Ransomware is everywhere. At least that might be the impression left by a seemingly endless stream of news reports on recent cyberattacks. Well, there were several (good) reasons why criminals have made it all the way to the front page.
First, the targets they’ve chosen for their malevolent activities. Such as hospitals on both coasts of the US, which were unable to protect patient data. People’s lives and health being put at risk has forced some facilities to pay thousands of dollars to cybercriminals.
Applying a countdown timer - or other nasty tricks to trigger a quick ransom payment - has also gained ransomware additional media attention.
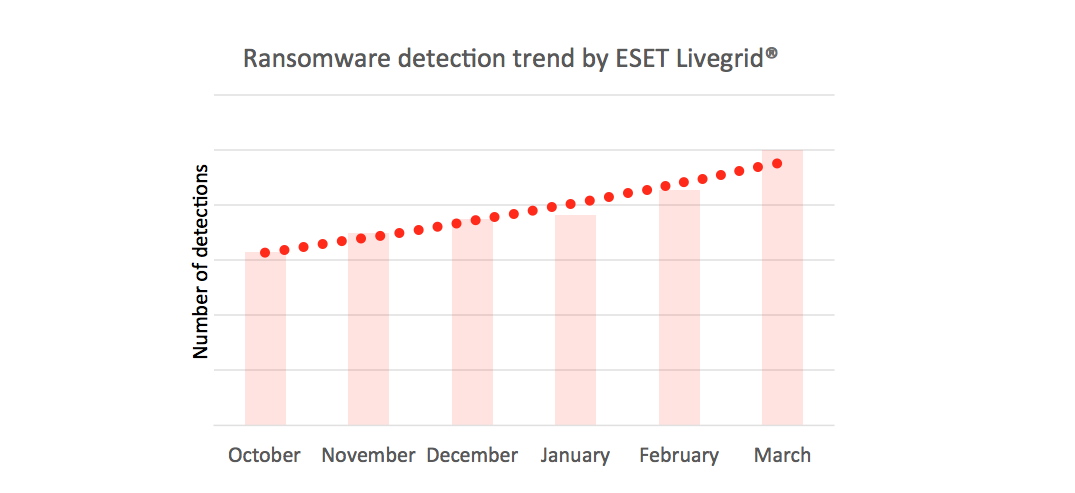
Other reasons for receiving widespread coverage has been the sheer volume of cybercriminal activity. Just a month ago ESET warned users about infected emails spreading ransomware and flooding inboxes all over the world.
Pretending to carry harmless file attachments, JS/TrojanDownloader.Nemucod was in fact trying to dupe victims into downloading and installing one or the other widely known ransomware families, such as TeslaCrypt or Locky.
It seems that this tactic was evaluated as effective by the criminals, as they subsequently tried their luck with multiple waves. They also used a wider pallet of extorting malware variants, such as CTBLocker or Filecoder.DG.
But not all ransomware is as dangerous as the families mentioned above. Many malware authors see a chance to profit from the trend and try to develop their own ransomware, often ending up with poor implementation that proves inadequate or easy to crack.
Luckily for users, this was also the case of two recent ransomware types – Petya and Jigsaw – which ESET analyzed. Both of them contained implementation flaws, which enabled the affected victims to get their files back and devices in order without paying a penny.
Booting up as a hostage
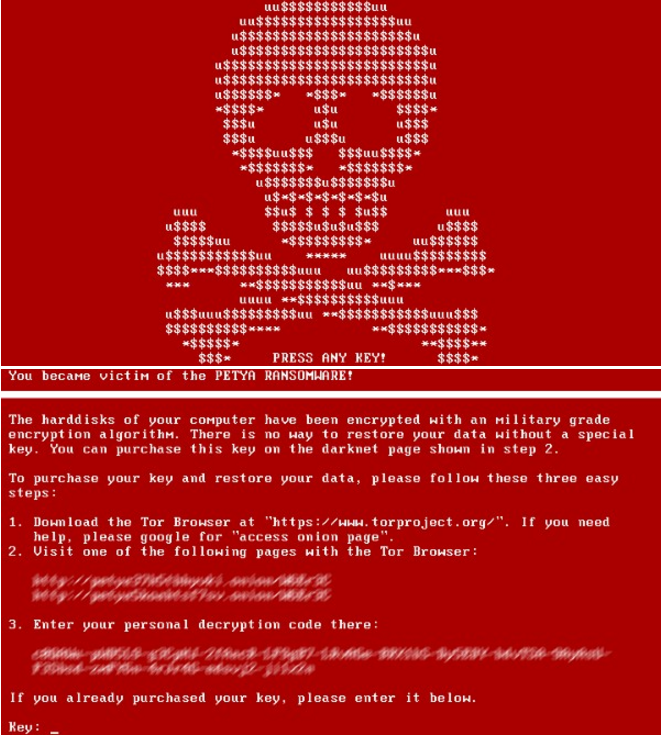
Petya, first announced by Trend Micro (Update 2022-08-14: this page is now offline; the link here points to the most recent version at archive.org), causes the “blue screen of death” after successful infiltration of Windows, thus forcing the victim to restart his/her machine. If the user does so, instead of loading the operating system he/she will only be displayed a ransom demand for 0.99 bitcoin ($431).
To accomplish this, it modifies the master boot record (MBR) to run the ransomware code instead of the system code. It then encrypts the master file table (MFT), which describes all files on the volume; by basically telling the system where the files are located and what the directory structure looks like.
Glitches in Petya
However, ESET analysis has shown, that Petya (despite the claim in the ransom message) is not encrypting the files themselves on the computer’s disks, only the file table. This (gap) allows users to recover files with some of the recovery tools available (although this might lead to some costs).
How does it spread?
To spread Petya, attackers have used emails disguised as résumés by potential employees. Yet, there is no document attached, only a link leading to a location on an (otherwise legitimate) online storage Dropbox.
If the victim clicks and downloads the file Bewerbungsmappe-gepackt.exe, instead of a resume, a self-extracting executable is downloaded to his machine unleashing Petya on the operating system. The subsequent naming of the file leads us to assume that this ransomware was aimed at users in German speaking countries.
At the time of writing, Dropbox had already removed the malicious file from several locations, but there is no guarantee that criminals won’t make additional changes and try their luck again. As of now, ESET is detecting two variants of this ransomware: Win32/Diskcoder.Petya.A and Win32/Diskcoder.Petya.B.
Meanwhile, there is also a free decryption tool available based on loopholes left in its structure allowing the user to recover the former master file table.
Ransomware that wants to play a game
Another ransomware family that piqued the interest of ESET researchers in recent days has been Jigsaw. Referring to the famous horror movie Saw, it tries to “play a game” with victims, by setting destructive rules.
If the user doesn't pay up within the first hour, the ransomware will delete one file. If the user doesn’t pay within the second hour, the number of destroyed files rises to two. With every additional hour, the number of deleted files grows exponentially, leading to an extensive data damage. Jigsaw also warns the victim that every attempt to restart the machine will be punished by deleting another 1000 files.
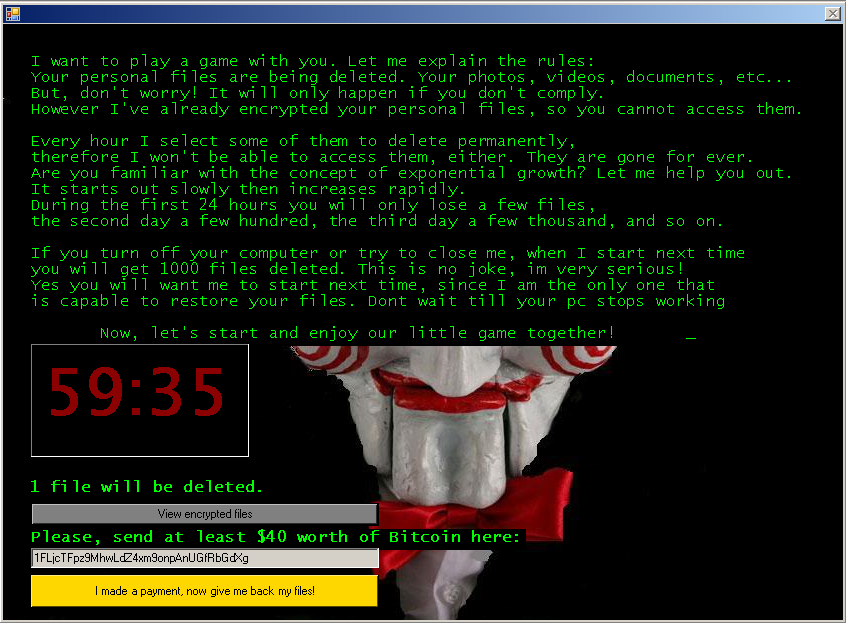
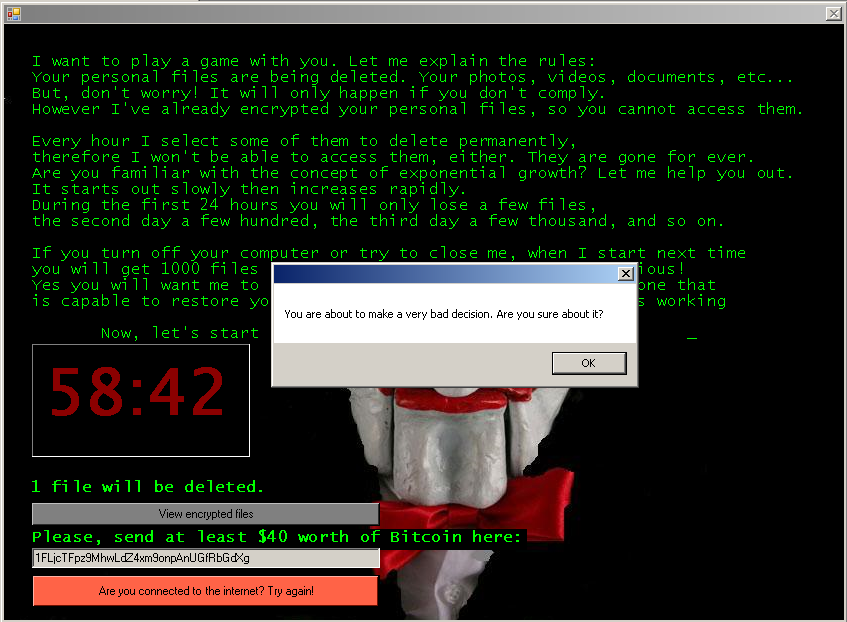
However, looking into the ransomware code, ESET researchers have found that Jigsaw is poorly implemented. It uses the same static key for all encryptions. At this point, there is already a decryption tool publicly available for users.
Also, in the past, there have been other ransomware variants which threatened to progressively delete victims’ files, but Jigsaw was the first one “in the wild” to actually use this approach. ESET detects the threat as MSIL/Filecoder.Jigsaw.A, MSIL/Filecoder.Jigsaw.B and MSIL/Filecoder.Jigsaw.C.
Locky copycat
A copycat detected by ESET telemetry as Win32/Filecoder.Autolocky.A, or Autolocky for short, is a good example of how malware writers are trying to feed off the “fame” of others, but often fail in the implementation phase.
Imitating the widespread and dangerous Locky ransomware, it uses the same extension for encrypted files (.locky). However, thanks to poor coding, the decryption key is sent only via Internet Explorer and can be easily tracked down in history directly on the infected machine. Autolocky victims are also lucky enough to have a decryption tool readily available, allowing them to get their files back.
As these recent examples show, users shouldn’t give in to ransomware scare tactics and should avoid paying the money demanded. There is a workaround or decryption tool for several of the extortion oriented malware families, restoring files safely and reliably, saving users money and cutting funding for future cybercrime.
Even though, some of the ransomware out there might be flawed or imperfect, cybercriminals are making their software better every passing day. Prevention is therefore essential to keep yourself safe from ransomware – even those of the lowest quality.
So, keep your operating system and software updated, use a reliable security suite with multiple layers of protection, and regularly backup all important and valuable data at an offline location (such as external storage). Be very careful when clicking on things in your email or browser. If you’ve received a message from an unknown source or it looks otherwise suspicious, delete it.




