ESET researchers have observed an increased number of apps on Google Play using social engineering techniques to boost their ratings, ranging from legitimate apps, through adware to malware.
Among these falsely high-ranking apps, an aggressive ad-displaying trojan was spotted, installed by up to 5,000 users as a tool to download content from YouTube. The app, detected by ESET as Android/Hiddad.BZ, uses a number of deceptive methods to trick users into installing its intrusive ad-displaying component and, at the same time, secure a good rating in the store.
To achieve the latter, the app innovates the good old-fashioned method of begging for high ratings through nag screens – it displays aggressive ads and makes a false promise of removing them in exchange for a five star rating.
Such incentives for rating are, however, inherently false promises, as there is no way for developers to connect users to specific reviews and thus no way to “reward” the ones that leave five stars. On top of that, reward or no reward, apps that promise users anything in exchange for high ratings are against the Google Play Developer Policy.
More false promises on Google Play
Similar deceptive techniques have recently been used in a number of ad-displaying apps on Google Play with a total of up to 800,000 installs, as found in ESET’s recent research.
These apps “force” users into leaving high ratings under various pretenses, which in turn makes them more likely to be downloaded in the future. What they have in common is a usually non-existent functionality; pop-up screens requesting five star rating to proceed, unblock full content or remove ads; and an illogically high rating.
A prime example of this is the fake game Subway Sonic Surf Jump, which requires users to rate it with five stars in order to proceed to the fictitious game, while displaying ad after ad. This leaves the app, installed by up to 500,000 users, with a 4.1 average rating and an ambiguous mix of five star ratings followed by angry “only-because-I’m-forced-to” reviews.
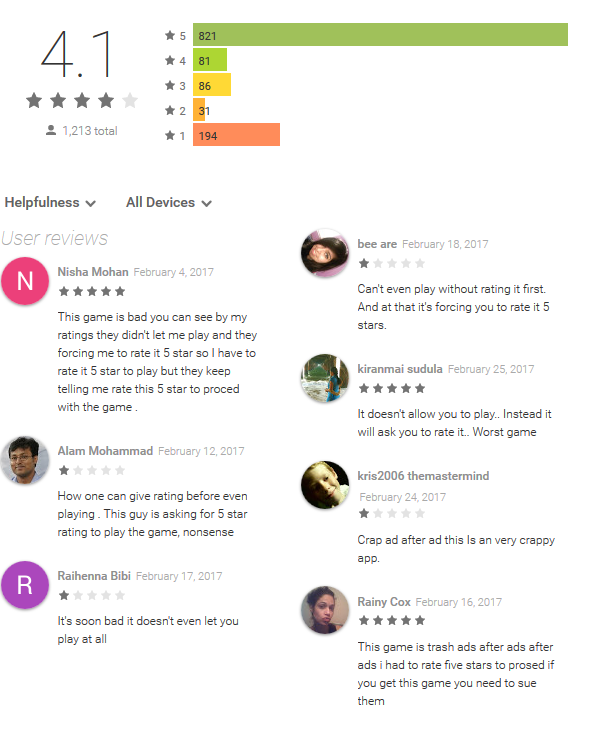
Figure 1 – Ambiguous reviews for Subway Sonic Surf Jump
Similarly, widely popular applications – at least according to their average rating – Anime Wallpapers HD and Latest online movies try to trade functions they have no intention of providing for five stars. Just like with Subway Sonic Surf Jump, this becomes apparent when one reads into the reviews of frustrated users.
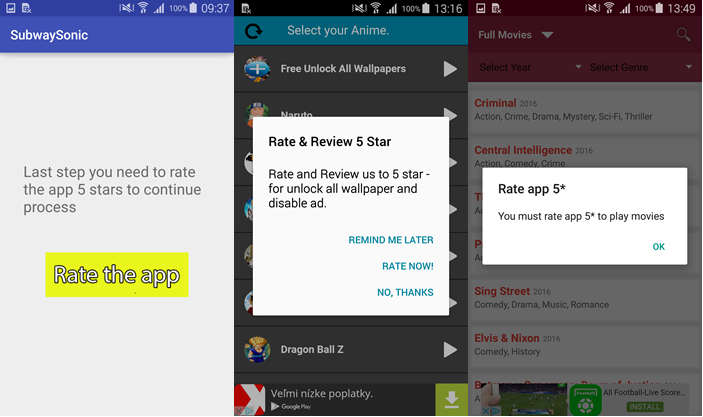
Figure 2 – Screens requesting five star rating in exchange for functionality
In some cases of incentivized rating, found mostly in real but somewhat shady games, developers simply reward all those who click OK/RATE APP on the nag screen. However, that doesn’t apply to the apps analyzed in this article, which are entirely fake and don’t deliver their promises regardless of what the user does.
Analysis of Android/Hiddad.BZ
The threat detected as Android/Hiddad.BZ was found on Google Play in seven versions, each named as a slightly different variation of “Tube.Mate” and “Snaptube”. Once installed, all seven applications appear as “Music Mania” under the user’s apps.
They work in the same way too: their functionality of downloading content from YouTube is combined with one of a dropper. The apps were reported by ESET on February 27th and consequently pulled from the store.

Figure 3 – The trojans on Google Play
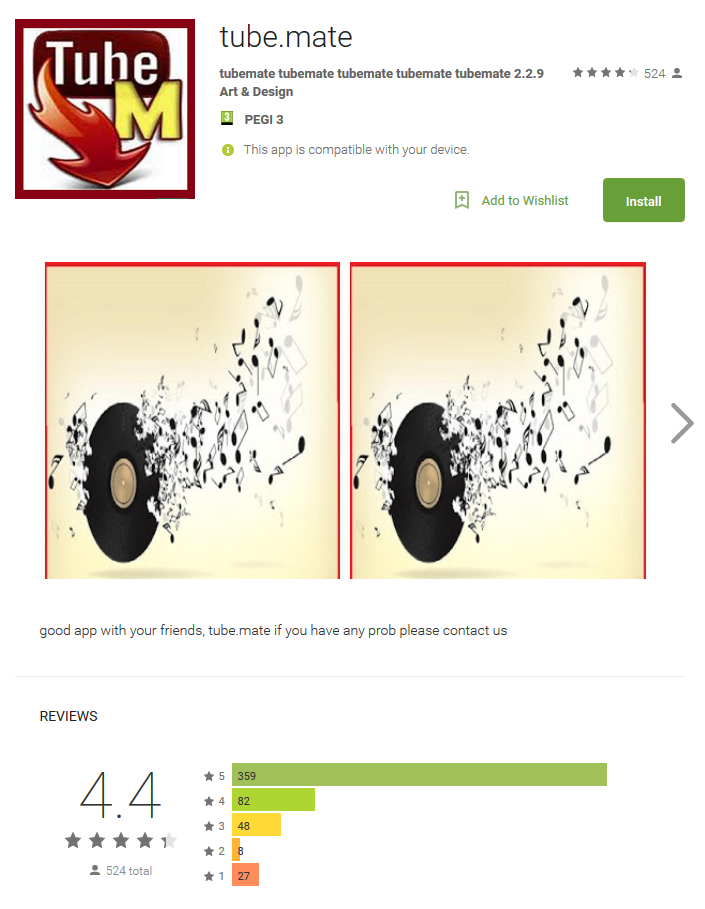
Figure 4 – High rating of the trojan as found on Google Play
How does it operate?
After the user launches the downloaded app by clicking on the “Music Mania” icon, the ad-displaying component is loaded. It manifests itself as a fake system screen requiring installation of “plugin android” and overlaying the screen until enabled.
By clicking the install button, the ad-displaying payload is installed. The user is then prompted to activate device administrator rights for the fake “plugin” by yet another non-cancellable screen.
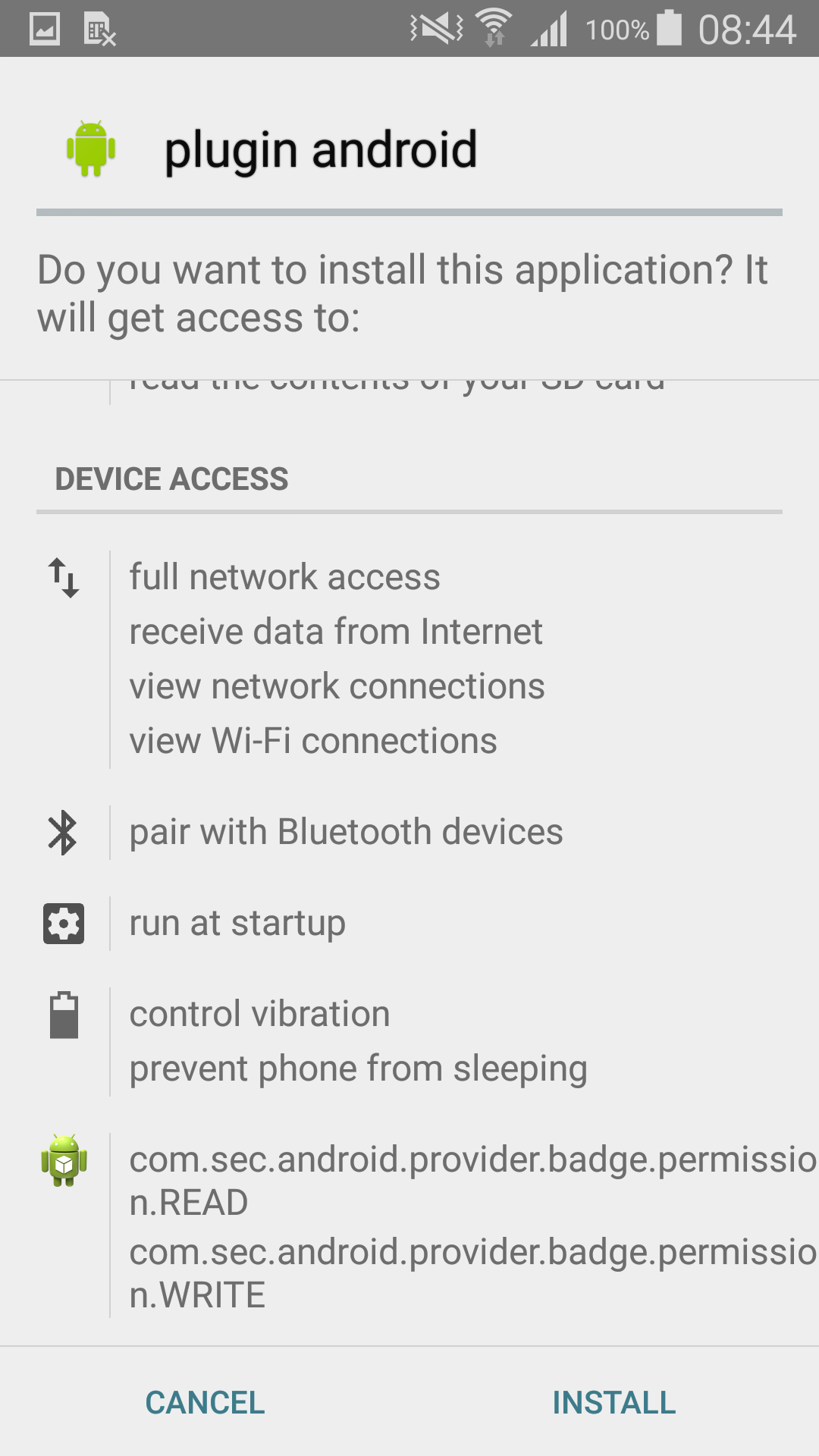
Figure 5 – Ad-displaying component disguised as “plugin android”
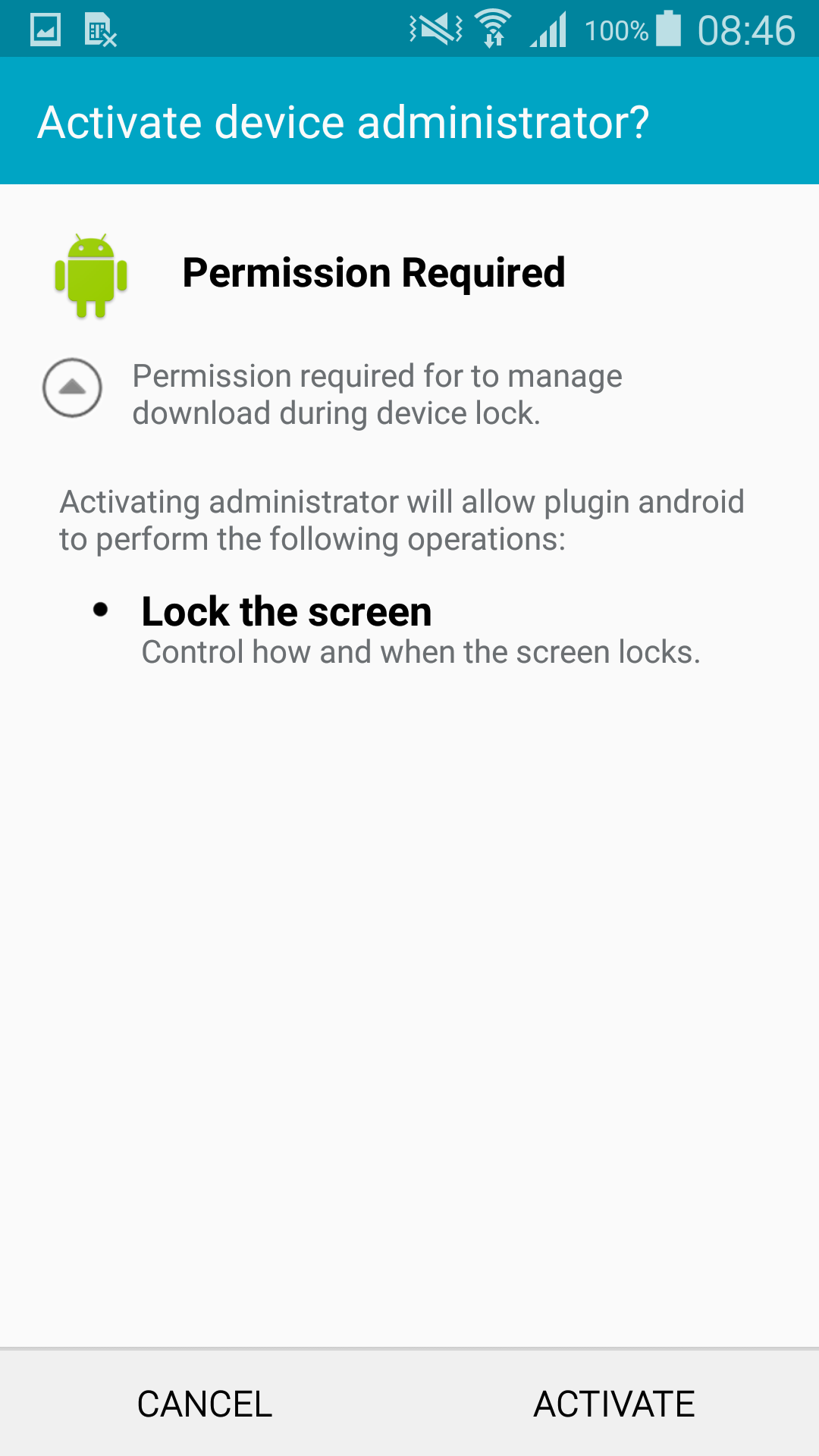
Figure 6 – Ad-displaying component requiring device administrator rights
After granting the rights, the user is immediately shown a screen full of ads and consequently asked to rate the app with five stars “to remove all ads”. Cancelling the message will result in an even greater flood of ads shown on the user’s device, aiming to provoke the user into rating the app next time the prompt is displayed.
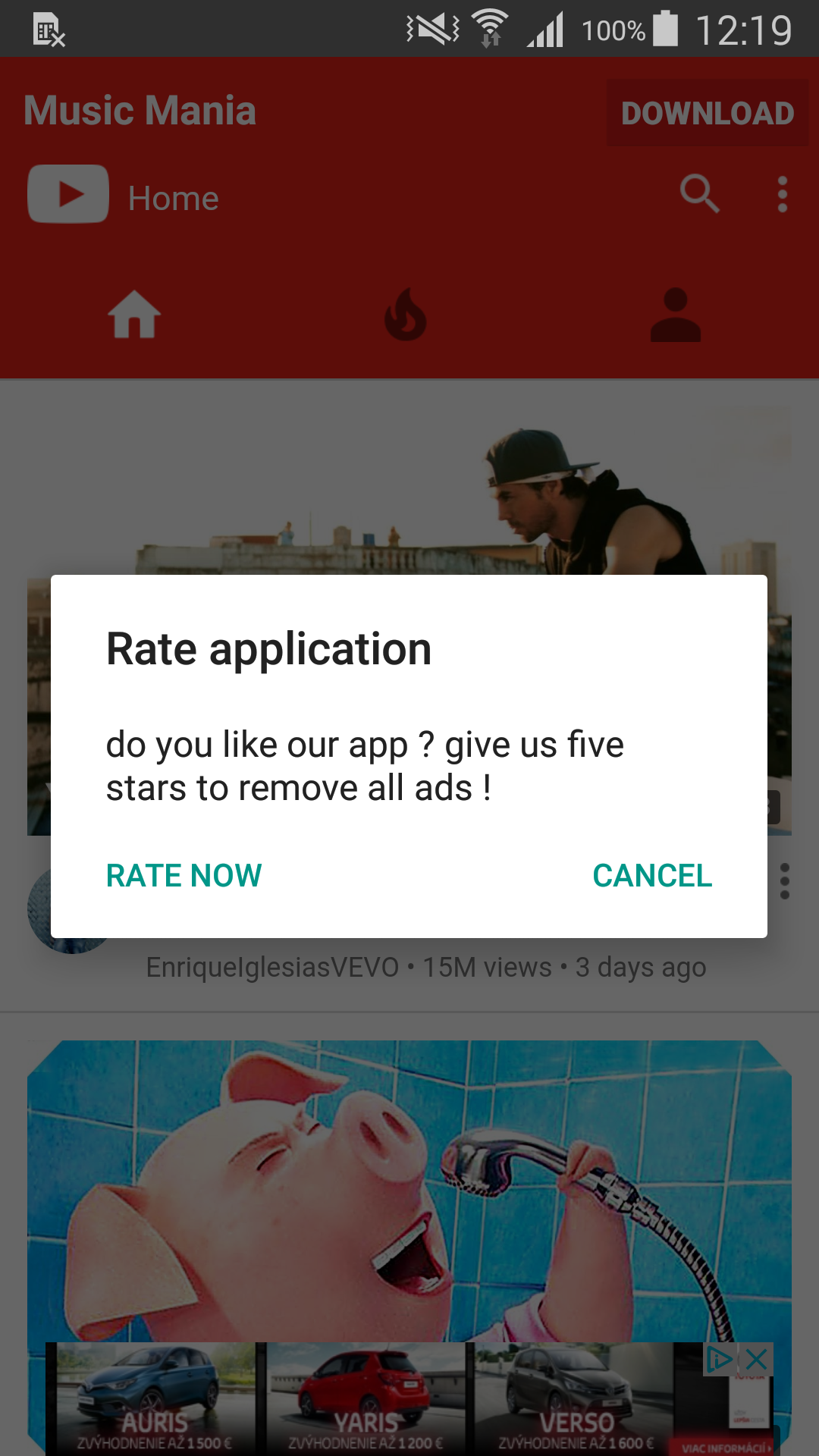
Figure 7 - Ad-displaying trojan requesting five star rating from user
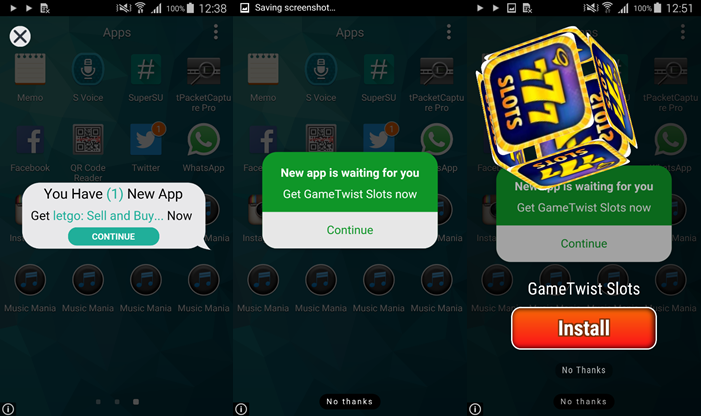
Figure 8 –Ad overload following canceled rating request
How do I clean infected device?
If you’ve downloaded this app, you will see both “Music Mania” and “plugin android” in your Application manager, with “plugin android” being the dropped payload responsible for aggressive ads. You will also find “Permissions required” under your device administrators.
Uninstalling the original app in Settings -> Application Manger -> Music Mania won’t be enough to remove the dropped payload. To fully clean your device of Android/Hiddad.BZ, disable its device administrator rights found under Settings -> Security -> Device administrators -> Permissions Required. Then you can proceed to uninstalling the payload by going to Settings -> Application Manger -> plugin android.
Alternatively, use a reliable mobile security solution to detect the threats and remove them for you.
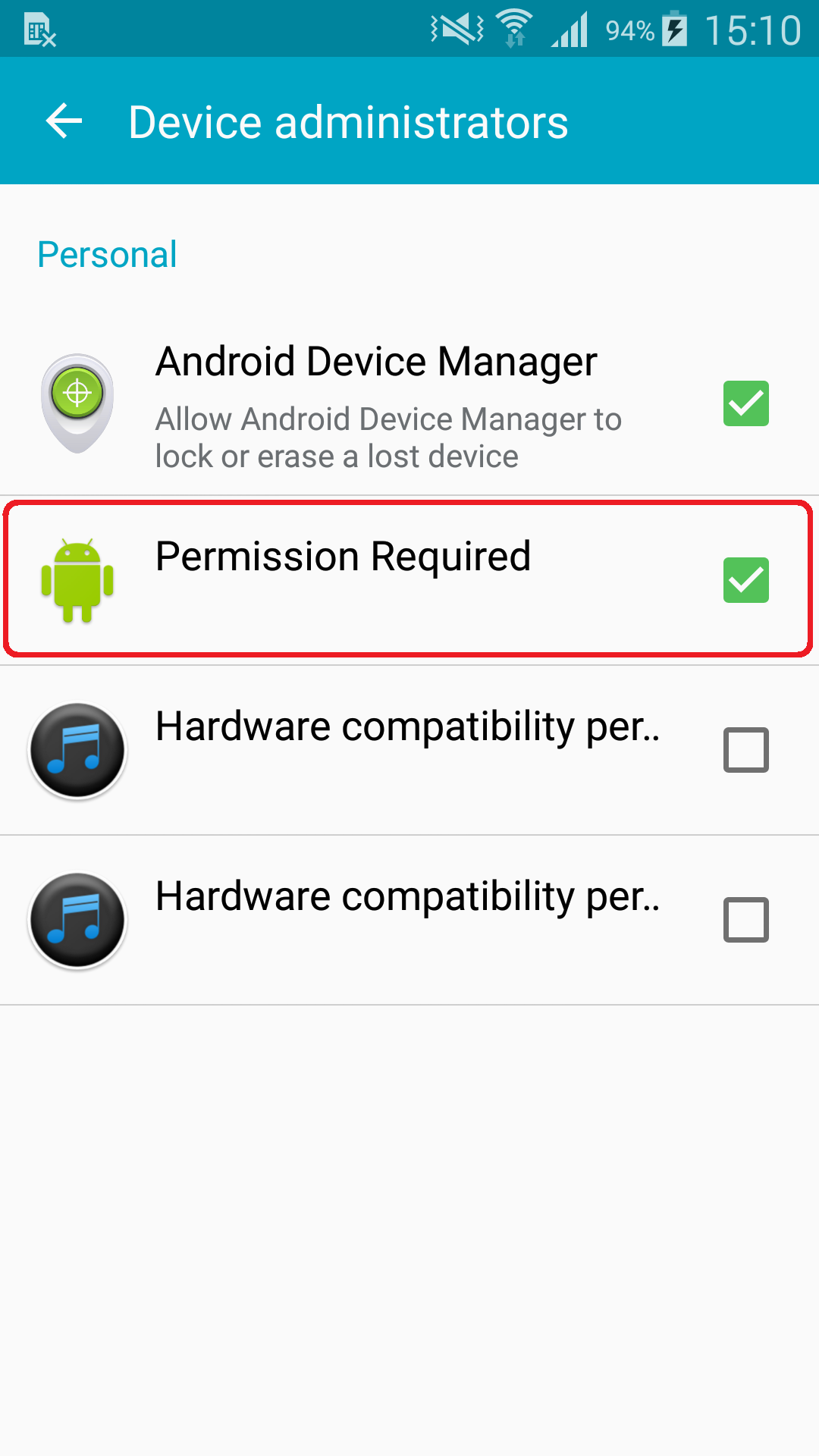
Figure 9 – Dropped payload under active Device administrators

Figure 10 – Dropped payload in Application manager
How to stay safe
Seeing even malicious apps tricking users into manipulating the Google Play rating system, one might question the much-repeated piece of advice “Check the rating before downloading”.
The advice still stands; only it’s not enough to check the rating. To get a real overview of what an app offers or doesn’t offer, take the time to read into user reviews. As demonstrated in the cases above, real users tend to be honest in their reviews – even if it means complaining about being forced to leave five stars, while leaving five stars.
Video capture from an infected device
Samples
| Package Name | Hash |
|---|---|
| com.baasdajie.zhofsdng | 75D1730511E35774866546177B93AD8AE59F616D |
| com.baoertcji.hansdfszh | 0C88D7F6742E4ECBD6FF032DDE989200EE385C8B |
| com.gannawen.dinergxi | 8501D2BDEC7EFF8CE19CCBC6CF6B8EB33996B7C5 |
| com.neigerj.gonfhgdgia | 8033C35A86E3B8FFF0642B29D6CCDB57E7C2A2DA |
| com.shisfdyan.pingsgfshan | DA7E8FA20E0718701B0198E0716C930556D4757C |
| com.suidfgdrning.zharetfou | 2D32C51DE3B9043443038113A61785E010F05C87 |
| com.yicsdfhang.dapdsfozhen | 458049945049B2AE456F01B9DA7A4F5564DBEA1C |
| com.bajie.zhong | 7F34FCC0783CF4526994065820220C4632303CD7 |




