Just when it seemed that the latest round of scams via WhatsApp was coming to a close, we have discovered a new one. This fake survey promises a chance at a discount coupon from Burger King, but ultimately ends by signing up victims to services that were not requested.
In this post, we will show our readers how not to fall into these traps, and also what technical resources attackers use. The WhatsApp scam campaign, so far, has spread in at least the following languages: English, German, Spanish, Portuguese, and Italian.
The start of the campaign
The scam begins with an instant message in WhatsApp, which usually comes from a known contact or group. The text offers you a chance to receive a voucher, allegedly from Burger King, for a certain sum of money.
This is an example of social engineering, used in both marketing and cyberattacks: it is the art of inducing people to perform certain acts that they might not otherwise be inclined to perform. The victims of this scam are the key players in the spread of the campaign. If the concept of social engineering is unfamiliar to you, we discuss this in more detail below.
How does it work?
Once the user clicks on the link we see in the figure below, the victim is redirected to a survey containing several questions, similar to the following:

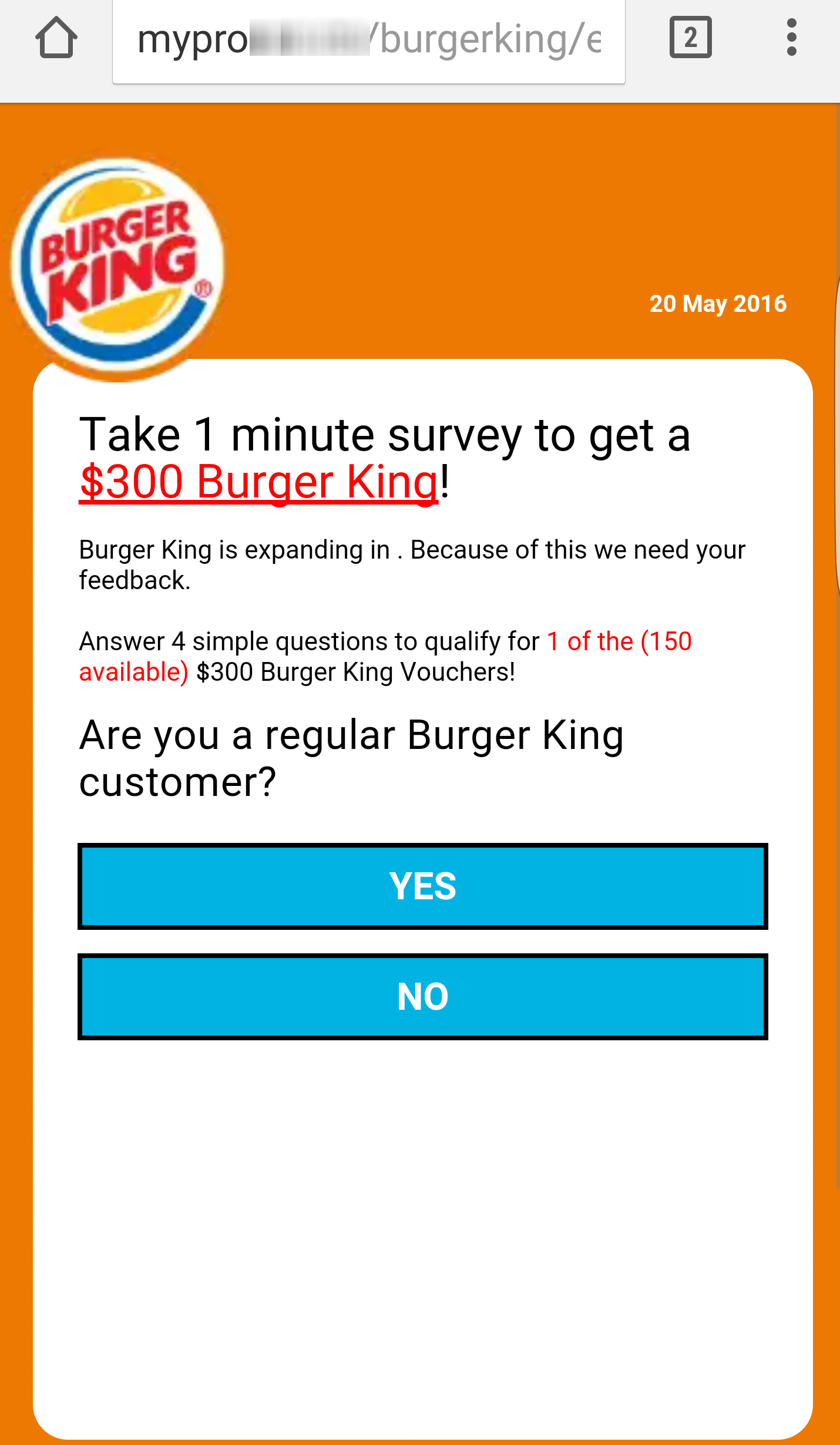
Figure 1 – Survey used to divert attention
Here, the 'only 150 coupons left' is the social engineering technique used to try to induce the victim to click quickly, without thinking.
Now let's see what's behind the scenes
It is interesting to note that in this case cybercriminals added a line of code to disallow search engines like Google or Bing to index their content, using the "noindex" function. Thus, the attackers hope that campaign will remain undetected for longer and will only be accessed by victims who directly access the link.
In addition, this type of campaign is only functional if viewed from a mobile browser — for instance, from a smartphone or a tablet. If you were to try to open it from a regular computer, an error would be displayed and the app would exit.
This is an ‘update’, since previous campaigns did not have this extra line of code (see below). These previous campaigns could be displayed on both mobile devices and desktop computers. The following screenshot shows how that function is called on certain devices:
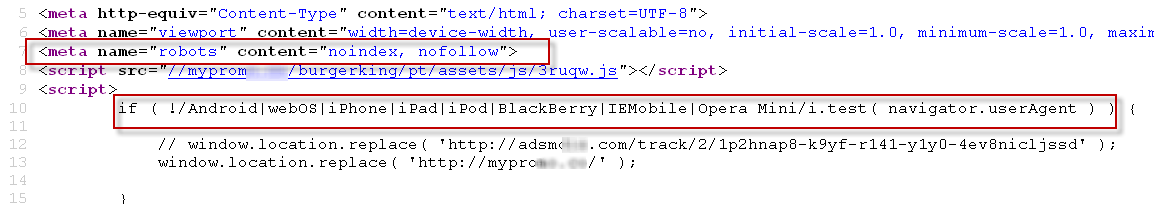
Figure 2 – 'noindex' used to disable search engines to index the content
Now, a bogus check indicates that there are still coupons available and a message that the victim has won his own (how lucky, right?) is then displayed.
In the next step, the victim becomes the main propagator of the scam: in order to receive the voucher, the message needs to be shared with 10 friends or three WhatsApp groups. And to make sure the victim makes the decision quickly, a counter displays a message that this “offer is valid for only 225 seconds”.
Technically, the source code below shows this part of the campaign. Both the redirection and the propagation method are presented in the following image:
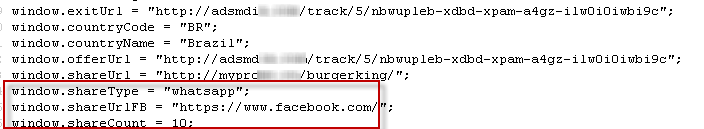
Figure 3 – Redirection URLs
It is noteworthy that the campaigns without the extra line mentioned above (that precludes viewing except on mobile devices) may spread on Facebook also.
In the end, to the disappointment of all who ever thought that they might win vouchers, the attackers finish the scam by sending the following message: “Thank you for participating. You did not win; try again and good luck.”
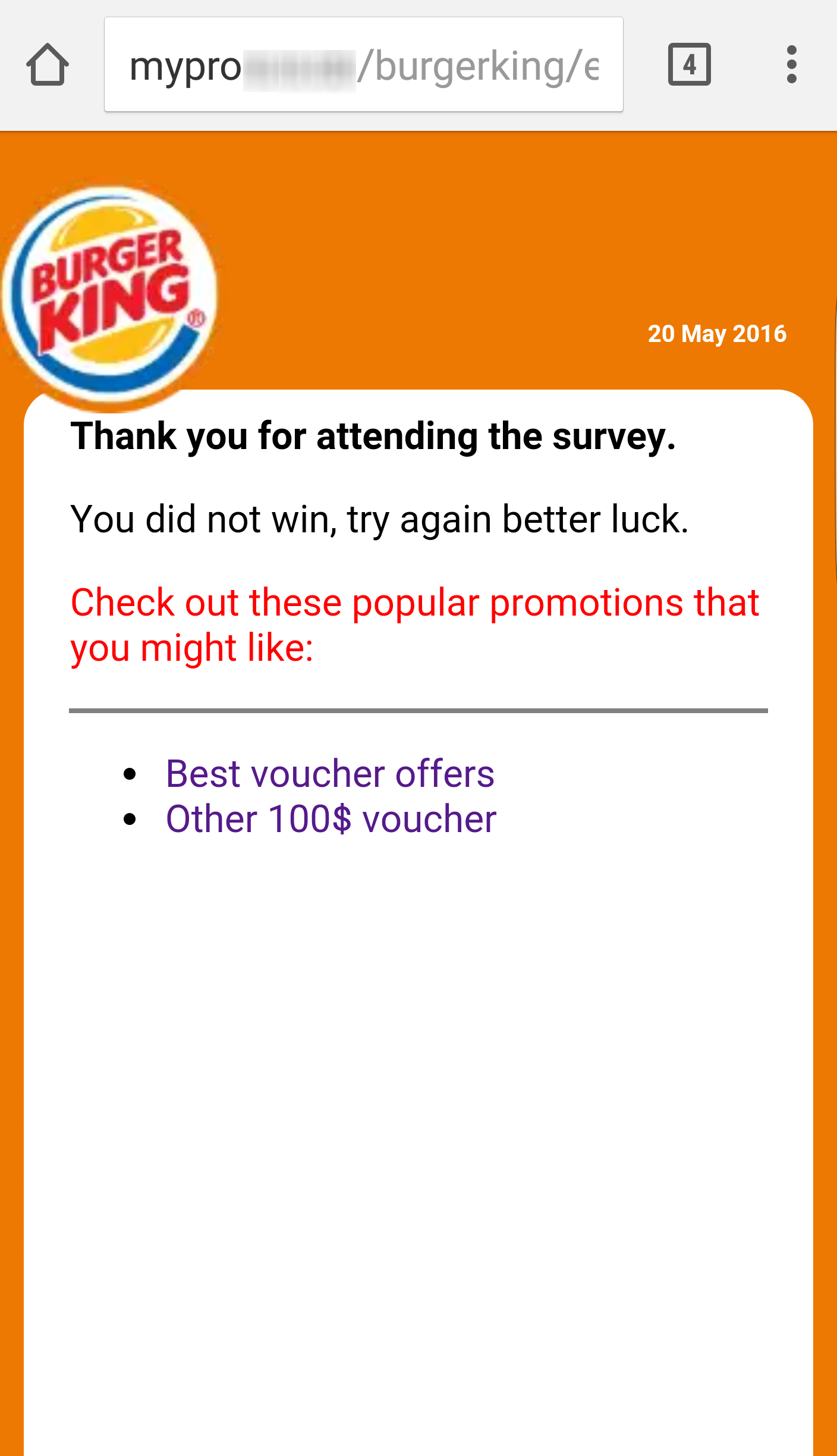
Figure 4 – Finishing the scam and offering new 'vouchers'
Another significant detail is the ability to change the language and currency automatically, depending on the user's IP address and the browser's language settings.
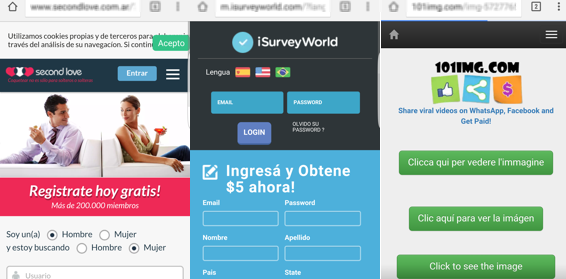
What happens internally (and unknown to the user) is multiple redirections that have different objectives: from generating clicks to giving a few cents to the author of the fraudulent campaign, to the registration of victim’s services that pay for getting new subscribers. The following screenshots show some of the services that you could get after the redirections:
How to protect yourself?
This kind of scam involving social engineering should be avoided through education and raising user awareness. Although this is nothing new, it is still widely used by cybercriminals and unfortunately we see every day how many people fall for scams in WhatsApp.
In case you receive such a message in WhatsApp, avoid becoming a victim by following these five simple tips:
- Do not click on suspicious links arriving in text messages, WhatsApp, any other messenger platforms or social networks (or email, web pop-ups, etc).
- Avoid providing personal information if the source is not known and unless a known source is also known to be reliable.
- Do not install applications from unofficial repositories. Instead, patronize only reputable sources like Google Play and The App Store.
- Do not share any suspicious messages (that appear malicious, or even might not) with your contacts.
- Always protect yourself with a security solution that blocks malware and fraudulent sites like these.
For more information on scams, please check out some of our previous articles.