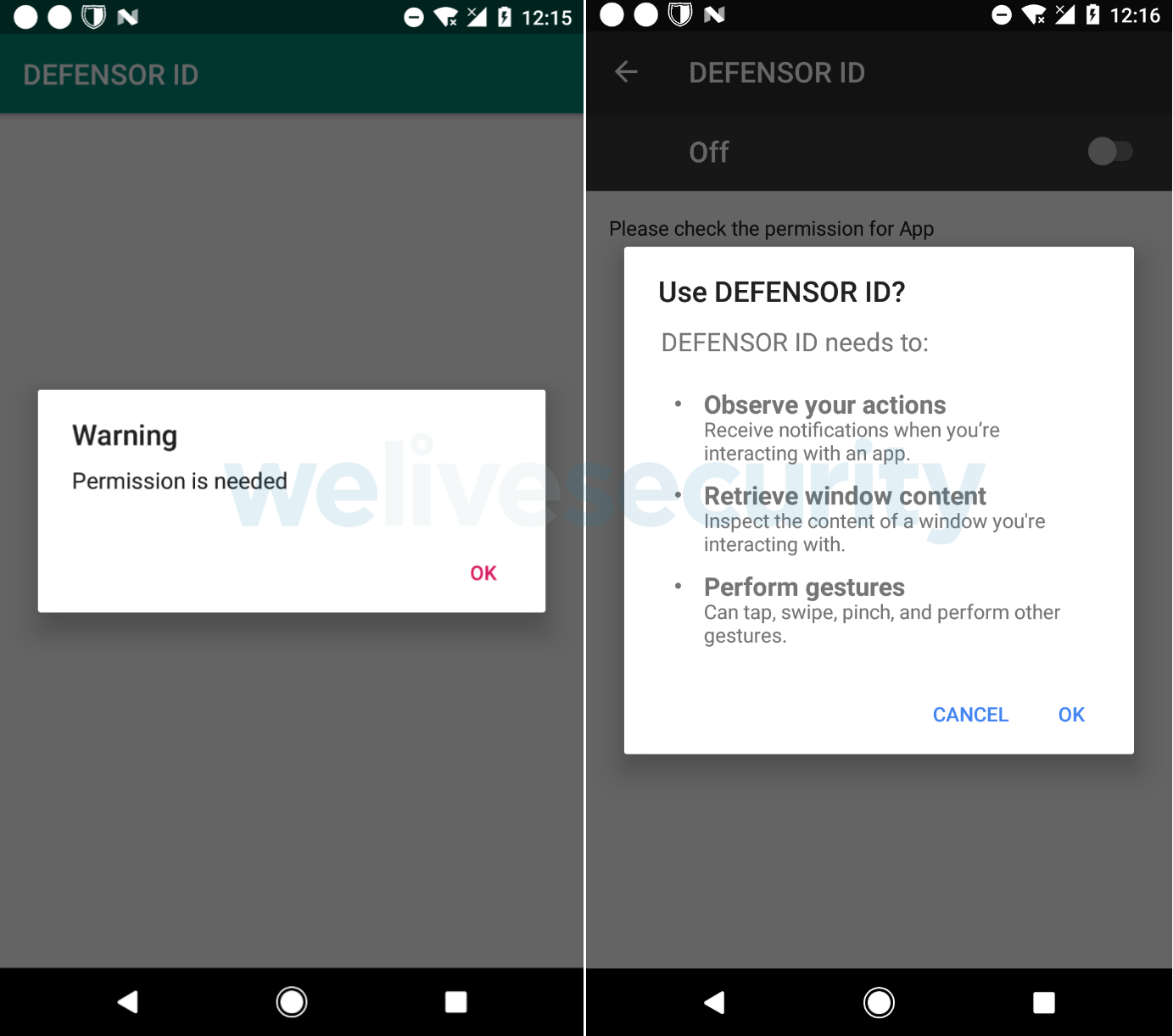
ESET researchers have analyzed an extremely dangerous Android app that can perform a host of nefarious actions, notably wiping out the victim’s bank account or cryptocurrency wallet and taking over their email or social media accounts. Called "DEFENSOR ID", the banking trojan was available on Google Play at the time of the analysis. The app is fitted with standard information-stealing capabilities; however, this banker is exceptionally insidious in that after installation it requires a single action from the victim – enable Android's Accessibility Service – to fully unleash the app's malicious functionality.
The DEFENSOR ID app made it onto the heavily guarded Google Play store thanks to its extreme stealth. Its creators reduced the app’s malicious surface to the bare minimum by removing all potentially malicious functionalities but one: abusing Accessibility Service.
Accessibility Service is long known to be the Achilles’ heel of the Android operating system. Security solutions can detect it in countless combinations with other suspicious permissions and functions, or malicious functionalities – but when faced with no additional functionality nor permission, all failed to trigger any alarm on DEFENSOR ID.
By “all” we mean all security mechanisms guarding the official Android app store (including the detection engines of the members of the App Defense Alliance) and all security vendors participating in the VirusTotal program (see Figure 1).
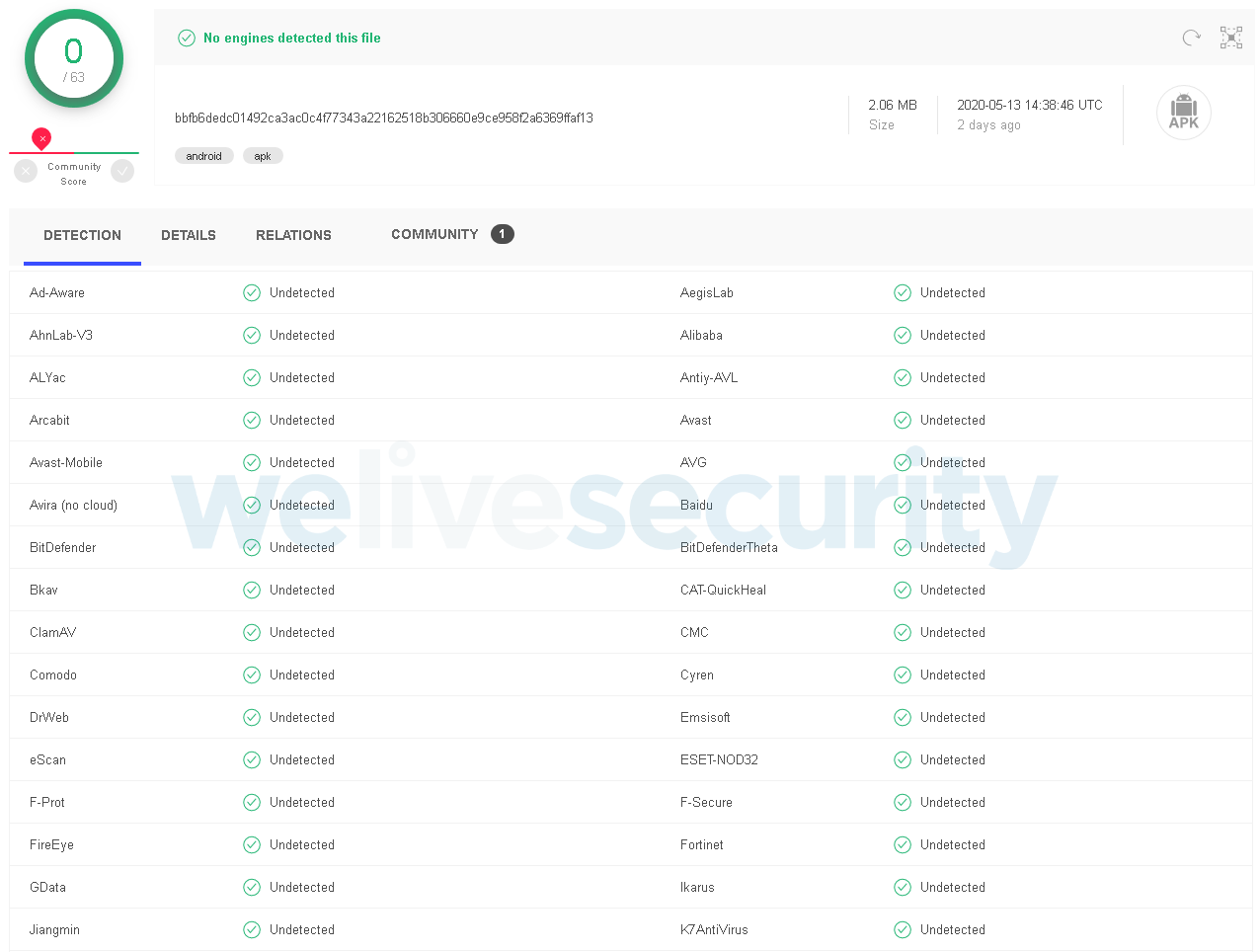
Figure 1. According to the VirusTotal service, no security vendor detected the DEFENSOR ID app until it was pulled off the Play store
DEFENSOR ID was released on Feb 3, 2020 and last updated to v1.4 on May 6, 2020. The latest version is analyzed here; we weren’t able to determine if the earlier versions were also malicious. According to its profile at Google Play (see Figure 2) the app reached a mere 10+ downloads. We reported it to Google on May 16, 2020 and since May 19, 2020 the app has no longer been available on Google Play.
The developer name used, GAS Brazil, suggests the criminals behind the app targeted Brazilian users. Apart from including the country’s name, the app’s name is probably intended to imply a relationship with the antifraud solution named GAS Tecnologia. That security software is commonly installed on computers in Brazil as several banks require it to log into their online banking. However, there is also an English version of the DEFENSOR ID app (see Figure 3) besides the Portuguese one, and that app has neither geographical nor language restrictions.
Playing further off the suggested GAS Tecnologia link, the app promises better security for its users. The description in Portuguese promises more protection for the user’s applications, including end-to-end encryption. Deceptively, the app was listed in the Education section.
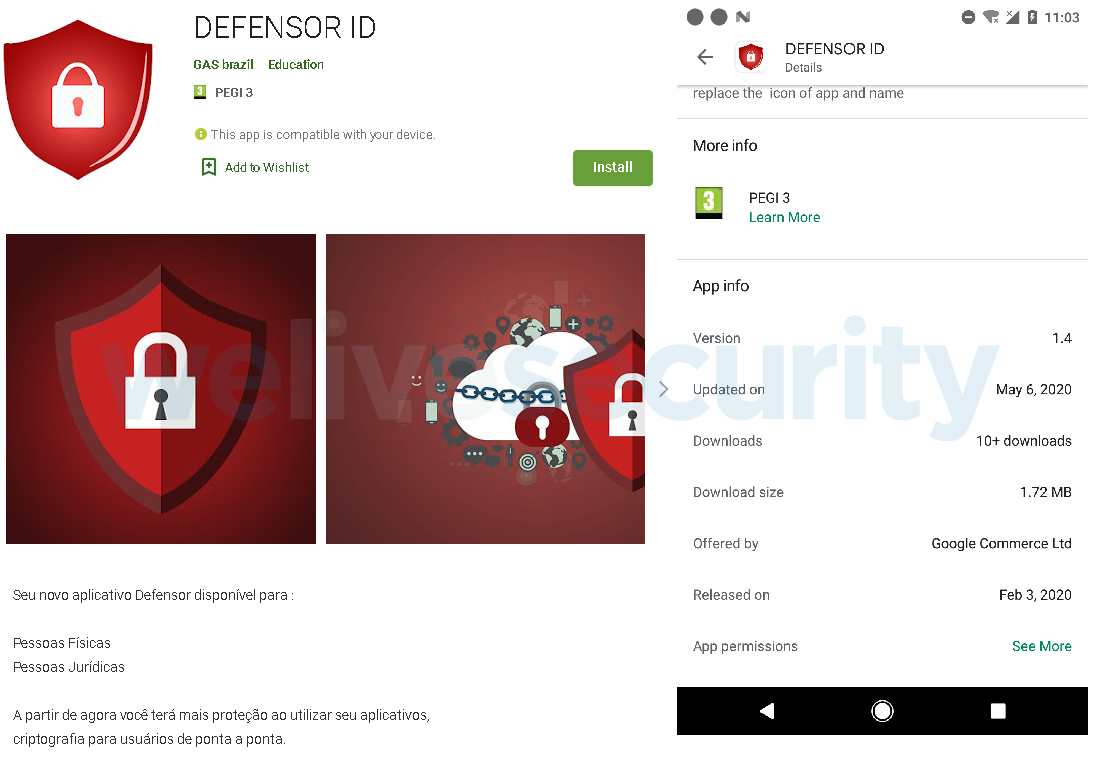
Figure 2. The DEFENSOR ID app on Google Play – Portuguese version (translates roughly as: “Your new Defensor app available for: / Individuals / Legal entities / From now on you will have more protection when using your applications, encryption for end-to-end users”)
Functionality
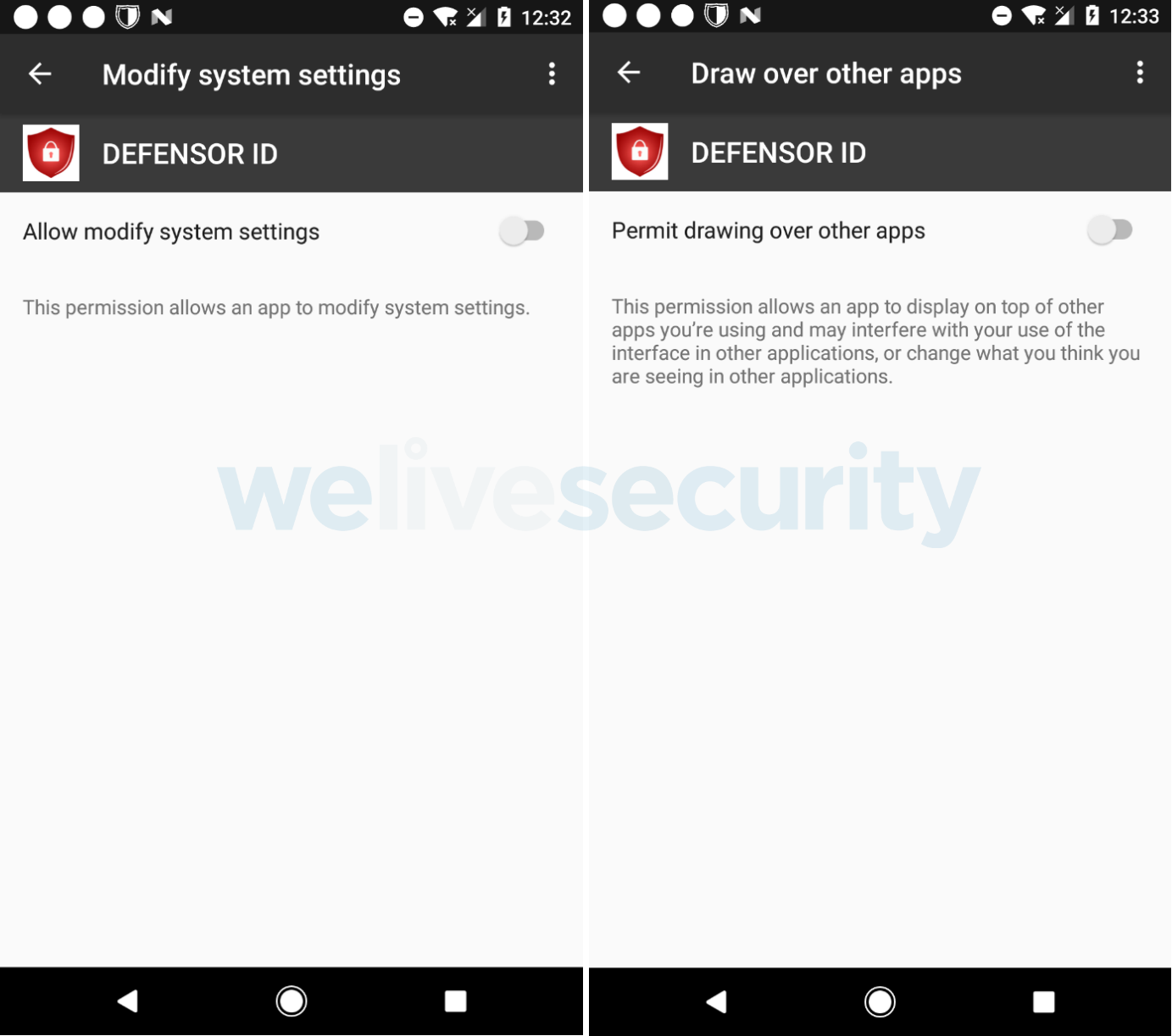
After starting, DEFENSOR ID requests the following permissions:
- allow modify system settings
- permit drawing over other apps, and
- activate accessibility services.
If an unsuspecting user grants these permissions (see Figure 4), the trojan can read any text displayed in any app the user may launch – and send it to the attackers. This means the attackers can steal the victim’s credentials for logging into apps, SMS and email messages, displayed cryptocurrency private keys, and even software-generated 2FA codes.
The fact the trojan can steal both the victim’s credentials and also can control their SMS messages and generated 2FA codes means DEFENSOR ID’s operators can bypass two-factor authentication. This opens the door to, for example, fully controlling the victim’s bank account.
To make sure the trojan survives a device restart, it abuses already activated accessibility services that will launch the trojan right after start.
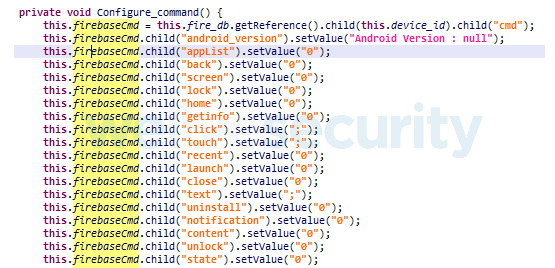
Our analysis shows the DEFENSOR ID trojan can execute 17 commands received from the attacker-controlled server such as uninstalling an app, launching an app and then performing any click/tap action controlled remotely by the attacker (see Figure 5).
In 2018, we saw similar behavior, but all the click actions were hardcoded and suited only for the app of the attacker’s choice. In this case, the attacker can get the list of all installed apps and then remotely launch the victim’s app of their choice to either steal credentials or perform malicious actions (e.g. send funds via a wire transfer).
We believe that this is the reason the DEFENSOR ID trojan requests the user to allow “Modify system settings”. Subsequently, the malware will change the screen off time-out to 10 minutes. This means that, unless victims lock their devices via the hardware button, the timer provides plenty of time for the malware to remotely perform malicious, in-app operations.
If the device gets locked, the malware can’t unlock it.
Malware data leak
When we analyzed the sample, we realized that the malware operators left the remote database with some of the victims’ data freely accessible, without any authentication. The database contained the last activity performed on around 60 compromised devices. We found no other information stolen from the victims to be accessible.
Thanks to this data leak, we were able to confirm that the malware really worked as designed: the attacker had access to the victims’ entered credentials, displayed or written emails and messages, etc.
Once we reached the non-secured database, we were able to directly observe the app’s malicious behavior. To illustrate the level of threat the DEFENSOR ID app posed, we performed three tests.
First, we launched a banking app and entered the credentials there. The credentials were immediately available in the leaky database – see Figure 6.
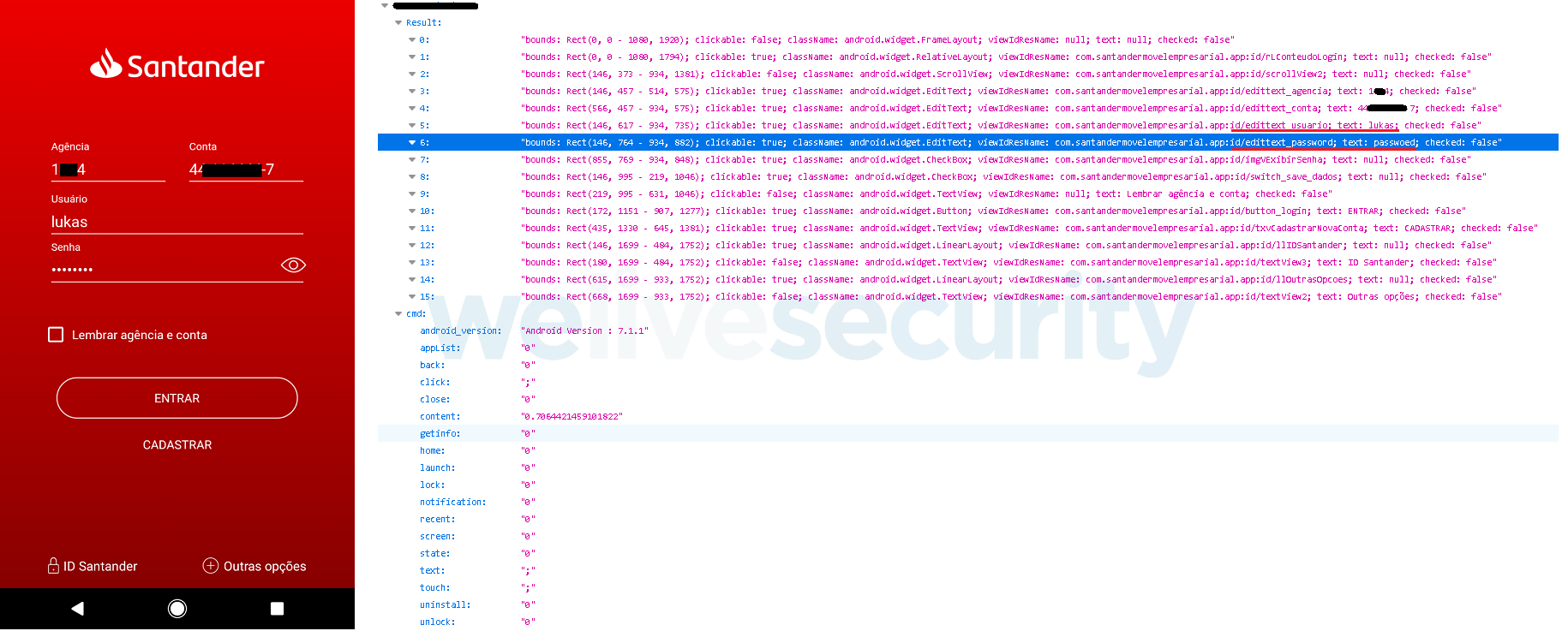
Figure 6. The banking app test: the credentials as entered (left) and as available in the database (right)
Second, we wrote a test message in an email client. We saw the message uploaded to the attackers’ server within a second – see Figure 7.

Figure 7. The email message test: the message as written (left) and as available in the database (right)
Third, we documented the trojan retrieving the Google Authenticator 2FA code.

Figure 8. The software generated 2FA code as it appeared on the device’s display (left) and as available in the database (right)
Along with the malicious DEFENSOR ID app, another malicious app named Defensor Digital was discovered. Both apps shared the same C&C server, but we couldn’t investigate the latter as it had already been removed from the Google Play store.
Indicators of Compromise (IoCs)
| Package Name | Hash | ESET detection name |
|---|---|---|
| com.secure.protect.world | F17AEBC741957AA21CFE7C7D7BAEC0900E863F61 | Android/Spy.BanBra.A |
| com.brazil.android.free | EA069A5C96DC1DB0715923EB68192FD325F3D3CE | Android/Spy.BanBra.A |
MITRE ATT&CK techniques
| Tactic | ID | Name | Description |
|---|---|---|---|
| Initial Access | T1475 | Deliver Malicious App via Authorized App Store | Impersonates security app on Google Play. |
| T1444 | Masquerade as Legitimate Application | Impersonates legitimate GAS Tecnologia application. | |
| Discovery | T1418 | Application Discovery | Sends list of installed apps on device. |
| Impact | T1516 | Input Injection | Can enter text and perform clicks on behalf of user. |
| Collection | T1417 | Input Capture | Records user input data. |
| Command and Control | T1437 | Standard Application Layer Protocol | Uses Firebase Cloud Messaging for C&C. |