For most of the second season of Mr. Robot, one of the most frequently asked questions was “Where is Tyrell?” Yes, he made a star appearance at the end of the season, but until this episode, we had no idea where he'd been for the past few months. In a series of flashbacks, we find out how, following the attack that ended with E Corp’s data encrypted, Tyrell was "recruited" by the Dark Army.
This episode doesn't really stand out technically speaking, as nothing is compromised, but we can take away two important tips relevant to cyberattacks today.
*Warning, the following contains spoilers.
The importance of preparation
During the months that Tyrell was missing, we see him working in isolation at a Dark Army property. He carries out various jobs, some of them closely related to the events that occurred in the second season of Mr. Robot, as we shall discuss below.
Although he seems confused at the beginning of his “captivity”, we soon see the importance of good preparation in attack and defense alike.
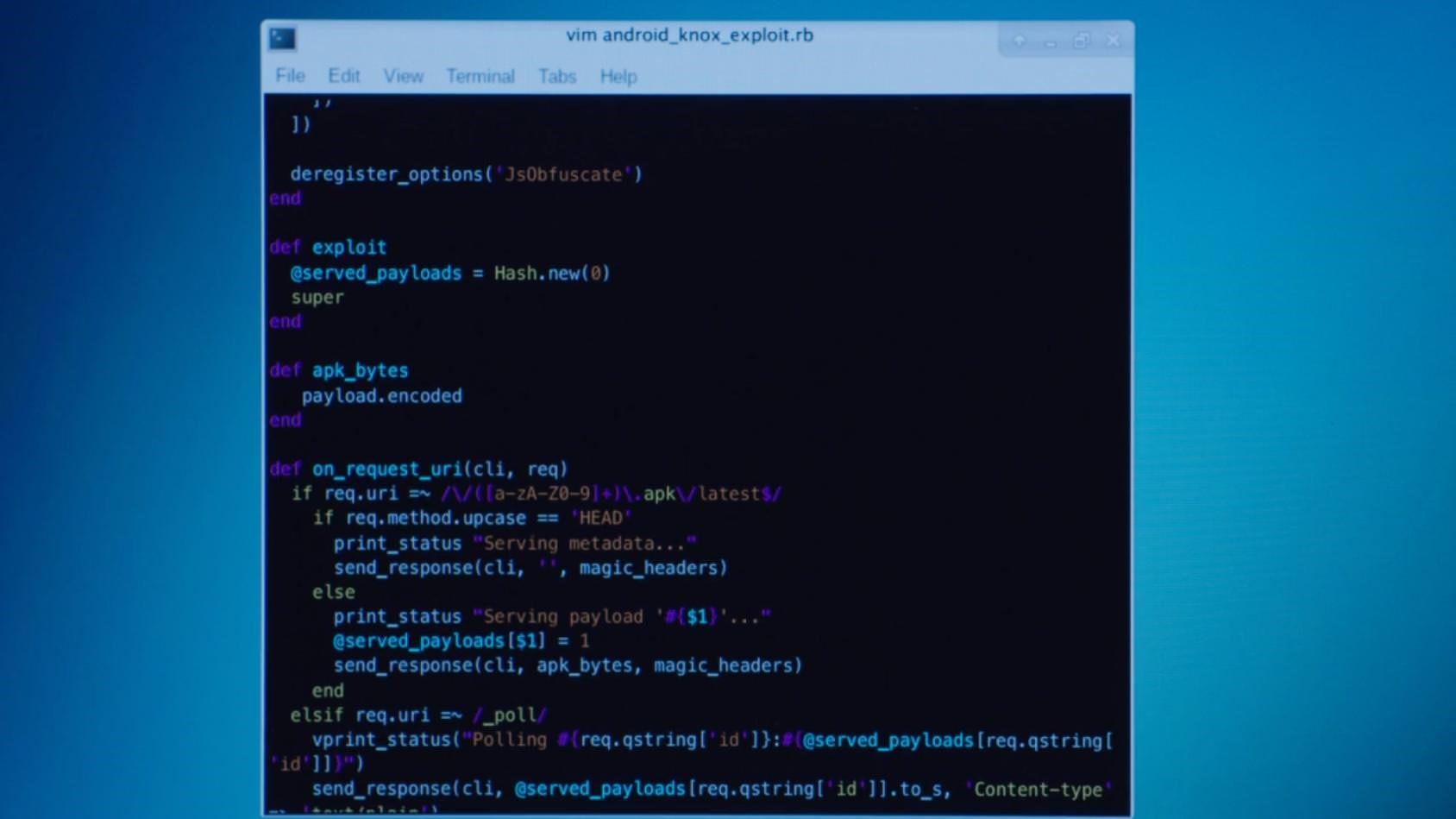
That's why it comes as no surprise that Tyrell is so methodical when it comes to planning the attack on E Corp's emergency generators. In one scene, we even see him using an application to design a network topology, allowing him to quickly identify where the weakest link is and how to exploit it.
When it comes to thinking defensively (as Elliot did in the previous episode), it's important to identify the weakest points in our networks and the systems we manage. Nowadays, with so many connected devices handling, and accessing crucial systems and data that also need to be patched to avoid someone exploiting their vulnerabilities, this task can become extremely complicated.
The difficulty in identifying the source of a cyberattack
During most of the second season, we believe that all the attacks carried out by Elliot, Darlene and the other members of fsociety were successful due to their own skills. However, in this episode we find out that, unbeknownst to them, they were helped by the Dark Army.
The infamous femtocell that Darlene provided Angela so that she could plant it on a floor full of federal agents and which was supposedly prepared by Cisco, Darlene's boyfriend(?), was really delivered to the Dark Army and then to Elliot for him to set up, although the Android malware was not his doing.
In addition, we also see how secondary characters, such as agent DiPierro's FBI boss, are also working for the Dark Army. The same goes for Leon, the colleague Elliot befriends in prison, who provides information about what he is doing while he's behind bars.
Since nothing is what is seems, it's hard to be sure who was really behind the attacks shown in the series. The world still believes fsociety was responsible (and they themselves do too, to an extent), but the truth is that there is a group in the shadows that is pulling all the strings.
Something similar happens in the real world when we hear about suspicions that this or that group connected with a certain country is responsible for a cyberattack. Who can say for sure that the portion of code proving their identity hasn't been planted there on purpose so that everyone points the finger at the enemy of the moment?
One curiosity is that this episode shows us how the Dark Army group also wants to influence the US election campaign of November 2016 (remember that the series timeline is still at the end of 2015). But we all know who ended up as President, don't we?
Easter eggs
Despite the fact that this episode didn't have much technical content, the team behind the series continues to surprise us and set up a highly original quiz among users signed up to the Mr. Robot mailing list, inviting them to take part in a new interactive story using Alexa, the Amazon virtual assistant.
Interacting with this virtual assistant, they had to provide the correct answers and, once the “challenge” was completed, successful participants were informed that they would be contacted again for new missions. Definitely a curious and fun way to delve further into the universe of Mr. Robot.
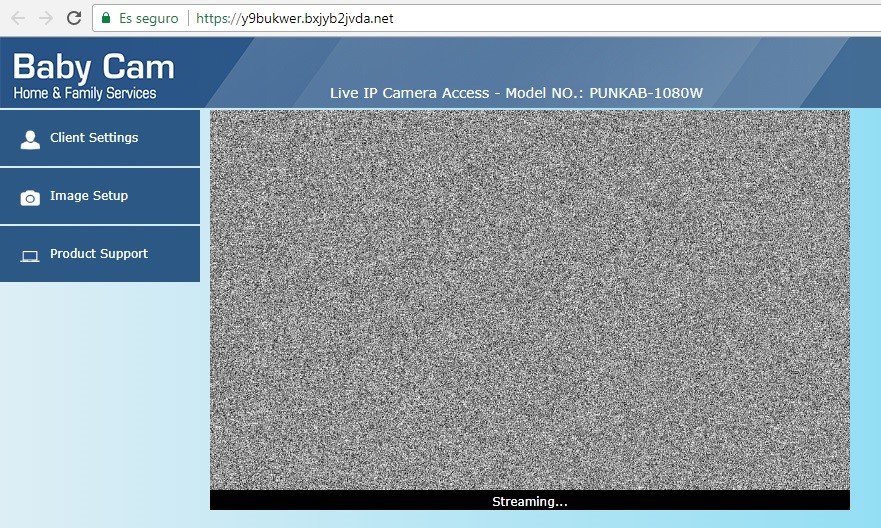
While Tyrell is preparing the attack on E Corp's emergency generators, we see him watching his son through a webcam. If we access the URL 192.251.68.238 that appears on the screen, we come to what appears to be a webcam streaming service like those used to monitor babies in their cribs. However, instead of seeing Tyrell's son, we see an image of static, although we're actually watching a looped GIF.
In the very last frame of this image, you can see a hexadecimal code hidden amongst the static. The same thing happens with other animations of static shown on the web, which, when translated into their corresponding characters, form the sentence "We're all mad here", a clear reference to Lewis Carroll’s Alice in Wonderland.
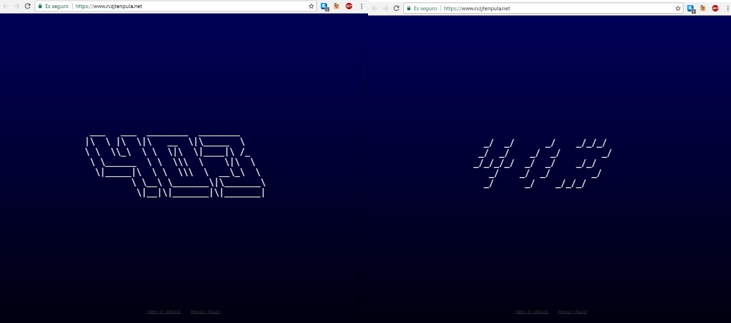
While Tyrell is preparing the femtocell, we see a weblink appear in the code (https://www.rvzjtenpula.net/). However, if we access this page, the only thing we see is an image showing error 403 (access denied). This image switches to another which is shown for an instant at random time intervals.
For now, we don't know the meaning of that Easter egg, but it may be revealed in future episodes.
Conclusion
This episode has served to fill an important gap in the story of a central character in the plot who was missing for much of the second season. It won't be the episode that teaches us the most about technical issues, but this type of episode is always useful for reviewing some of the things we may have overlooked and completing the pieces of the thrilling puzzle that is Mr. Robot, a series that has us all hooked.
Image credits: USA Network