries.
The incident at the aircraft maker serves to highlight the risks of not installing security updates. Indeed, Microsoft made available a patch on March 14th, 2017, for all supported versions of Windows to plug the very hole that WannaCryptor would exploit two months later. In the aftermath of the global outbreak, Microsoft even issued rare emergency patches for no-longer supported systems, including Windows XP, in order to stymie later iterations of the attack.