From time to time, some malware propagation campaigns reach high propagation levels in one or several countries during a few days. In those cases, the users are specially vulnerable if they don’t protect their systems properly.
We have seen one of these scenarios during last week, when we observed a huge increase in detections of the Nemucod trojan, a threat that usually tries to download another malware from the internet. Those detections ratios were very high in some countries but also globally, and could indicate a campaign that is not focused on one country in particular but trying to affect as many users as possible throughout the world.
You’ve got an (infected) email
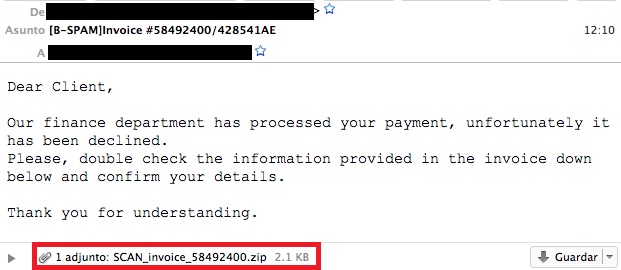
As with many other malware campaigns that we’ve analyzed recently, the attackers used the email as the attack vector. Posing as a fake invoice, they try to convince the users into opening an attached ZIP file. The sender of the email is usually another user that has been affected previously so the malware continues to propagate as long as it has possible victims.
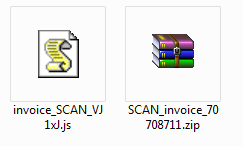
If we open the attached ZIP file we find a difference compared to recently analyzed samples. Instead of finding an EXE file, the ZIP container has a Javascript file inside. This technique might have been used by the attackers to avoid detection in some mail scanners and reach as many victims as possible.
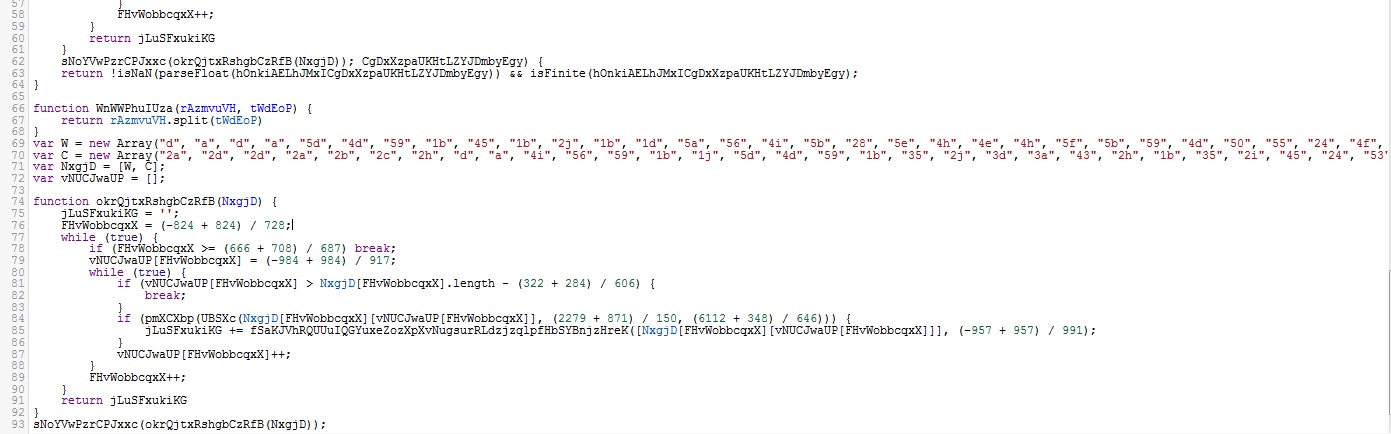
Using Javascript to download the payload
Anyway, a Javascript file is something that a user can execute and can be as dangerous as an EXE file. If we take a look at the code of the file we find several interesting things. One is that most of the variables used seems to be using random names. Also, we found two arrays in the code that could be a way of obfuscating the IPs or web addresses used by these criminals to spread the malware.
In fact we found two domains that were used to spread a new variant of Teslacrypt ransomware (detected by ESET as Win32/Filecoder.EM) among other threats. One of these domains belongs to a compromised German website but the other was created recently as we can see in this whois info.
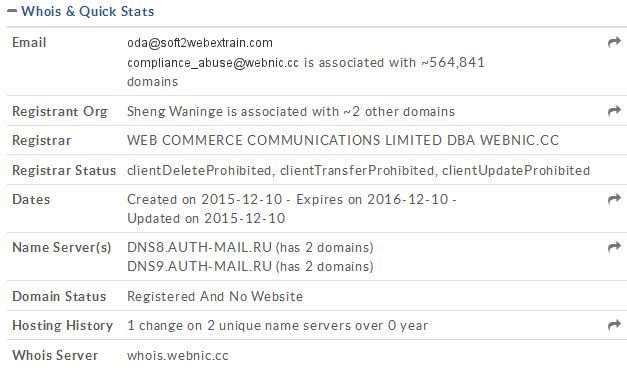
In fact, this web contained nothing but a warning saying that the web was empty because the site was just being created. We cannot say for sure that the web was generated just for spreading the threat but the registration date of the domain is suspicious at least.
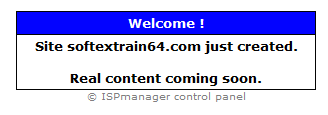
Infection of the user by Teslacrypt
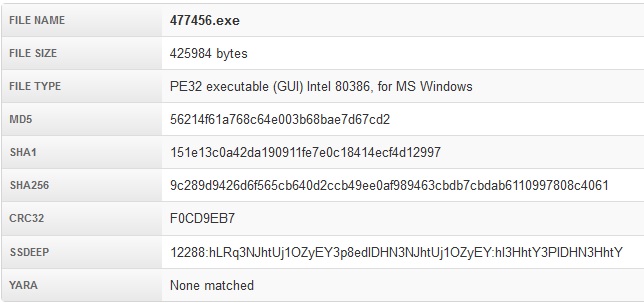
As we have already said, one of the malwares that was being downloaded from the malicious or compromised web sites was a variant of the Teslacrypt ransomware. The malicious file was an executable with just numbers as a name.
If the victim executes this file, the ransomware begins to encrypt some types of files usually used to store images, videos, office files and more, launching the following screen in the web browser when it finishes. This template has been used by other ransomware families and explains to the victims that they need to pay a ransom if they want to recover their personal files.
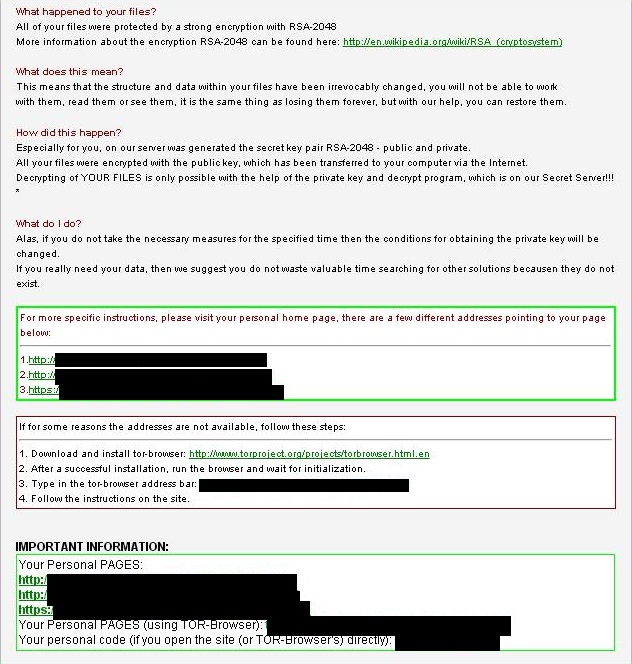
There is also another TXT file generated in each folder that contains encrypted files. In this TXT we can read similar instructions to the ones found in the HTML file but also some contradictions. For example, in the HTML file says that the ransomware is using RSA-2048 encryption, while in the TXT file it says that the encryption used is RSA-4096.
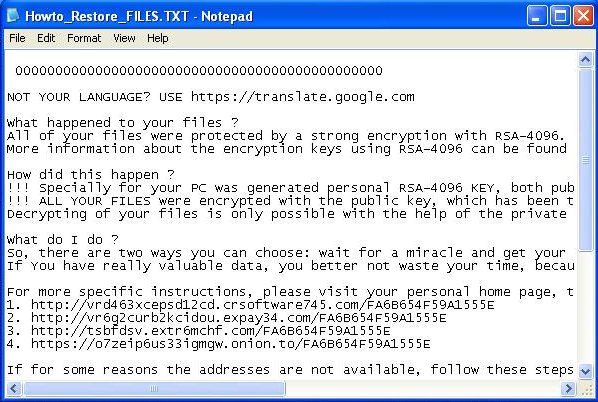
This can be explained by the use of the template of other families of ransomware like Cryptowall. Anyway, despite of the encryption algorithm used, most of the times the files can’t be reversed to its original state so the customer loses access to this information.
Nemucod impact around the world
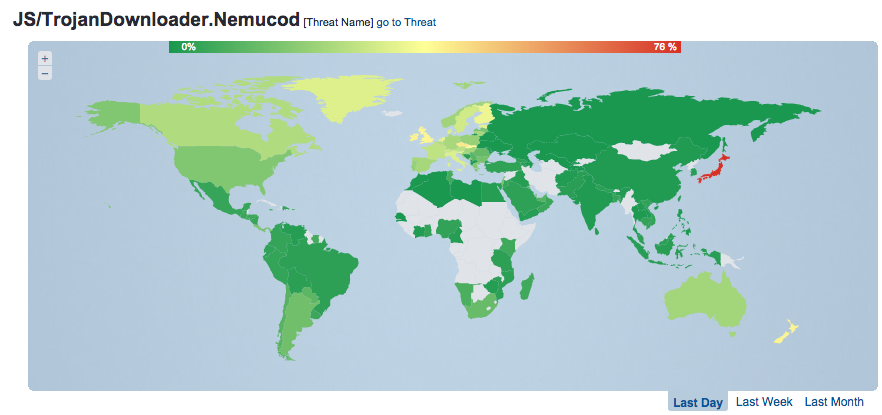
This malware propagation campaign has been quite interesting because the detection rates have been unusually high. We have seen peaks as high as more than 10% globally, but the impact has been much higher in some specific countries. In Europe we saw detection ratios of this threat above 20% in several countries (23% in Spain or 30% in Italy, for example).
In other regions such as the Americas we saw a lower detection ratio but also higher than usual (around 14% in Argentina or 15% in the US and Canada).
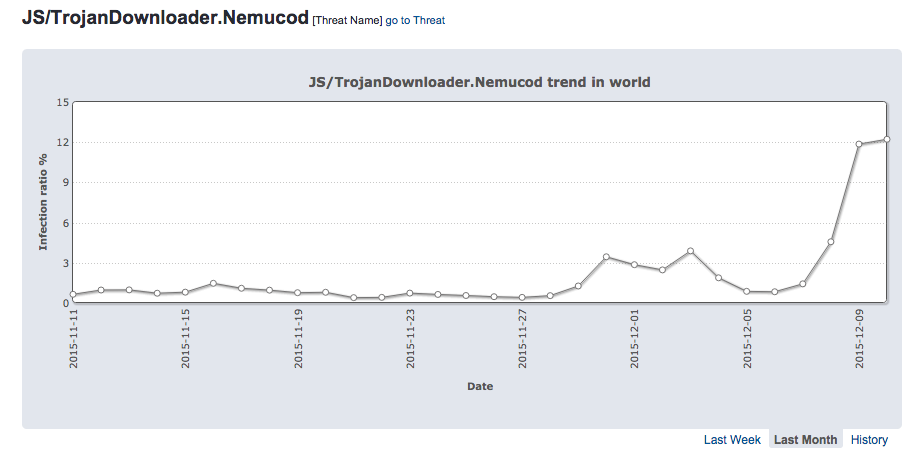
But the highest infection ratio detected was, by far, in Japan. During more than two days Nemucod detections reached above 75% percent of detections in that country. We still have to investigate why the detection was so high in Japan but it has been something that we have not seen in a very long time.
Conclusion
This new malware campaign didn’t affected as many users as previous ones but the detection rates shows us that, for some days, the amount of emails used to spread the threats had to be significantly high to achieve those percentages.
The fact that the numbers of affected users has not been as high as previous ransomware campaigns despite the elevated number of detections is good news. It means that the users are using protection measures capable of detecting new threats and it can also mean that they are not executing suspicious files attached to emails as the one we’ve analyzed.
Anyway, we still can improve our security measures and, to avoid problems created by a ransomware infection, one of those measures has to be an updated backup of all our important files in order to recover them as soon as possible.