In September we informed about a new banking trojan called Hesperbot (detected as Win32/Spy.Hesperbot). The perpetrators responsible for the threat are still active – November has been particularly eventful. In this post, we’ll give an update on the situation and malware developments.
New targets: Germany and Australia
The geographic distribution of Hesperbot infections has been fairly localized to a handful of specific countries, which is partly due to the fact that fraudulent emails posing as originating from a local trustworthy institution (e.g., postal service or ISP) is the primary infection vector.
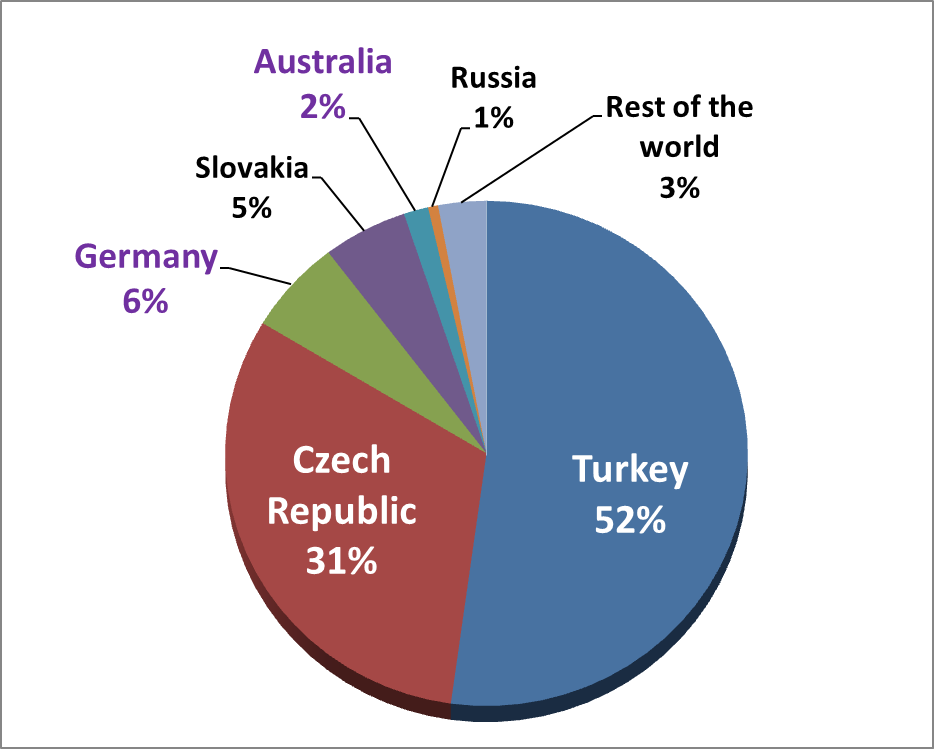
As suspected, it didn’t take long before attackers started using the malware to target online banking users in more countries. In addition to the initial four country-specific botnets (Turkey, the Czech Republic, Portugal and the United Kingdom), in November we discovered new Hesperbot versions targeting Germany and Australia.
Meanwhile, large infection waves continued in the Czech Republic and web-injection scripts (which were previously absent) were added to the configuration files for the Czech botnet. The ESET LiveGrid® pie-chart below shows Hesperbot detections per country in November.
Configuration files – targeted banks
The modular architecture and modus operandi of the threat remain unchanged. The supplied configuration file determines which URLs the form grabber should ignore (all other HTTPS POST requests are captured – with the intention to harvest online banking login credentials), the URLs that should trigger video-capturing (both as a means of overcoming virtual keyboards, and also a quick way for the botnet operator to see the victim’s account balance without having to log in) and defines web-injections in a similar format to Zeus or SpyEye.
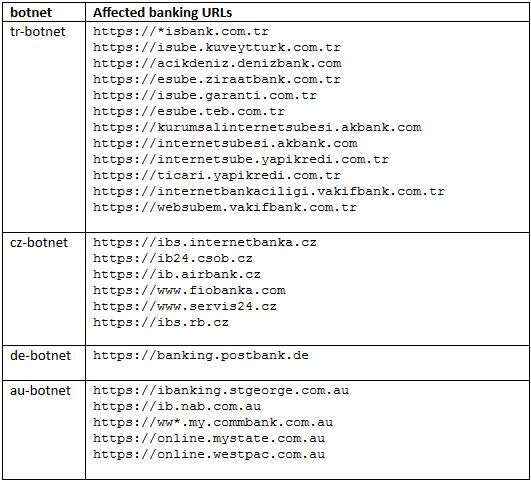
The table below shows affected online banking URLs from the most recent configuration files.
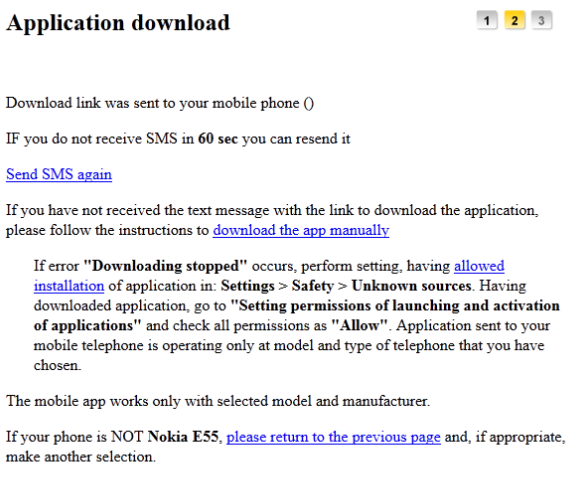
The actual injected web-forms, through which the attackers try to lure the victim into installing the mobile component look like this:
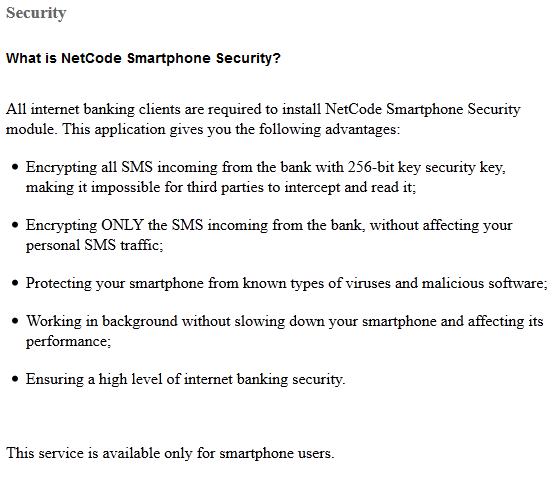
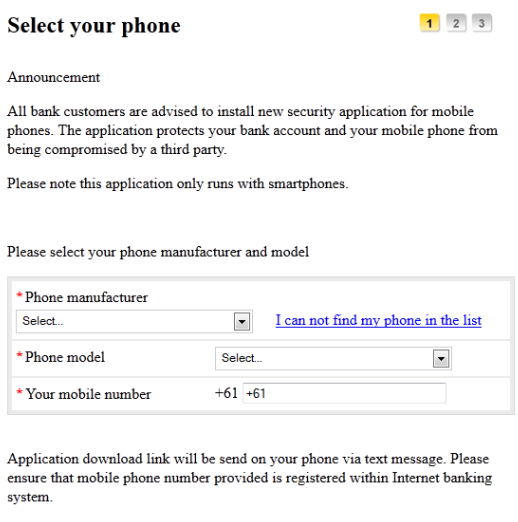
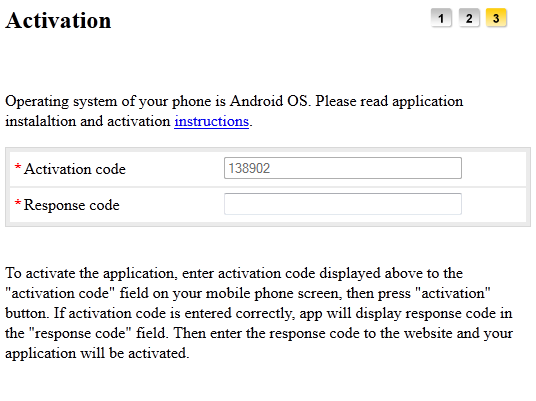
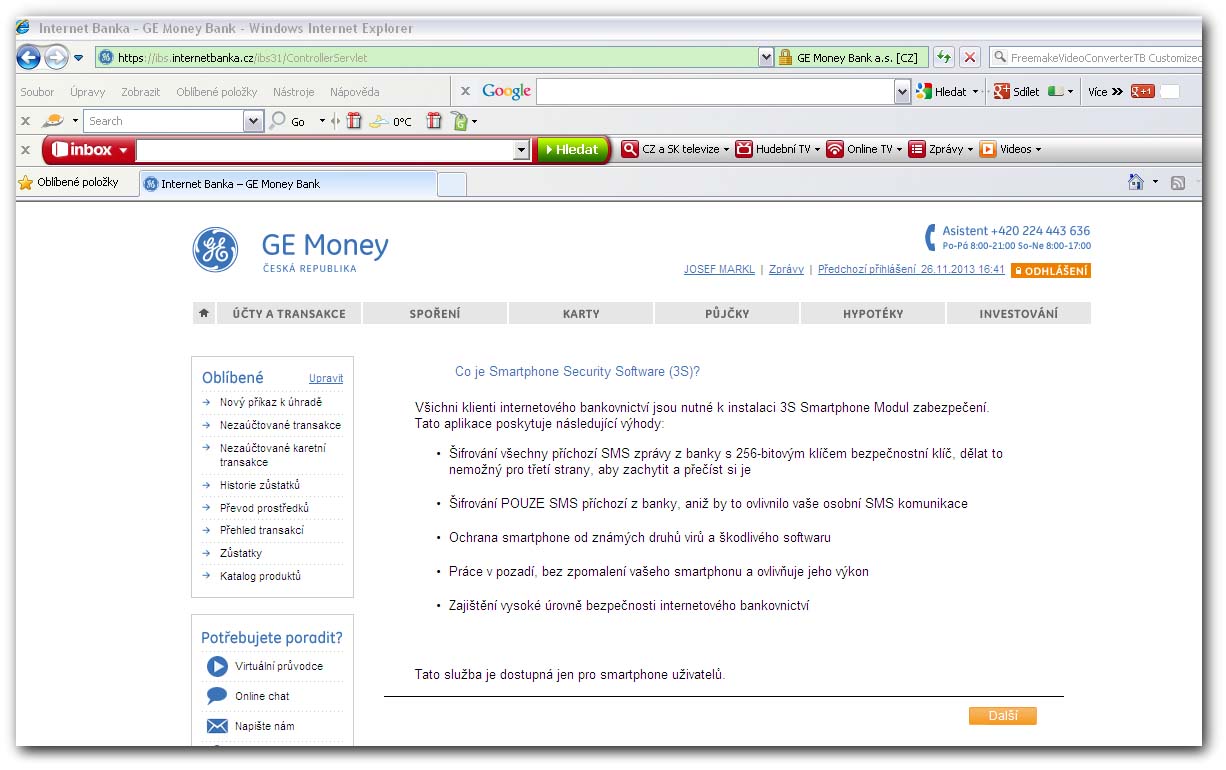
Note that the above screenshots are without all CSS formatting, which is specific to each bank’s website. Below is a real case of seamless web-injection in a Czech bank’s site:
Hesperbot’s man-in-the-browser technique ensures that the HTTPS connection appears secure. For details on how this is accomplished, see our previous analysis.
New Bitcoin and process-blocking modules
In our previous technical blog posts (part 1 and part 2) we described the individual Hesperbot modules and their functionality. The latest version of the trojan now uses two new modules.
The first one, gbitcoin, attempts to steal the following files and send them to the remote C&C server:
-
%APPDATA%\Bitcoin\wallet.dat
-
%APPDATA%\MultiBit\multibit.wallet
These files represent Bitcoin wallets that store private keys for the original Bitcoin client and the MultiBit client, respectively. With the current high value of Bitcoin, the decision to add this module is quite understandable. Some advice on how to keep your Bitcoins safe can be found on WeLiveSecurity and on the official Bitcoin wiki.
The second module is perhaps more interesting. Its actions are determined by the Hesperbot configuration file. If corresponding entries are present, the module can:
- Suspend all threads in a specified process and then disable and hide all its visible windows
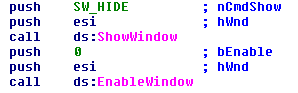
- Display a specified message using the MessageBox function.
- Block network communication by hooking the recv, WSARecv, send, WSASend functions from the WS2_32.dll library for a period of time.
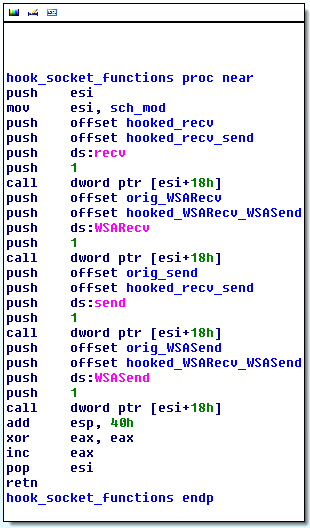
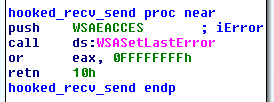
The hooked functions merely return the WSAEACCESS error. Notice that to apply the hooks, Hesperbot uses the auxiliary sch_mod module.
Until now, we haven’t spotted configuration files, which would make use of this new functionality. However, a possible purpose is to block standalone banking applications, as the trojan wouldn’t be able to take control over them. This way, the user would be forced to use his (infected) web-browser.
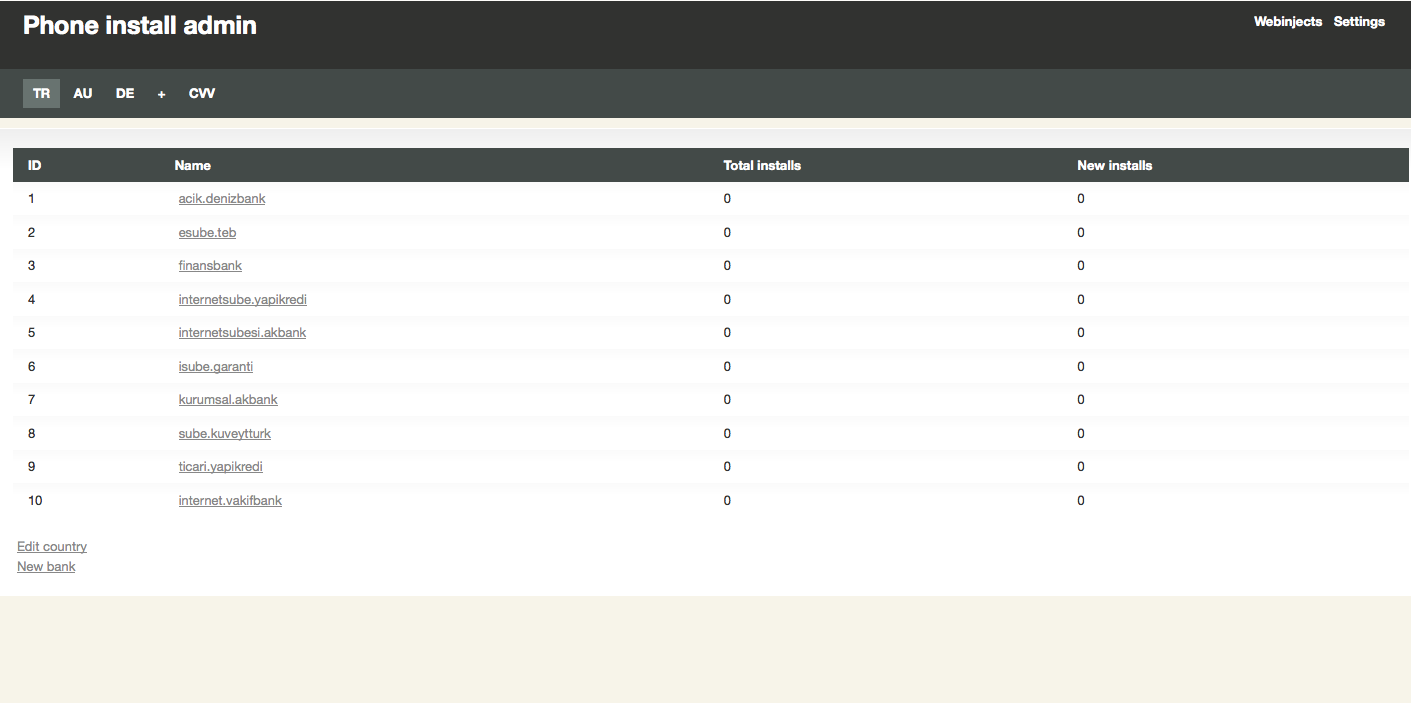
Botnet admin panel
We also managed to get a look at a Hesperbot C&C panel:
This screen shows different banks targeted in a particular country and the number of successful installations of the mobile component. As previously mentioned, the attacker lures victims into installing the SMS-forwarding mobile component through web-injects injected into the bank’s website.
Notice that this admin panel shows Turkish, Australian and German botnets.
The Hesperbot operators are very active, causing real financial losses for bank’s customers and it seems we still haven’t heard the last of this malware. We continue monitoring the threat and will keep you informed of further developments.
Authors:
Anton Cherepanov
Robert Lipovsky
List of SHA1s
dropper (DE-BOTNET) 04bbb39578d3fa76cab5c16367b9abe1c1a01106
dropper (AU-BOTNET) 3195768f3647b9ee99acc6dd484b997e4661b102
dropper (AU-BOTNET) 0563e9960abb703f72368fdf8ad8fcf641574898
gbitcoin_mod_x64.mod e1f7a1bb5e4991ca6c77f8fcb2a63df1ab84983c
gbitcoin_mod_x86.mod 43667df9e811863a5456a16b6bfd8ad59f7ff18c
procblock_mod_x64.mod daefe673cd1e7625831b3365602918b33b05dbe0
procblock_mod_x86.mod b1a2603c1850a07ea2f26780ea166ff69c0b39ad