The WhatsApp fraud on a large scale – multiple countries, languages and brands used
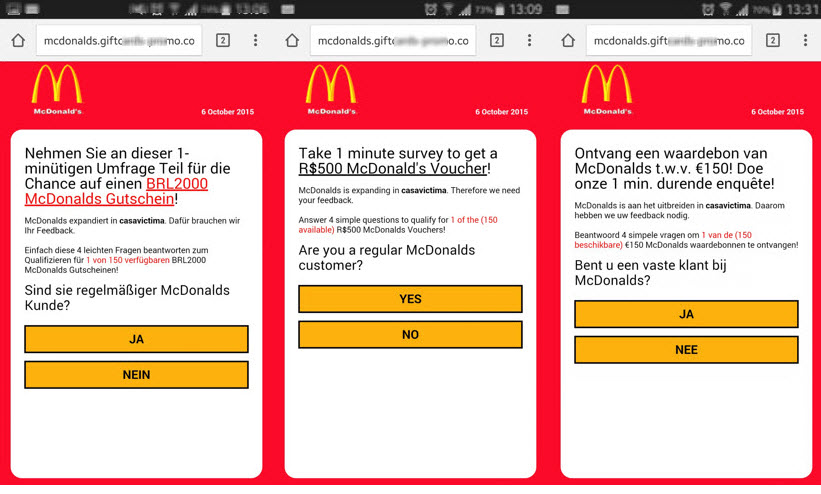
We have recently analyzed several scam campaigns that compromised a variety of popular international stores, such as Zara, Starbucks, McDonald’s and, specifically in Argentina, COTO supermarket. They consist on a series of customized fake surveys that adapt to the city and language of the user that receives them.
It all starts with a message in WhatsApp that can be in English, Spanish, French, German, Portuguese and other languages, according to where the IP address of the user belongs. It offers a voucher usable in the correspondent store, and the currency also changes depending on who receives the survey.
After quickly alerting our readers, we looked at the patterns shared by these campaigns in more detail. In this post, we will highlight some unusual tools employed by the cybercriminals behind this scheme, and then reflect on what seems to be an emerging trend of scams.
Social engineering – the art of manipulating people for a purpose – is one of the pillars of this type of fraud. Together with geolocation techniques, cybercriminals have achieved great propagation rates by turning a target user not only into a victim, but also at the same time into an accomplice in the spread of this type of scam.
It is also notable that these threats use the names of well-known stores and trusted brands that are not normally associated with digital fraud and do not handle sensitive information - as would be the case with financial institutions, which have been historically affected by malware and phishing sites. Thus, cybercriminals attempt to mislead home users by exploiting the inherent trust towards those brands, which have never been compromised nor associated with security incidents in the past.
Another important characteristic is the number of brands used to generate different templates - it is difficult to find a country where these brands do not exist.
So which companies are being used as a decoy?
When researching the servers involved, it was found that they were hosted in the Republic of Moldova, and further evidence was found in the DNS addresses showing that other companies were also being targeted.
This includes established department stores that are present in multiple countries, which were chosen for being very popular and having branches in as many countries as possible. We will look at some of them below.
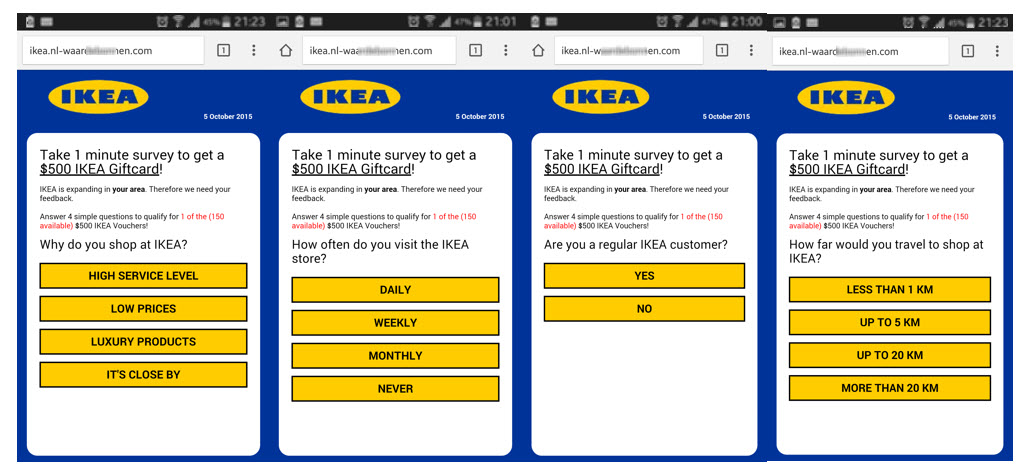
IKEA
IKEA is a Swedish multinational corporation based in the Netherlands, which has 238 stores operating in 44 countries. One of the main campaigns, which was only used for the initial part of the scam, used five associated subdomains including the name and logo of the company:
- ike**mo.com
- ike***-promotions.com
- ikea.nl-wa**en.com
- ike****-cards-promo.com
- ike******tions.com
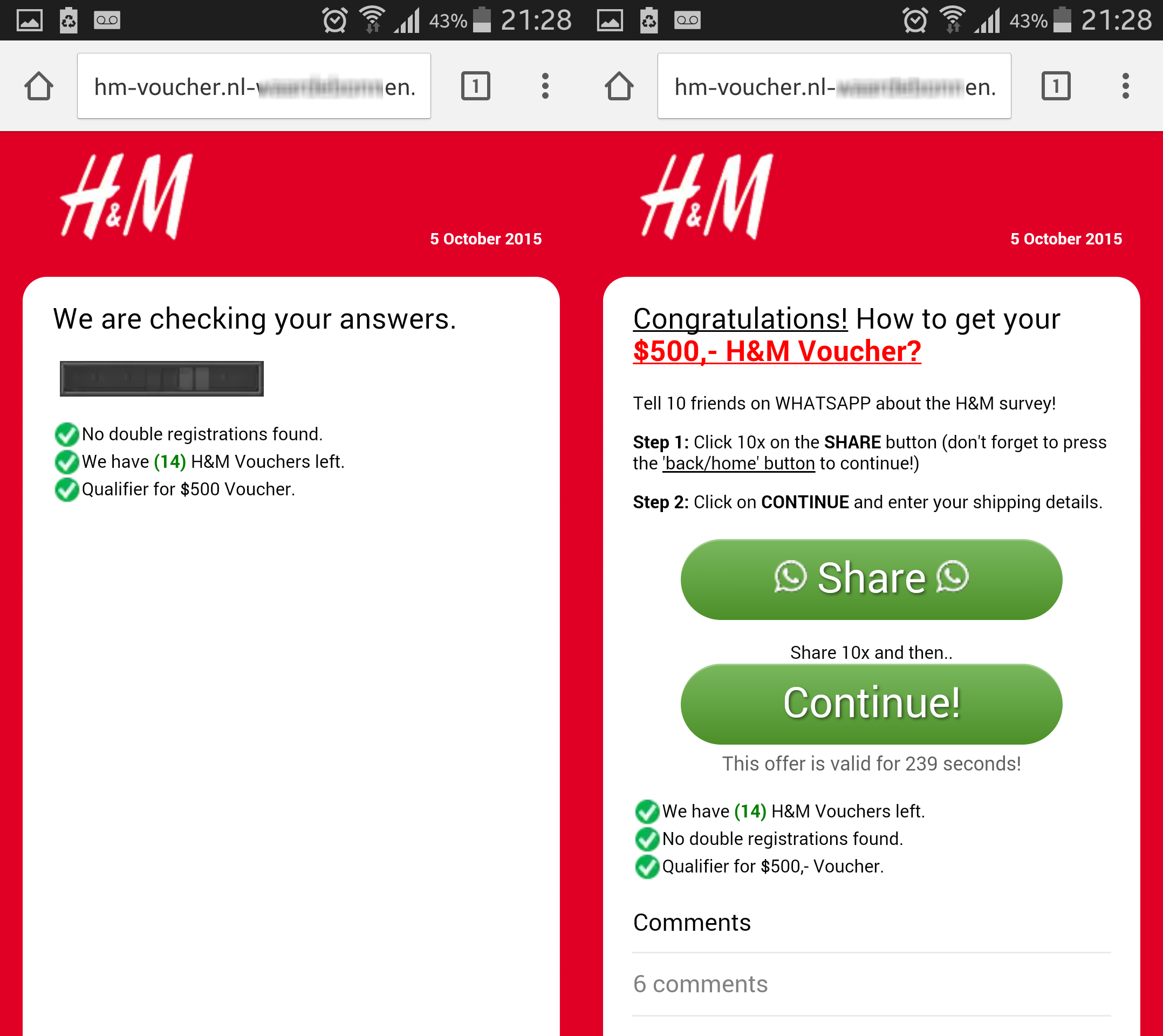
H&M
H&M is Swedish-based company operating in 44 countries in Europe, Asia, Africa and America. Cybercriminals took advantage of the great diversity of locations of their clothing stores. They used two domains with this brand, as shown below:
- hm-voucher.giftca***-***mo.com
- hm-voucher.nl-wa*****en.com
Once again, as we can see in the pictures below, the survey patterns match IKEA’s, but instead are customized with H&M's colors.
Moreover, the date is always updated:
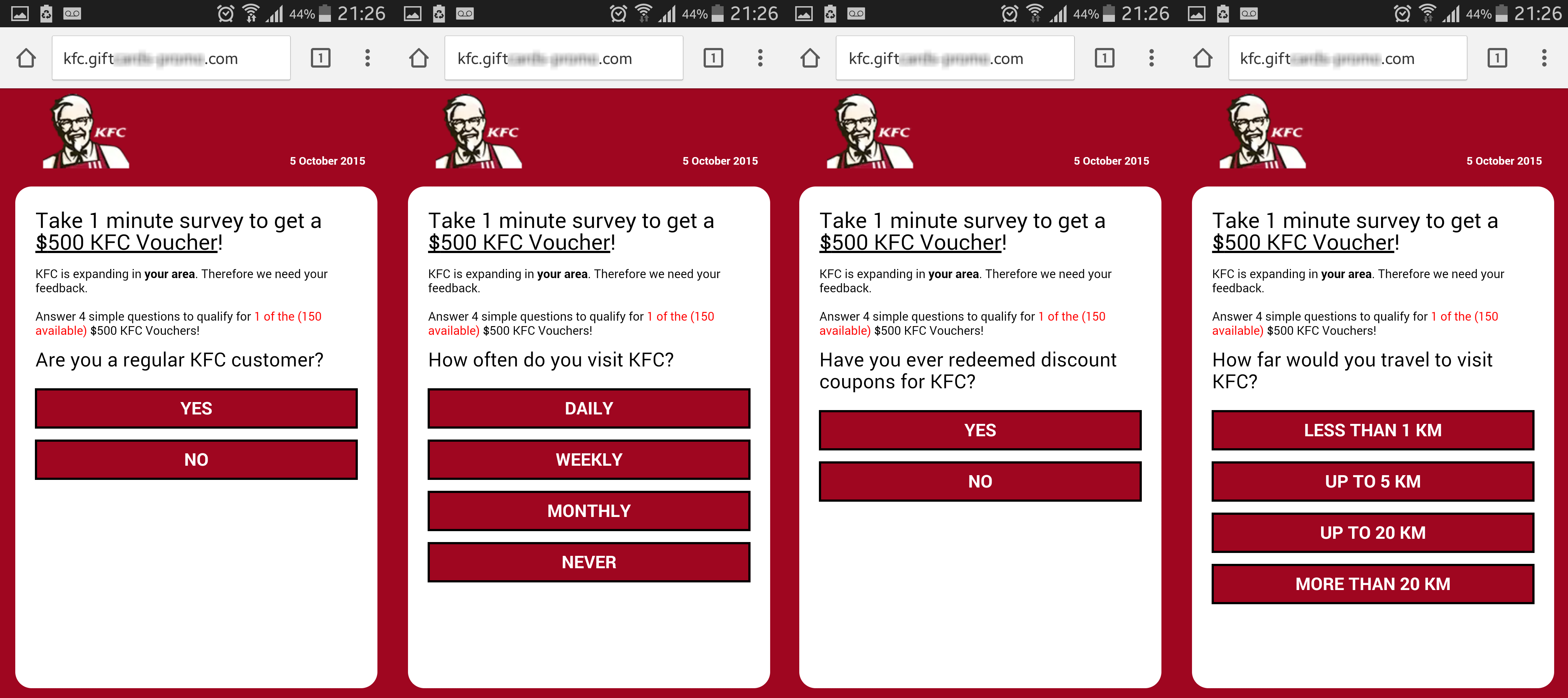
KFC
KFC, a popular fast food chain, has more than 18,000 restaurants distributed in 144 countries and, as with McDonald's, is also a victim of this huge fraud campaign.
The following images correspond to the version of the scam that used KFC's name:
SPAR
SPAR is a mega supermarket chain that has more than 20,000 branches in 35 countries, and this is how the scam that goes under its name looks like:
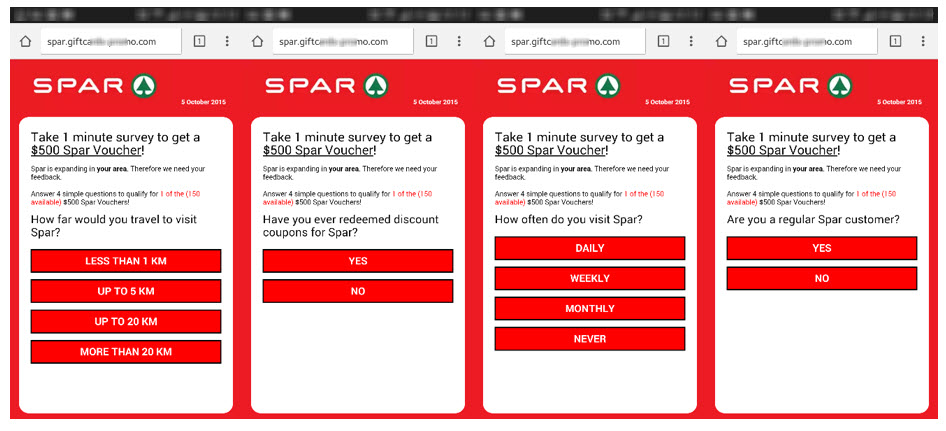
However, cybercriminals have sought to achieve greater penetration worldwide, which is why, in countries where these stores are not present, they looked for local popular stores to replace them. For instance, in Argentina they used the COTO supermarket chain, which has approximately 120 stores throughout the country.
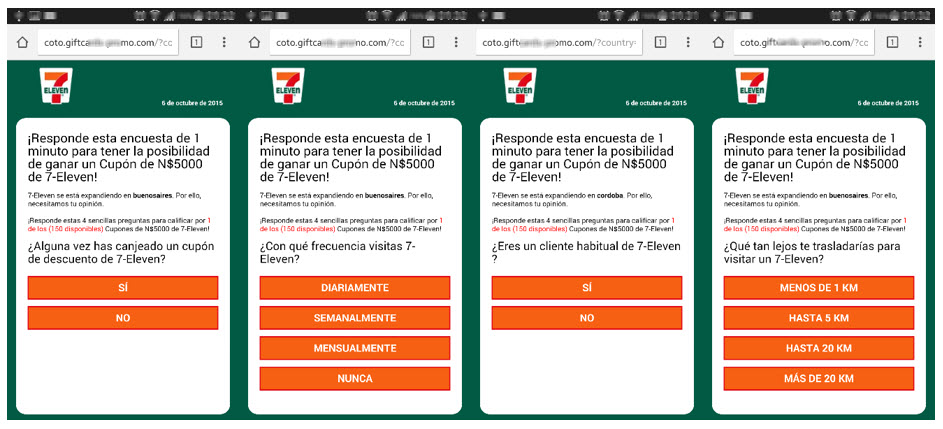
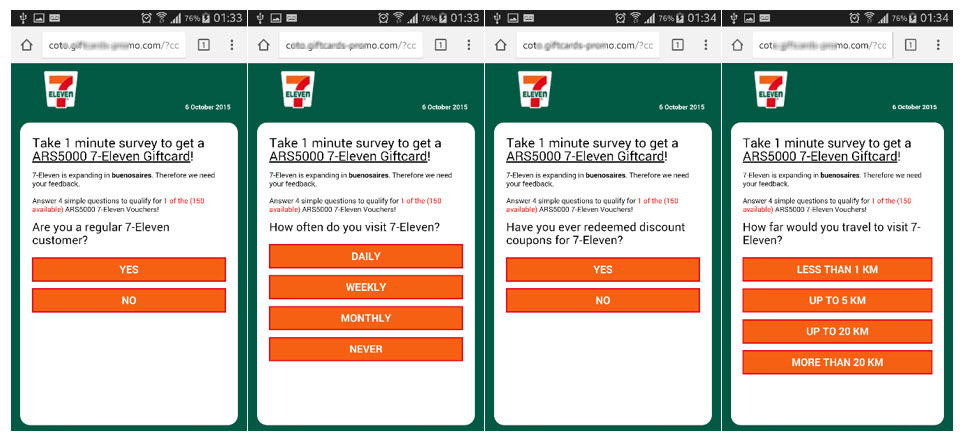
7-Eleven
7-Eleven is another international chain used for this type of fraud. With its 52,000 convenience stores distributed in 16 countries, it specializes in the sale of commodities and has a strong presence in the USA and Asia.
Take a look at this example in Spanish; we’ll see below how the language is changed in case the user receiving the message speaks English or another one:
Another affected company in the same line of business was the Walmart supermarket chain, which has 11,000 stores in 28 countries. The subdomain used in this case was: walmart.giftc*******.com
Following the path of the scam
As can be seen, the templates used are very similar in all the examples – they were only customized according to the colors and logos of each brand.
They all share the same survey model, which is determined by default according to the IP address of the visitor. This IP address gives cybercriminals information on the country and language used by the victim.
If we examine the first request, we notice it uses the GET method to retrieve parameters, as can be seen in the picture below:

In this way, it is evident that these campaigns are flexible, since they can change the value of the language parameter - in this case from "es" (Spanish) to "en" (English) - and we can see the template for the fake survey automatically changing its language:
The next step in the surveys is to make the users share the initial link with 10 WhatsApp contacts. By limiting the time in which the survey can be completed, the cybercriminals prevent the victim from becoming anxious – they do not have time to be suspicious of a possible fraud.
This technique may not be that common, but it is clearly effective and we will probably start to be it being used more frequently in the future.

The last part of the campaign includes different types of frauds to mislead the user, such as subscription to Premium SMS numbers and installation of Potentially Unwanted Applications.
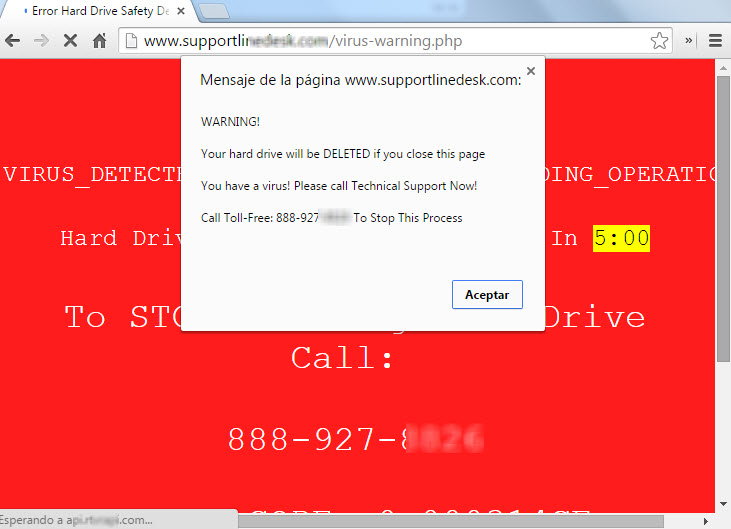
In other cases, if you access from a PC and your IP address is located in the US, you are redirected to rogue pages with warnings about a virus infecting the system, with pop-up messages and a very persistent audio alert telling you to dial a phone number to receive support.
And they assure that if you don't do it or if you try to close that page, you will lose all the content on your hard drive. Of course this is completely false, as well as the survey prizes or the gift certificates - they are mere social engineering tactic to make the user perform some kind of action.
In conclusion
It is interesting to highlight the large amount of resources used in these operations, considering the fact that they target different countries, currencies and even languages.
With the flexibility and automation of these attacks, added to the type of companies involved and considering that there have not been many similar security incidents in the past, it is only natural that there is a huge number of users who have already become victims but have not yet noticed.
This type of scam shows why education is the first layer of protection. In that sense, we intend to warn users and help them reflect on these new trends that use old techniques in modern communication channels such as WhatsApp.
We have already found about 10 different brands used in this campaign, whose purpose was to propagate globally, and we will most likely see new cases as days go by. We will keep you updated on the developments of this trend of multi-brand scams.