During the first half of this year, ESET has observed an increase in the number of detections of Nymaim, a long-known malware family whose prevalence has fallen markedly since 2014. Back in 2013, WeLiveSecurity published a series of articles about this malware, in which we described its kill chain and evasion techniques, as well as the extent of this threat, which has resulted in more than 2.8 million infections.
In 2016, the number of detections observed has already increased by 63% compared to the first half of 2015, appearing mostly in Poland (54% of all Nymaim detections this year), Germany (16%) and in the US (12%). It has increased so much that if this growth trend continues, we will already have seen more detections by the end of June 2016 than in the whole of 2015.
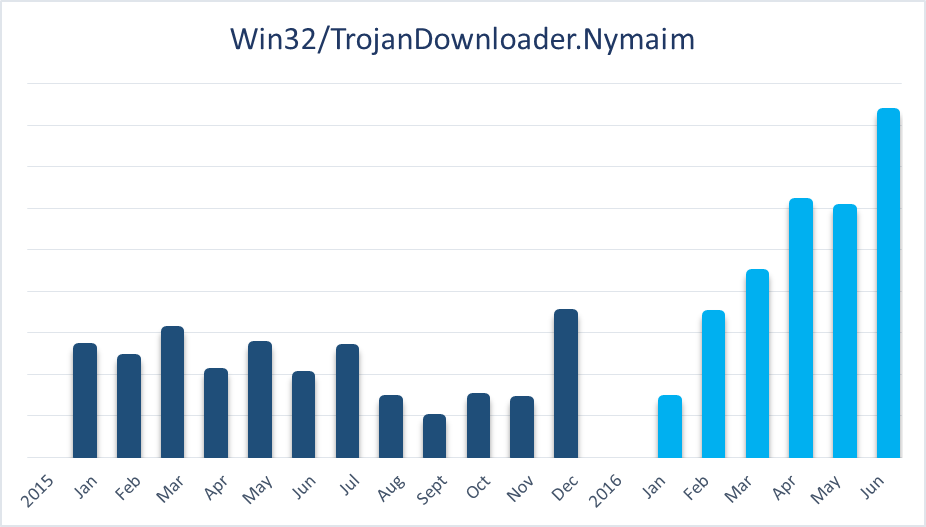
Figure 1: Nymaim activity worldwide in 2015 and January - June 2016
Phishing workflow
Unlike the 2013 version, which was being disseminated through drive-by-downloads as the victims visited compromised websites, the new Nymaim's attack vector has shifted to spearphishing campaigns, with emails containing a malicious Microsoft Word .DOC file as an attachment.
This malicious document contains a macro to do its dirty work. Because default Microsoft Word security settings will prevent the macro from running, the document contains a couple of “tricks” to hopefully work around this.
First, the document contains a block of “garbled text”, presumably suggesting to the likely victim that something needs to be done to decode or decrypt it. Second, at the very top of the document is the message “Enable Content to run in compatibility mode”. This message is formatted very similarly to the warning bar of recent Microsoft Word versions, which warns users that macros in the current document have been disabled.
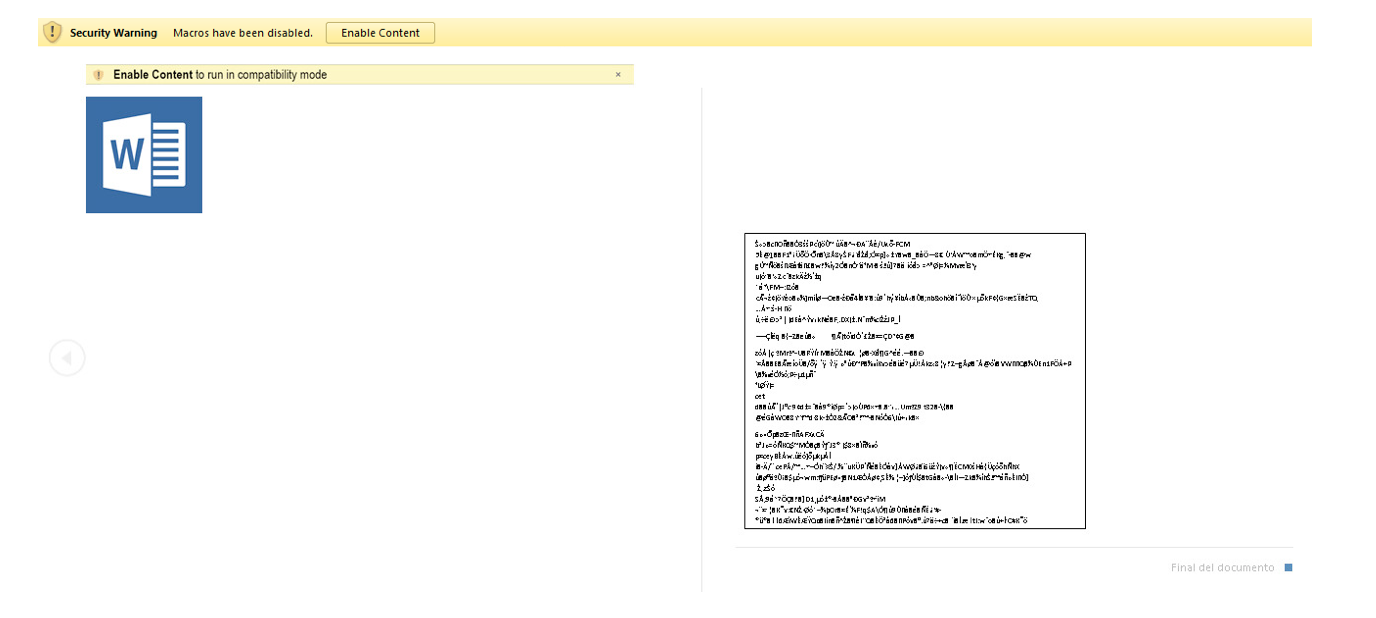
Figure 2: Malicious .DOC displaying security warning message in English
While this may work well to convince users of English versions of Microsoft Word to enable macros, if the document is opened in a different language version of Microsoft Word, this social engineering attempt may be much less compelling, as seen in Figure 2.
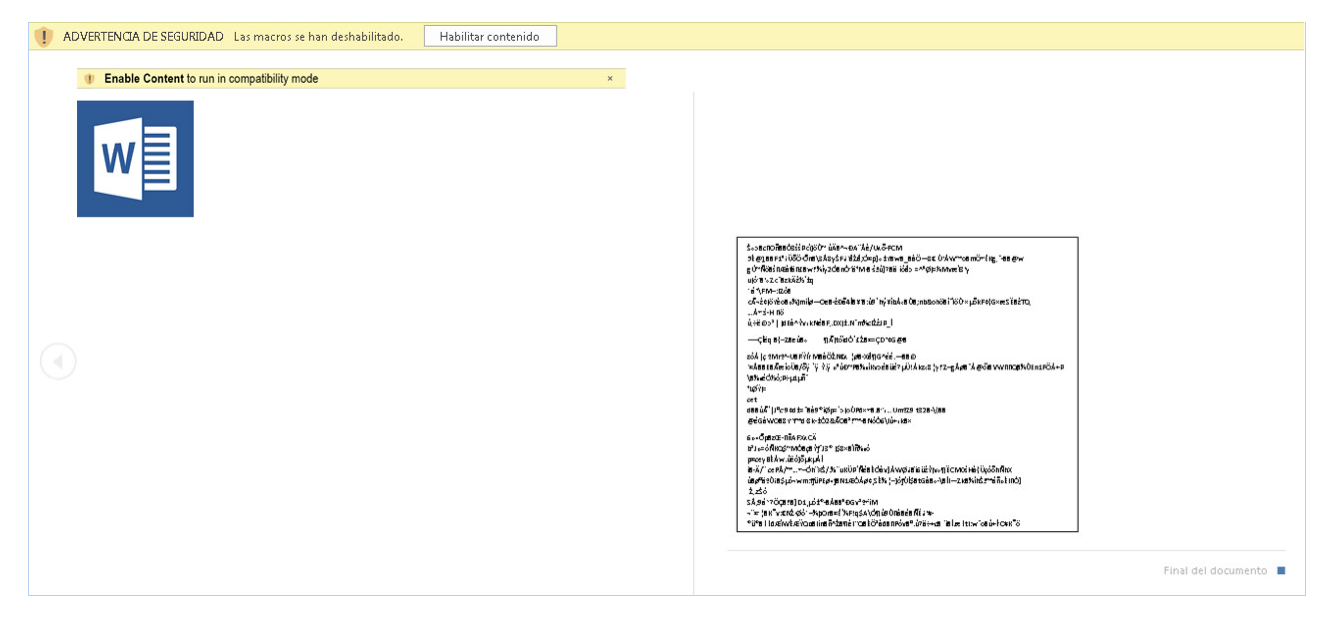
Figure 3: Malicious .DOC displaying security warning message in Spanish
With respect to this cyber kill chain, it starts with the execution of the malicious macros contained in this document. If the malicious macro - detected (and blocked) by ESET as VBA/TrojanDownloader.Agent.BCX - runs successfully, it downloads the Nymaim payload from the hosting website creating a new executable file in the temporary folder (%temp%), which it then executes.
Nymaim analysis
The advanced evasion techniques, combining obfuscation, anti-VM, anti-debugging and control flow capabilities of this family are well known. It consists of a two-stage downloader usually associated with file-encoding ransomware as the final payload.
Nonetheless, in April 2016, a hybrid variant of Nymaim and Gozi was uncovered, targeting financial institutions in North America, and providing the attacker with remote control over the compromised computer instead of encrypting files or locking out the computer in exchange for money.
Although it is possible to forge the relevant PE metadata, for this new variant they suggest that the sample dates from 17th May 2016, whereas the variant family was first detected in October 2015 as Win32/TrojanDownloader.Nymaim.BA. The malicious .DOC attachment was supposedly generated on the following day, which suggests that Nymaim was repackaged into this sample to be used in this specific spearphishing campaign.
Nymaim in Brazil
In Brazil we also observed highly targeted Nymaim attacks directed against financial institutions. Despite the relatively low number of detections, which is to be expected due to the very specific target selection, Brazil accounts for 0.07% of all detection incidents involving this variant, placing it 11th in the list of countries where this variant was most often detected. In contrast, considering detection statistics for all Nymaim variants since 2015, Brazil is in 39th place.
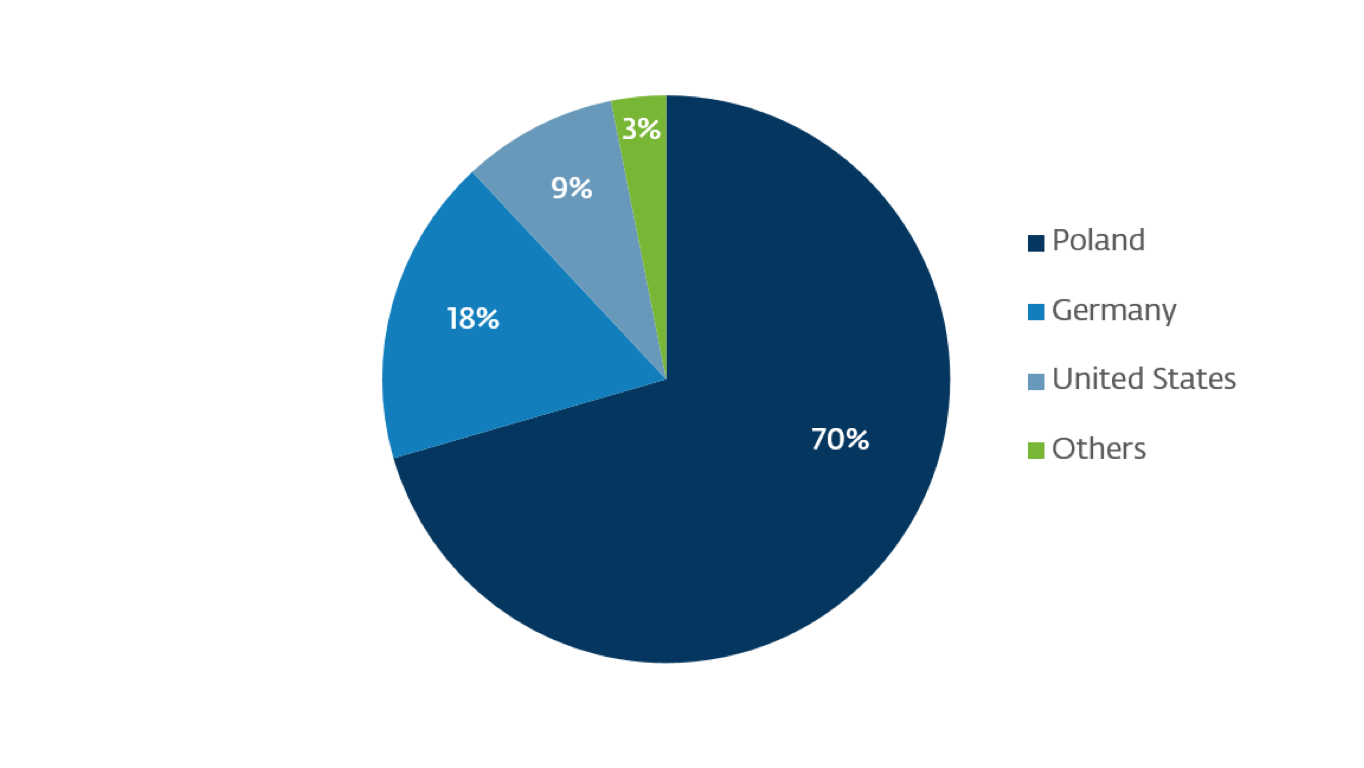
Figure 4: Nymaim.BA detection by country
In brief, this spearphishing campaign seems to have been specifically intended to target selected victims soon after Nymaim was rebuilt/repacked into Nymaim.BA, when both the downloader and Nymaim.BA payload were detected by very few antivirus engines.
Detection and countermeasures
A comment at VirusTotal by member @matthewm provides potentially useful information to assist with detection and mitigation of this threat.
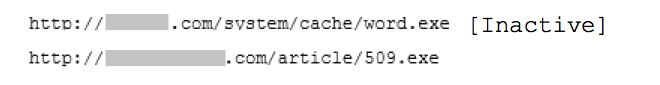
In his comment, he properly identified the payload as Nymaim and provided URLs where the initial downloader was found hosted until June 2nd:
He also provided a URL that was being resolved into IP by a fast flux DNS and supposedly hosted a final payload downloaded by Nymaim:

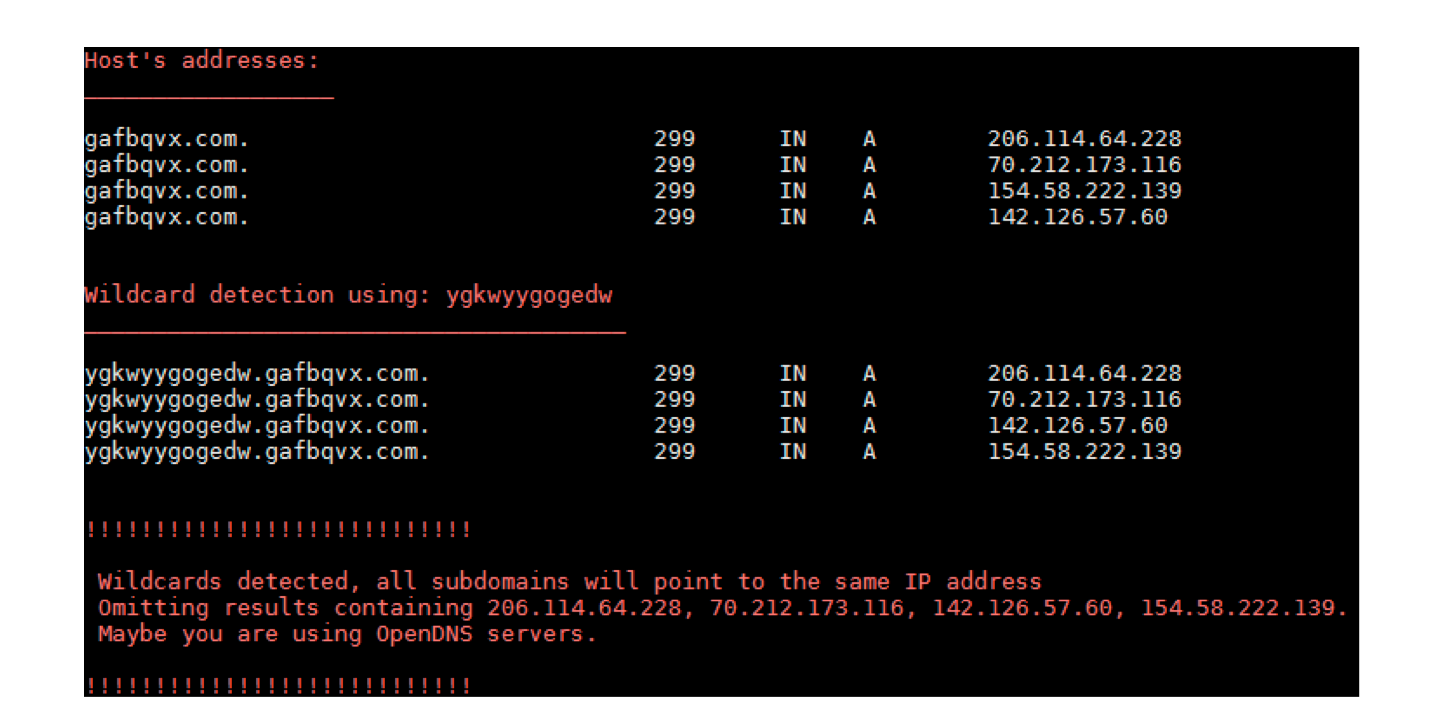
Figure 5: Fast flux DNS entries of gafbqvx.com on 2nd June 2016
Below you will find a full list of IPs resolved from DNS queries of gafbqvx.com since its first appearance on May 16th through to June 2nd, 2016, which includes new IPs observed since @matthewm’s comment:
35.51.69.111
70.212.173.116
101.186.50.249
142.126.57.60
154.58.222.139
165.203.213.15
206.114.64.228
According to @matthewm, the last stage consists of a VNC connection to a remote host at 162.244.32.165:8458.
Thus, if you suspect that your computer or network has been compromised, we recommend you check that the IPs and URLs provided by @matthewm are not to be found in your firewall and proxy logs.
A prevention strategy for this threat can be put in place by blacklisting the IPs contacted by this malware at the firewall and the URLs at a proxy, so long as your network supports this kind of filtering.
Furthermore, it is important to make use of antimalware protection on your endpoints, along with anti-phishing and web control capabilities, and of course to keep it all up-to-date.
Indicators of Compromise
Hashes
| Threat | Hash (SHA-1) |
|---|---|
| VBA/TrojanDownloader.Agent.BCX | 87b47aa1d421679bc1200dd3b61f48cc8991e421 |
| Win32/TrojanDownloader.Nymaim.BA | d983920eee2fc7306e500ee3df7791a612a6ba4b |
Network
Connections to the following IPs and URLs:
31.184.234.158
35.51.69.111
70.212.173.116
101.186.50.249
142.126.57.60
154.58.222.139
162.244.32.165
165.203.213.15
206.114.64.228
hxxp://gafbqvx.com/xyg9rwlq/index.php
hxxp://olmart.com/system/cache/word.exe
hxxp://securesrv15.com/article/509.exe




