Guess who hasn't been using two factor authentication to protect its social media accounts?
Twitter and YouTube accounts belonging to Central Command - the group responsible for United States' military operations in the Middle East - were hijacked yesterday by hackers claiming to back Islamic State.
In a series of messages posted on the @CENTCOM Twitter account , the pro-ISIS hackers claimed to have broken into US military networks and stolen information.
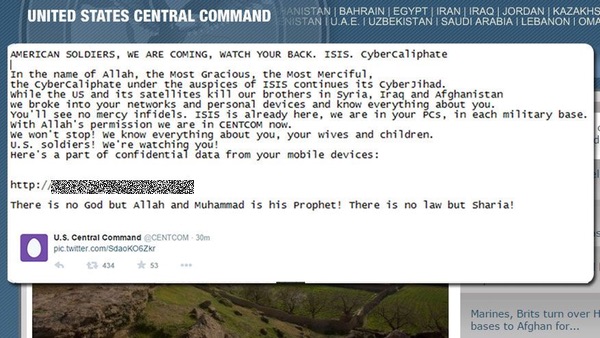
For some time, anyone on Twitter could read bizarre messages on the @CENTCOM account including "I love you ISIS".
It's bad enough having your social media accounts compromised, of course, but then the hackers began to post what they claimed were leaked military documents.
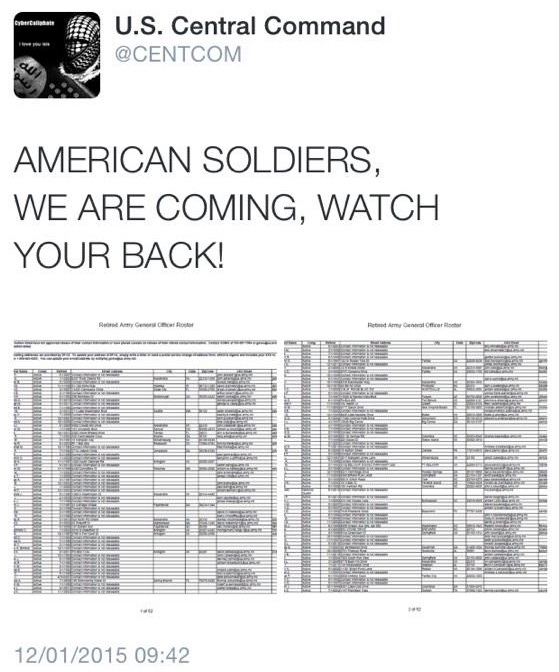
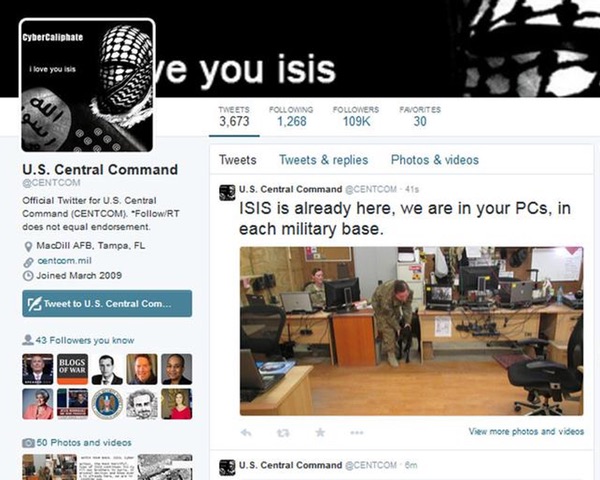
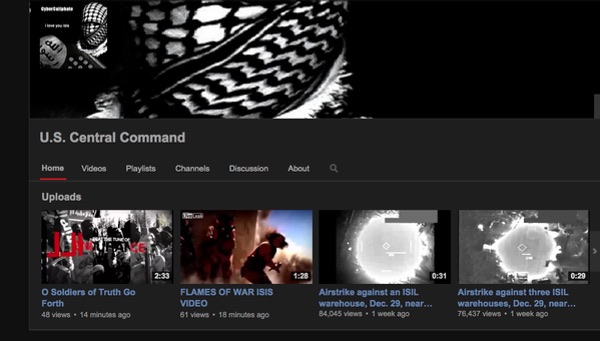
And it wasn't just Central Command's Twitter account that was being abused. Its YouTube channel had also been broken into, with the hackers uploading videos and changing images:
In less than an hour, Twitter had suspended the compromised account.
Of course, there is a vast difference between hacking into a sensitive military network and compromising a handful of social media accounts.
In a press statement, CENTCOM was at pains to point out that it did not believe that any sensitive information had been posted to the accounts, and that its own servers had not been hacked:
U.S. Central Command's Twitter and YouTube sites were compromised for approximately 30 minutes. These sites reside on commercial, non-Defense Department servers and both sites have been temporarily taken offline while we look into the incident further. CENTCOM's operational military networks were not compromised and there was no operational impact to U.S. Central Command. CENTCOM will restore service to its Twitter and YouTube accounts as quickly as possible. We are viewing this purely as a case of cybervandalism.In the meantime, our initial assessment is that no classified information was posted and that none of the information posted came from CENTCOM's server or social media sites. Additionally, we are notifying appropriate DoD and law enforcement authorities about the potential release of personally identifiable information and will take appropriate steps to ensure any individuals potentially affected are notified as quickly as possible.
Precisely how the accounts were hacked isn't clear. It's possible that keylogging malware which infected Central Command's social media team managed to grab their passwords or that a hack of a military computer revealed a document containing the passwords, but it's perhaps more likely that a member of the team was phished or made the mistake of using an easy-to-guess password or reusing the same password on more than one site.
None of this would have allowed the hackers to gain access to the Twitter and YouTube accounts though if two factor authentication (2FA) had been enabled.
Twitter's 2FA (known as login verification) requires users to not only give a username and password to connect to the site, but also requires users to enter a one-time-password which is either sent to them an SMS message to their mobile phone, or via a smartphone app like Google Authenticator.
The principle is that even if a hacker comes to learn your password, chances are that they don't have access to your mobile phone and so will still not able to access your account.
YouTube, like other Google services, also has two-factor authentication (although they call it two-step verification) which works in a similar way.
Frankly, you're playing a dangerous game if you run social media accounts and aren't using some form of 2FA to protect them - especially if the accounts represent an organisation or brand where reputational damage is possible.




