By now you should be settled back at work after the holiday break. Are you ready for 2016? I hope you're sitting comfortably, because from the security point of view it's bound to be a bumpy ride.
Microsoft
Yesterday was the second Tuesday of the month and you know what that means - Patch Tuesday (or as Microsoft would prefer you called it, "Update Tuesday").
As usual, Microsoft issued a bundle of security bulletins.
In all, the patches address 26 vulnerabilities in a wide range of products including Windows 10, Microsoft Office, Silverlight, Internet Explorer, and Internet Explorer's successor Microsoft Edge.
Of the nine security bulletins issued by Microsoft, six are described as critical and if left unpatched leave the door open for hackers to exploit for the purposes of remote code execution. In other words an attacker could trick your computer into running malware without you necessarily realising anything strange was afoot.
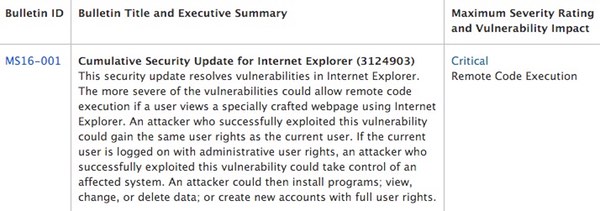
That's precisely the threat addressed by security bulletin MS16-001, probably the most critical of the bunch, which could see your computer infected by malware if you are tricked into visiting a boobytrapped webpage with Internet Explorer.
As Aryeh Goretsky noted yesterday, these are the last ever security updates that will be released for several versions of Internet Explorer running on various versions of Windows.
| Operating System | Supported version of Internet Explorer (as of January 12th, 2016) |
|---|---|
| Windows Vista SP2 | Internet Explorer 9 |
| Windows Server 2008 SP2 | Internet Explorer 9 |
| Windows 7 SP1 | Internet Explorer 11 |
| Windows Server 2008 R2 SP1 | Internet Explorer 11 |
| Windows Server 2012 | Internet Explorer 10 |
| Windows 8 | Microsoft recommends upgrading to Windows 8.1 |
| Windows 8.1* | Internet Explorer 11 |
| Windows Server 2012 R2* | Internet Explorer 11 |
| Windows 10* | Internet Explorer 11 |
| Windows Server 2016 Preview* | Internet Explorer 11 |
*Denotes operating system that shipped with Internet Explorer 11
It's clear that Microsoft is keen for home users and businesses to switch to Windows 10 and Microsoft Edge, and with its announcements and actions is sending a clear message that continued use of older versions of Internet Explorer could leave PCs at risk of attack.
If you're not yet ready to upgrade Internet Explorer or to switch to a browser from a different vendor, check out Aryeh's article for some great tips on how to reduce the risks on insecure and unsupported versions of Internet Explorer.
Curiously, a quick glance at the names of the security bulletins (MS16-001, MS16-002, MS16-003, MS16-004, MS16-005, MS16-006, MS16-007, MS16-008, MS16-010) shows that something is mysteriously missing.
Where is whatever vulnerability would have been addressed MS16-009? One can only assume that late in the process, Microsoft decided to pull MS16-009, presumably because they found a bug or software conflict which would have caused more problems than the security hole the patch was intended to fix.
No doubt it will see the missing patch will see the light of day in the coming weeks, but in the meantime - consider applying these security updates at your earliest opportunity and explore your options regarding upgrading or migrating from Internet Explorer if appropriate.
Adobe
And, of course, it's not just Microsoft that is pushing out regular updates to protect against security vulnerabilities.
 Yesterday, Adobe also issued its latest patches for Adobe Reader and Acrobat, fixing critical code execution vulnerabilities that could be exploited by a malicious hacker to infect and hijack vulnerable Windows and Mac OS X computers.
Yesterday, Adobe also issued its latest patches for Adobe Reader and Acrobat, fixing critical code execution vulnerabilities that could be exploited by a malicious hacker to infect and hijack vulnerable Windows and Mac OS X computers.
Ironically, even the software that Adobe uses to download updates, Adobe Download Manager, is reported to have had a vulnerability that could have unauthorised code to execute.
The good news is that none of the vulnerabilities are thought to have yet been exploited in the wild - but that is no excuse to treat them as unimportant, as that could change very quickly.
As with the Microsoft patches, you would be wise to ensure that your systems are updated with the latest Adobe patches at the earliest opportunity.
Of course, not all businesses will be able or willing to roll-out security patches across its entire enterprise without proper testing. There have been too many instances in the past where updates have caused software conflicts (probably the reason why MS16-009 has been delayed) that end up causing greater headaches than the problems they are attempting to resolve.
The secret to protecting your business is to adopt a layer defence, using a variety of technologies. Patching is, of course, an important part of that defence - but if you are protecting a large number of computers you might be wise to stagger the roll-out until you feel comfortable.
If all of this wasn't keeping you busy enough, don't worry - chances are there will be a security update for Java coming out from Oracle next week...




