This weekend it emerged that Pippa Middleton was the latest in a long line of celebrities to have her online accounts broken into by criminals, and private photographs stolen.
As The Daily Mail reports, a man who had allegedly broken into Pippa Middleton's iCloud account was offering 3,000 private photographs of the 33-year-old socialite including snaps of her at a wedding dress fitting, and naked photographs of her fiancé James Matthews.
Included in the haul, according to media reports, were private images of Pippa Middleton's sister, and her sister’s children, George and Charlotte.
Things become more serious when you remember that Pippa Middleton's sister is Kate Middleton, officially known as the Duchess of Cambridge, and wife of Prince William.
Fortunately even the British tabloid media appears to have baulked at the idea of publishing the stolen photographs, and it was no surprise to hear that police have made an arrest.
What is important to understand is that this, and many of the previous celebrity "hacks" that we have heard about in the past, did not probably occur because of some underlying security vulnerability in Apple's iCloud system.
Instead, my hunch is that Pippa Middleton's account was not following best security practices and had not properly secured her account.
My recommendation is that all iCloud users enable two-factor authentication on their accounts to increase the security on their Apple ID.
That way, even if your password is guessed (because you chose something obvious), grabbed (through perhaps a phishing attack or keylogging malware) or given away (maybe you made the mistake of reusing the same password on multiple websites), the hacker won't be able to break into your account without also having access to your smartphone.
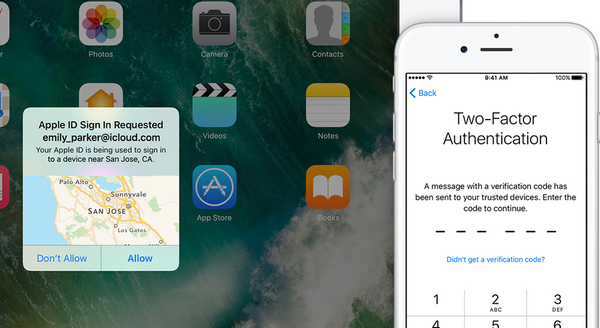
Here is how Apple describes the additional security measure of two-factor authentication:
With two-factor authentication, your account can only be accessed on devices you trust, like your iPhone, iPad, or Mac. When you want to sign in to a new device for the first time, you'll need to provide two pieces of information—your password and the six-digit verification code that's automatically displayed on your trusted devices. By entering the code, you're verifying that you trust the new device. For example, if you have an iPhone and are signing into your account for the first time on a newly purchased Mac, you'll be prompted to enter your password and the verification code that's automatically displayed on your iPhone.Because your password alone is no longer enough to access your account, two-factor authentication dramatically improves the security of your Apple ID and all the personal information you store with Apple.
Whenever you place sensitive information in the cloud you need to consider the worst case scenarios of what could happen if an unauthorised party was to gain access to the account. For the most sensitive information it might make sense to encrypt the data before you upload it to the internet, so even if your account is compromised all that the hackers will be able to do is download gobbledygook.
However, for some users in some scenarios, encrypting information before it is placed in the likes of iCloud may be a step too far. There is, however, no good reason why you wouldn't additionally protect your accounts with two-step verification or multi-factor authentication when a service makes it available to you.
It makes sense for your web email accounts, your file-sharing accounts and your social media accounts.
So, what are you waiting for?




