Update (November 11th): For clarification, this article is focused on providing information on the increased activity of the Retefe banking trojan, which has been targeting various banks, mostly in Switzerland, Austria, and the UK. While this is happening at the same time as news breaking that Tesco Bank suffered a major cyberattack, there is no concrete evidence that Retefe is behind this.
Tesco Bank, which recently saw thousands of its customers lose funds to cybercriminals, has been found on the target list of the so-called Retefe malware. This trojan horse goes after users’ online banking credentials, which can be then misused to conduct fraudulent transactions. Many more thousands might be at risk as the malware’s target list contains several other banks.
In a statement, Tesco Bank’s chief executive Benny Higgins said: “Tesco Bank can confirm that, over the weekend, some of its customers’ current accounts have been subject to online criminal activity, in some cases resulting in money being withdrawn fraudulently.”
According to the BBC, approximately 40,000 saw suspicious transactions over the weekend and about 20,000 of them had money stolen. Tesco Bank later confirmed that around 9,000 customers were affected. Higgins assured that Tesco would continue to cooperate with the authorities and keep their customers informed through their website and other channels.
Tesco Bank decided to temporarily stop online transactions from current accounts, but left its other services such as cash withdrawals, both chip and PIN payments, as well as all existing bill payments and direct debits available for the current account customers. Based on that decision, one can assume that its core infrastructure hasn’t been affected and there are no additional details that would suggest otherwise.
Our active malware monitoring and ESET Threat Intelligence services show that Tesco Bank has recently been on the target list of Retefe trojan horse.
Disturbingly, our analysis shows that there is quite a lengthy list of other banks located in many other countries in this malware’s crosshairs. It must also be said that this campaign began at least as far back as February 2016. (Note that the Retefe malware had already been active even prior to this date but had been using different techniques to infect victims’ computers.)
If a user had been infected by this malicious code and tried to connect to any of the targeted online banking services, the malware modified the banking webpage in an attempt to harvest logon credentials.
Detected by ESET as JS/Retefe, this malicious code is usually spread as an email attachment pretending to be an order, an invoice or a similar file. Once executed it installs several components including anonymizing service Tor and uses these to configure a proxy for targeted banking sites.
The effect of this malware technique is that when an infected user tries to access their online banking website (full list of affected domains at the end of the blog post) they are covertly redirected to a fake copy instead.
Retefe also adds a fake root certificate disguised as if issued and verified by a well-known certification authority, Comodo. This makes the fraud very difficult to spot from a user’s perspective.
This is not a security issue on the side of any of the affected banks.
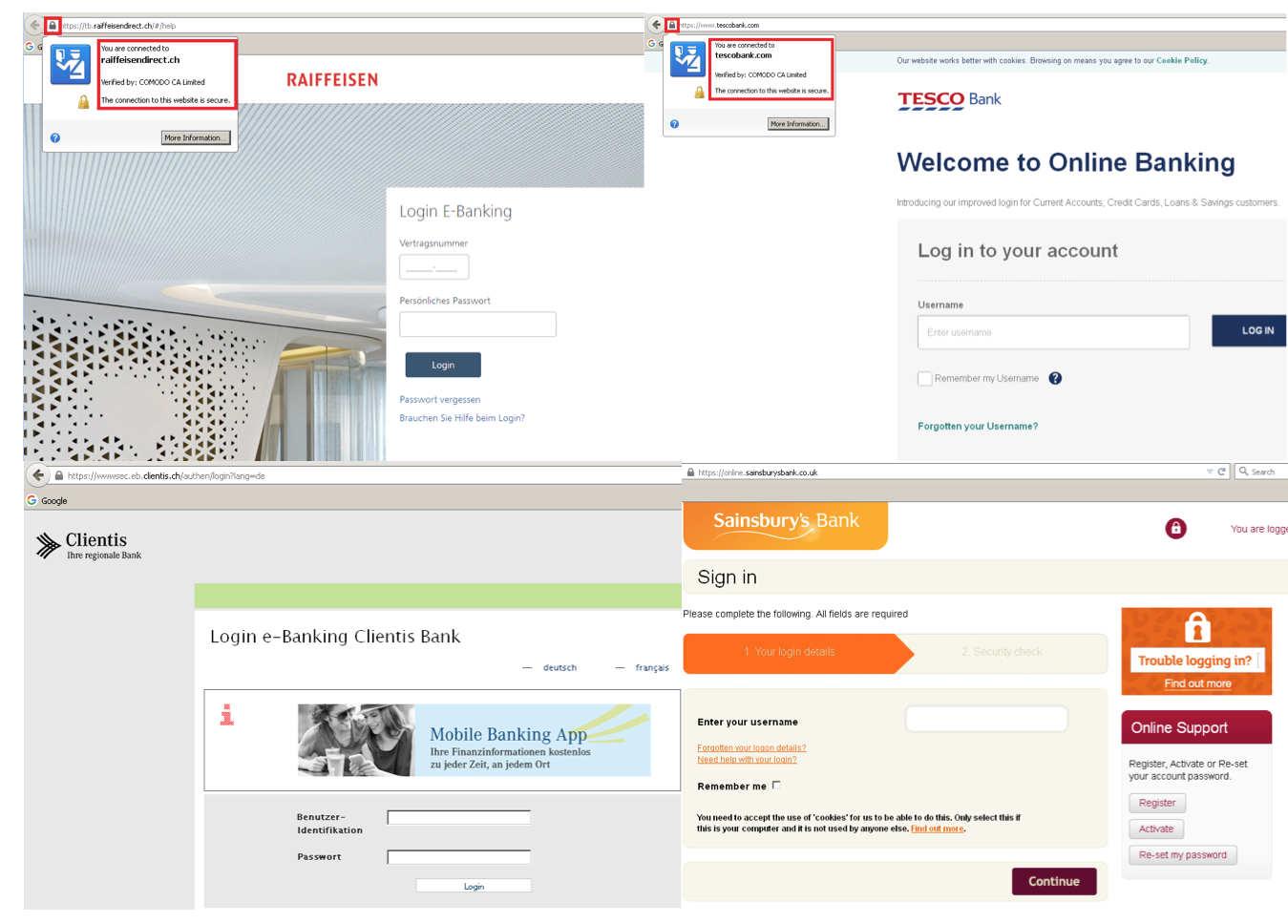
All major browsers, including Internet Explorer, Mozilla Firefox and Google Chrome were affected. In some cases, it also tried to trick the user into installing a mobile component of the malware (detected by ESET as Android/Spy.Banker.EZ). This mobile component was then used to bypass two-factor authentication.
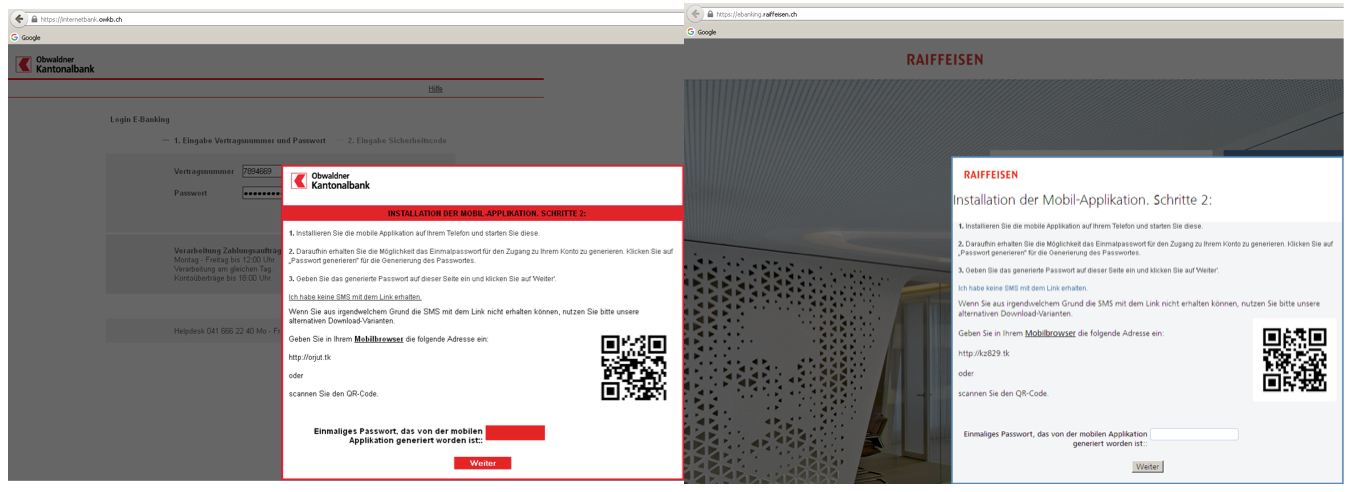
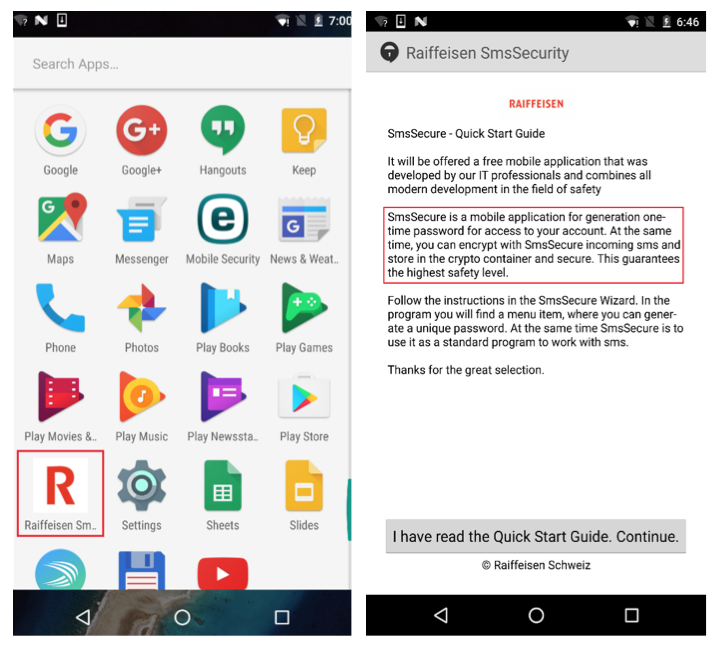
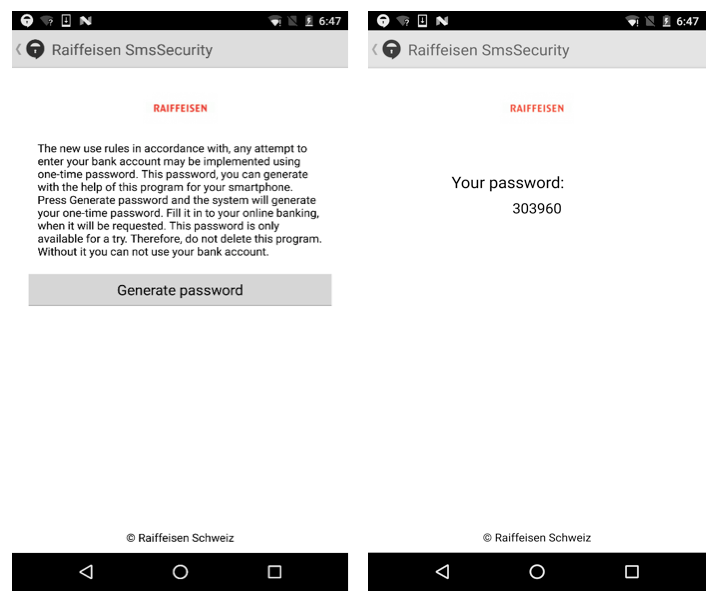
ESET researchers have also analyzed another variant, detected as JS/Retefe.B, with a slightly slimmer structure. Instead of using the Tor, the cybercriminals opted for the Tor2web service allowing the malware to access the anonymization services without using the Tor Browser.
Retefe has been on the radar of security researchers in the past, most recently when it targeted UK banking customers earlier this year. Since then it has added the mobile component and extended its list of targets.
Am I one of the victims?
Users of the services mentioned below are advised to manually check for the following indicators of compromise or use ESET’s Retefe Checker website:
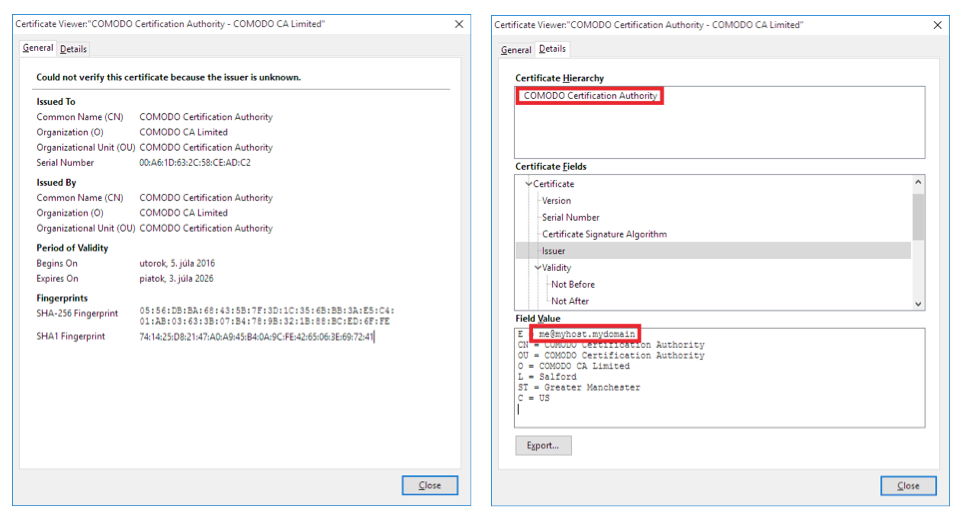
- Presence of one of the malicious root certificates claiming to be issued by COMODO Certification Authority, with the issuer’s email address set to me@myhost.mydomain:
For Mozilla Firefox, go to the Certificate Manager:
For other browsers, look within the system-wide installed root certificates through MMC (Microsoft Management Console):
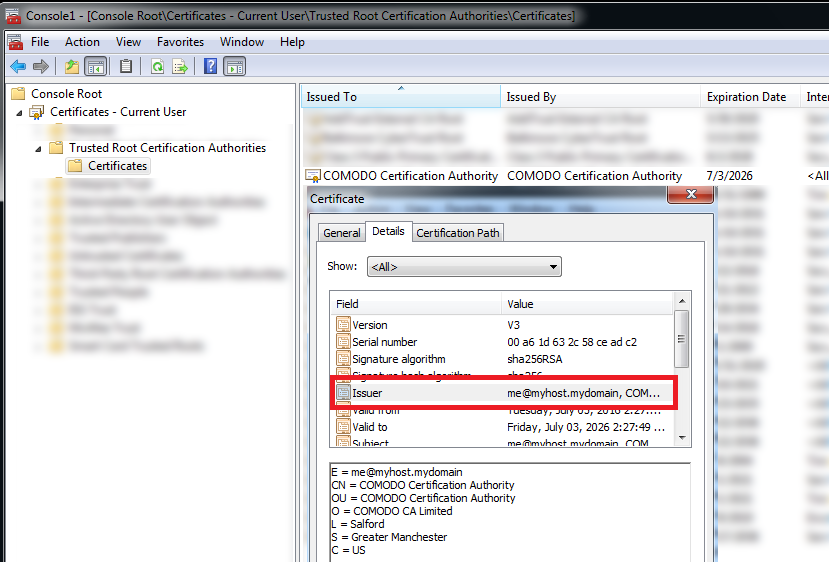
So far, we have seen two such certificates with following details:
o Serial number: 00:A6:1D:63:2C:58:CE:AD:C2
o Valid from: Tuesday, July 05, 2016
o Expires: Friday, July 03, 2026
o Issuer: me@myhost.mydomain, COMODO Certification Authority, …
and
o Serial number: 00:97:65:C4:BF:E0:AB:55:68
o Valid from: Monday, February 15, 2016
o Expires: Thursday, February 12, 2026
o Issuer: me@myhost.mydomain, COMODO Certification Authority, …
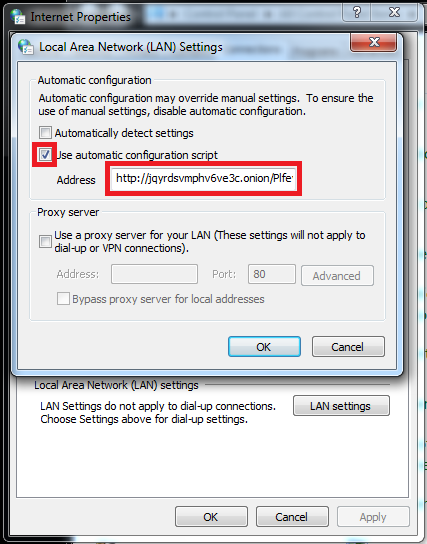
- Presence of malicious Proxy Automatic Configuration script (PAC) pointing to a .onion domain
http://%onionDomain%/%random%.js?ip=%publicIP%
where %onionDomain% is an onion domain randomly selected from the configuration file
%random% is a string of 8 characters from alphabet A-Za-z0-9
%publicIP% is the user’s public IP address
For example: http://e4loi7gufljhzfo4.onion.link/xvsP2YiD.js?ip=100.10.10.100
- Presence of Android/Spy.Banker.EZ on your Android device (can be checked using an app)
What should I do if I am infected by Retefe?
1. If you are using any of the services from the list of targets below, change your logon credentials as well as check for suspicious activity (e.g. for fraudulent transactions in your online banking).
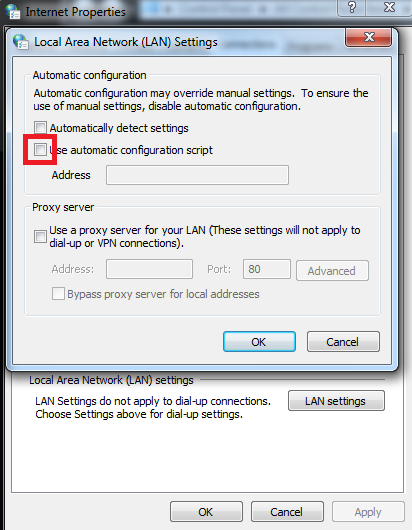
2. Remove the Proxy Automatic Configuration script (PAC):
3. Delete the above mentioned certificate.
4. For proactive protection use a reliable security solution with dedicated banking and payment protection. And don’t forget to protect your Android device as well.
Hats off to my colleagues Juraj Jánošík and Zolo Rusnák for the technical analysis.
List of targets
*.facebook.com
*.bankaustria.at
*.bawag.com
*.bawagpsk.com
*.bekb.ch
*.bkb.ch
*.clientis.ch
*.credit-suisse.com
*.easybank.at
*.eek.ch
*.gmx.at
*.gmx.ch
*.gmx.com
*.gmx.de
*.gmx.net
*.if.com
*.lukb.ch
*.onba.ch
*.paypal.com
*.raiffeisen.at
*.raiffeisen.ch
*.static-ubs.com
*.ubs.com
*.ukb.ch
*.urkb.ch
*.zkb.ch
*abs.ch
*baloise.ch
*barclays.co.uk
*bcf.ch
*bcj.ch
*bcn.ch
*bcv.ch
*bcvs.ch
*blkb.ch
*business.hsbc.co.uk
*cahoot.com
*cash.ch
*cic.ch
*co-operativebank.co.uk
*glkb.ch
*halifax-online.co.uk
*halifax.co.uk
*juliusbaer.com
*lloydsbank.co.uk
*lloydstsb.com
*natwest.com
*nkb.ch
*nwolb.com
*oberbank.at
*owkb.ch
*postfinance.ch
*rbsdigital.com
*sainsburysbank.co.uk
*santander.co.uk
*shkb.ch
*smile.co.uk
*szkb.ch
*tescobank.com
*ulsterbankanytimebanking.co.uk
*valiant.ch
*wir.ch
*zuercherlandbank.ch
accounts.google.com
clientis.ch
cs.directnet.com
e-banking.gkb.ch
eb.akb.ch
ebanking.raiffeisen.ch
hsbc.co.uk
login.live.com
login.yahoo.com
mail.google.com
netbanking.bcge.ch
onlinebusiness.lloydsbank.co.uk
tb.raiffeisendirect.ch
uko.ukking.co.uk
urkb.ch
www.banking.co.at
www.hsbc.co.uk
www.oberbank-banking.at
wwwsec.ebanking.zugerkb.ch




