When discussing banking trojans these days, Dridex is the one that everybody seems to be talking about the most. This is no surprise as it has inherited the popularity of the ancient Zeus trojan and grown to be one of the biggest threats that we can find right now. It is in constant evolution to become more efficient.
How Dridex works?
The way Dridex (also known as Bugat and Cridex) works can seem easy but it represents the evolution of previous banking trojans like Zeus (and its many variants). Attackers use attached files to spread this malware to all types of users, from individuals to big financial institutions.
It may sound particularly strange but, like a blast from the past, Dridex is using an attack vector, among others, that was quite popular in the late 90s: malicious macros included into MS Word and Excel files. We may have thought that we overcame this attack vector many years ago but it seems that we didn’t. Once the user executes the malicious file, Dridex infects the systems with a botnet that is controlled by the attackers.
From this moment, the criminals will be able to steal private information such as online banking accounts from the infected systems and they will also be able to send commands to the infected machines under their control.
New propagation campaign
Every few weeks we observe how a new Dridex campaign is launched by some criminal gang, affecting users around the world. Thanks to ESET Virus Radar, we can monitor which countries are more affected or even which are the ones targeted. Each one of these campaigns can cost millions to online banking users, so it’s important to alert them as soon as we detect a new variant spreading.
For some time now we have been monitoring several of these Dridex campaigns. Notably, since since August, there has been a spike in criminal activity. September and October have also been extremely busy months for the attackers behind Dridex, and November, not yet over, is proving to be no exception.
If we take a look at the detection ratio that can be observed at our Virus Radar service, we observe how a new threat is in the top three.
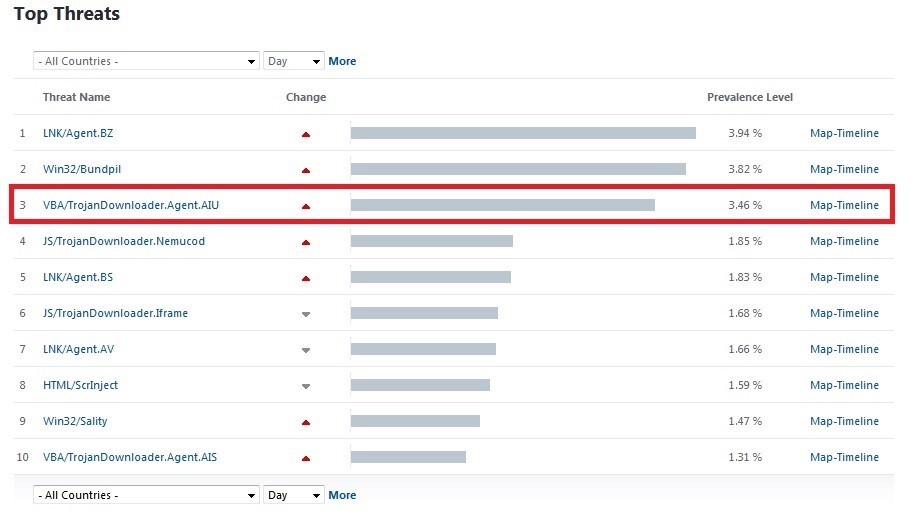
That malware was not even on the list a few days ago but now represents the most detected malware in several countries, most of them located in Europe and with special impact in Spain and Slovakia, but also in South Africa.
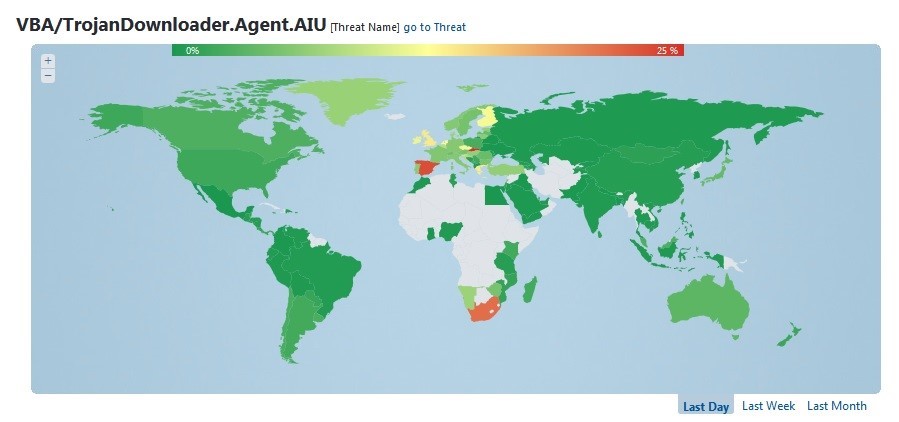
This information represents the amount of users that tried to open the infected attached file but ESET solutions blocked it because it was detected. And, because it is affecting countries with different languages, this is proof that the malicious email is written in English.
So, why would a user in Spain open an email in English? Well, that tell us a lot about how cybereducation in internet threats works in different countries. Some users are just curious and open every single message they receive, no matter where it comes from or what it contains. Luckily, for some of them, their security solution was able to stop this threat before it could cause any damage.
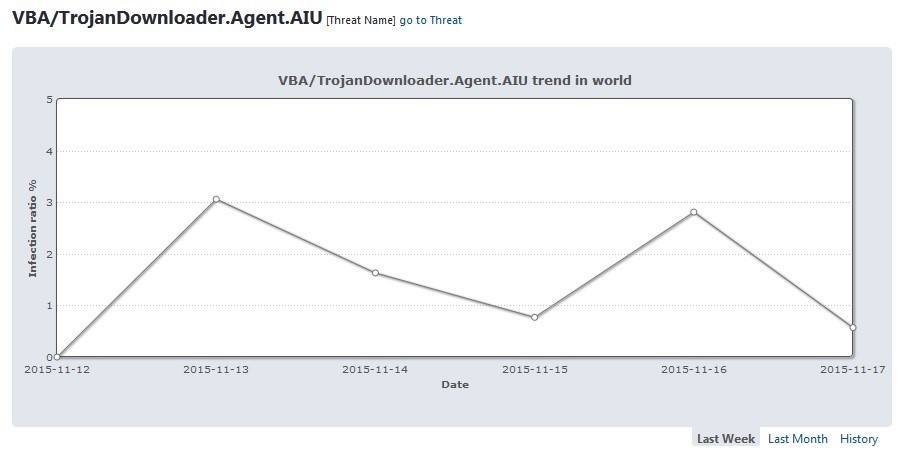
If we take a look at the timeline of this infection, we observe that since its creation last week, it had two peaks of activity on November 13th and 16th:
Conclusion
Every time a new threat like Dridex becomes this popular, it also draws the attention of the authorities. We have seen examples of security agencies such as the NSA, FBI, Europol, GCHQ, the Metropolitan Police Service, CERT-UK, Germany BKA, Spanish Guardia Civil and the Moldovan authorities taking down cybercriminal gangs or individuals that used Dridex to steal money from infected customers.
But we can’t just wait for the authorities to do their job since their resources are limited. As internet users we should be able to detect when we receive a malicious email, such as the ones Dridex uses and we can achieve this knowledge easily. All it requires is staying informed with the latest happenings in information security.




