Moonpig, the online personalised card company, has been accused of a shockingly sloppy attitude to security, after apparently leaving a serious hole in its security unpatched.
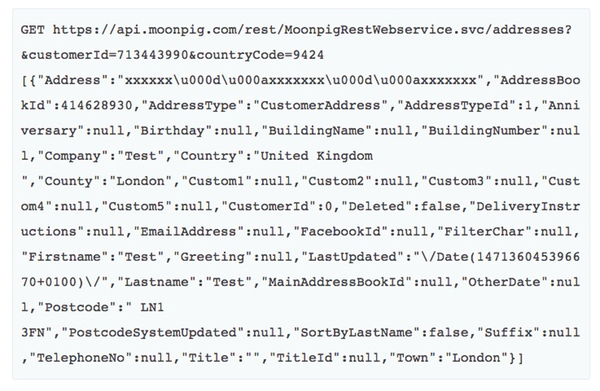
The vulnerability, which was said to have been first reported to Moonpig back in August 2013 (yes, 2013) allows anyone with a modicum of programming knowledge to access the names, dates of birth, email and home addresses of the company's 3.6 million customers.
All that it takes is to change the Customer ID number sent in an API request. No authentication is required.
Developer Paul Price discovered the serious security hole back in August 2013 (yes, 2013) and told Moonpig about the problem. Frustrated by the company's lack of response after some 17 months, Price has now gone public.
In Price's tests he discovered that the API calls were not rate-limited, meaning that in theory it appears it would be possible to work your way through every variation of the Customer ID and eventually access the personal details for all of Moonpig's users.
News of the flaw quickly spread on Twitter last night to such an extent that "Moonpig" was trending in London.
Sadly Moonpig's UK branch appeared to be oblivious to furore, telling followers it had settled down with a nice cup of tea to watch the latest series of David Tennant detective drama "Broadchurch":
Price, who says he responsibly disclosed the vulnerability to Moonpig on 18 August 2013 and again a year later on 26 September 2014, is clearly unimpressed:
"I've seen some half-arsed security messures in my time but this just takes the biscuit. Whoever architected this system needs to beshotwaterboarded."
Clearly, Moonpig's system was not built with security in mind. That's very bad, as its databases contains sensitive information and it could clearly be easily abused by online criminals and fraudsters.
But what I find worse is Moonpig's failure to adequately respond when it has been given such a long time to do so.
Personally, I would have preferred it if Price had taken his findings to a security journalist rather than made details of the vulnerability public, and the media could have applied pressure on Moonpig to resolve the issue.
However, after waiting 17 months, I can certainly understand the frustration felt by someone who has tried to get the problem fixed and found a company that clearly wasn't listening.
At the time of writing, Moonpig appears to have shut down access to its offending API. However, it hasn't as yet made any public response on its Twitter account. Maybe it's still reeling from the events of the episode of "Broadchurch" it was watching...




