Jean-Ian Boutin, a malware researcher at ESET since 2011, has successfully built up a reputation as an authority on banking trojans. His hard work in this area has so far culminated in a career-highlight study, The Evolution of Webinjects, which was presented at the 24th Virus Bulletin conference in Seattle last year.
Based in one of ESET’s research labs in Montreal, Canada, Mr. Boutin continues to investigate the growing complexity and sophistication of this threat, utilizing his expertize and experience to deliver insight into a menace that is more ubiquitous than ever before.
In an exclusive for WeLiveSecurity, Mr. Boutin, whose golden rule for cybersecurity is “be paranoid enough”, shares his thoughts on the past, present and future of banking trojans.
If you compare banking trojans today to the kind that were around five years ago, what would be the key differences?
A lot has changed. Today we see far more families [of banking trojans]; more creative ways of stealing; and new and refined functionalities, including form grabbing, webinjects, mobile components, proxy and remote desktop/VNC.
It is also far more difficult to obtain the configuration file these days. This usually contains vital information about targets and command and control servers.
One trend that is getting stronger as the years go by is the specialization of actors – malware authors – in several aspects of what is needed for a campaign. A botmaster can now buy online everything that is required to build a botnet: geolocated installs, webinjects, the banking trojan itself, and so on.
Are there, in relation to above, any new techniques that make banking trojans harder to detect both from a user point of view, as well as that of a vendor?
"It is a cat and mouse game. When new security measures are put in place, cybercriminals are always trying to evade them.
It is always a cat and mouse game. When new security measures are put in place, cybercriminals are always trying to evade them.
Are there new techniques used by banking trojans that makes their detection harder? The answer is yes, but, alongside that, security solutions have also evolved to counter them.
What’s the most interesting banking trojan you’ve come across during your time in the industry?

Banking trojans like Hesperbot are incredibly sophisticated
I will go with an emotional choice and choose Gataka because it was one of the first ones I analyzed when I started work as a malware researcher at ESET.
It was a banking trojan with a modular design that used a local proxy server to intercept network communications – this technique was different from the popular browser API hooking technique that other banking trojans use.
It was then reused by other banking trojans, including Hesperbot, an extremely effective type of malware.
Do cybercriminals have particular techniques for deploying banking trojans and are there any particular techniques that users should be most aware of?
Usually, the same means used to distribute other types of malware are used in banking trojans, including spam and drive-by downloads.
Besides keeping their software and plugins up-to-date, users should also use caution when clicking on links or opening attachments.
What are your tips for consumers who like to bank online but are worried about the threat of cybercrime?
Be cautious online and understand that exploit kits usually exploit old vulnerabilities so it is important to keep your software up-to-date.
With banking trojans, which are often distributed through spam, the same applies – be watchful before opening attachments or clicking on links found in emails.
Additionally, be vigilant for sudden changes in your online banking website, while for mobile, do not install Android applications from unknown sources.
It is usually the case that banking attacks happen on a client side (consumers) more than on server side. However, after all the leaks we’ve seen as of late, do you think banks, financial institutions and corporations will be more of a target?
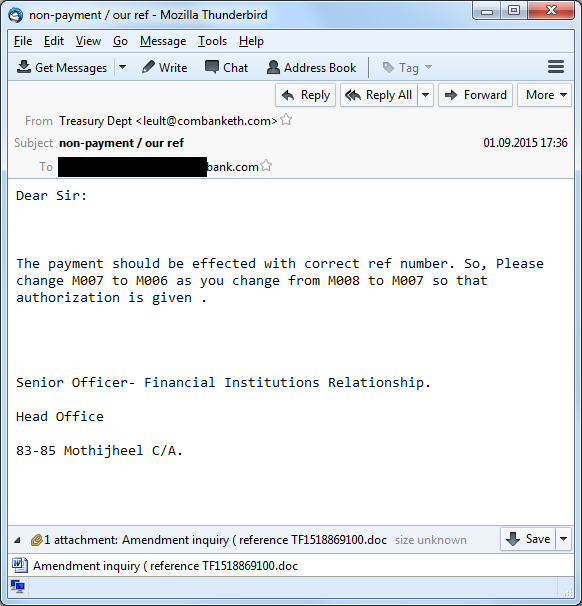
An example of a spear phishing email that was sent to a German bank by the Carbanak gang
What we have seen lately is that some criminal groups are now targeting financial institutions to try to steal money directly from them.
One very good example concerns the Carbanak gang, which was publicly documented in 2014, but is still active today and targeting different institutions around the world.
How do you expect banking trojans to evolve over the next few years?
"We will see more and more groups focusing their efforts on high-value targets."
I think we will see more and more groups focusing their efforts on high-value targets, a bit like what we saw for Carbanak or Buhtrap operations.
For banking trojans targeting individuals, we will see them targeting new ways used by people to perform online banking and payment.
There seems to be a lot of growing interest in virtual money. Do you expect digital currencies like bitcoin being attacked in even greater numbers?

Bitcoins are likely to be targeted more and more
We see mainly two types of malware interested in bitcoins: the first type steals resources from a system to perform mining and the second one tries to steal money from the user wallet.
As long as the bitcoin value, as well as other virtual currencies, will remain high, we will see a steady stream of attacks trying to achieve one of these two goals.
Is it easier to dupe someone with a so-called Bitcoin wallet, where the value is for now “digital”, or someone with a banking account, where the value is “more real”?
I believe it might be a little bit easier to steal a Bitcoin wallet as the safeguards to keep the wallet safe are usually on the user’s shoulders as opposed to the bank’s.
The banks, as they usually have to repay stolen funds, have a good incentive to protect their users against these.
As someone with a lot of insight into banking trojans, what’s your general assessment of this type of malware?
Although this type of malware is very old, it is still successful. We have seen, for example, a lot of changes in banking trojans to adapt to the different security measures put forth by financial institutions.
The battle is certainly not over and it is clear that we will have to protect our users against this type of malware for a long time to come.





