If you've been messing around with technology for a while, you may remember the good old days of acoustic couplers, ZModem, and Bulletin Board Systems (BBSes).
These were the days before the worldwide web had taken off, when even the slowest broadband speeds would have been sheer fantasy.
And because getting an online connection was slow and sometimes flakey, it wasn't at all uncommon for techies to compress their programs and downloadable files into tight little packages, to make the download as painless as possible for users. The most famous compression tool of all was PKZip, created by the late Phil Katz, and versions of the .ZIP file format are still widely used today in some circles.
But there were other data compression tools which competed for .ZIP's crown, each with their own loyal bands of followers. And one of the most famous was .ARJ.
And, to be honest, ARJ was pretty cool.
So you can imagine my delight when I discovered today that .ARJ wasn't entirely forgotten and consigned to the dusty annals of history. Instead, it is still being used - albeit by malware authors...
Here is an example of a typical malicious email, spammed out by online criminals:
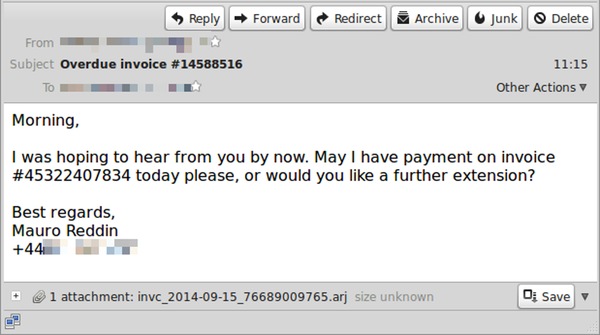
Subject: Overdue invoice #14588516
Attached file: invc_2014-09-15_7689099765.arjMorning,
I was hoping to hear from you by now. May I have payment on invoice #45322407834 today please, or would you like a further extension?
Best regards,
Mauro Reddin
Of course, the social engineering might have been a little better thought out. For instance, the invoice numbers quoted in the email don't match each other.
But it's easy to imagine how many users might be alarmed to hear that it is being suggested that they are being accused of a late payment, and would click on the attached .ARJ file without thinking of the possible consequences.
At that point the .ARJ file will decompress, spilling out its contents.
As Conrad Longmoore explains on the Dynamoo blog, inside the .ARJ archive file is an executable program - designed to infect your Windows computer.
Before you know it, your Windows PC could have been hijacked by a hacker and recruited into a botnet. Whereupon the remote attacker could command it to send spam on their behalf, launch denial-of-service attacks or steal your personal information.
That's why you should always be wary of opening unsolicited files sent to you out of the blue via email.
The good news for users of ESET anti-virus products is that it is detected as a variant of Win32/Injector.BLWX. But if you are using a different vendor's security product you may wish to double-check that it has been updated to protect against the threat.




