Security experts at ESET have released their latest research into the notorious TorrentLocker malware, which has infected thousands of computer systems around the world, taking data hostage and demanding a ransom be paid to ensure its safe return.
 In a technical white paper, researcher Marc-Étienne Léveillé describes how the TorrentLocker family of ransomware (which is known as Win32/Filecoder.DI by ESET security products, but which the malware's creators would apparently rather be known as "Racketeer") has evolved since its first sighting in February 2014.
In a technical white paper, researcher Marc-Étienne Léveillé describes how the TorrentLocker family of ransomware (which is known as Win32/Filecoder.DI by ESET security products, but which the malware's creators would apparently rather be known as "Racketeer") has evolved since its first sighting in February 2014.
As months have passed, TorrentLocker (named because early versions of the malware set a Registry entry which referenced the Bit Torrent application) has become more sophisticated and automated its systems.
For instance, in September Finnish researchers at Nixu Oy detailed a method by which victims of TorrentLocker could recover the contents of their encrypted files, without handing any money over to the criminals behind the attack.
Predictably, once they realised that it was possible to extract the keystream, the authors of TorrentLocker released a new version which changed their encryption methodology, and shut the door on the loophole immediately.
Another example is that at first victims were required to send emails to the criminals behind the malware to make payments and request decryption keys. Today, this has been automated via a user-friendly payment page, explaining how to pay with Bitcoins to receive the decryption software.
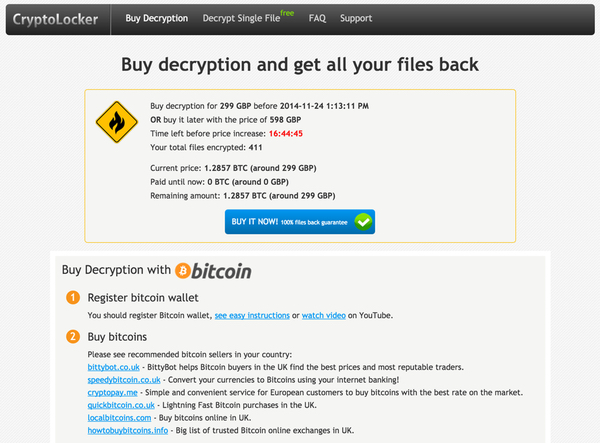
But although the malware has become more sophisticated, in other ways it appears less professional.
Some of the screens displayed by TorrentLocker refer to "CryptoLocker" instead. Is this a case of laziness on the malware creator's part, or a deliberate attempt to dupe users into searching for information about an unrelated (albeit just as notorious) piece of ransomware?
Furthermore, the gang behind TorrentLocker does not appear interested in maximising its potential pool of victims by striking at computer users around the globe.
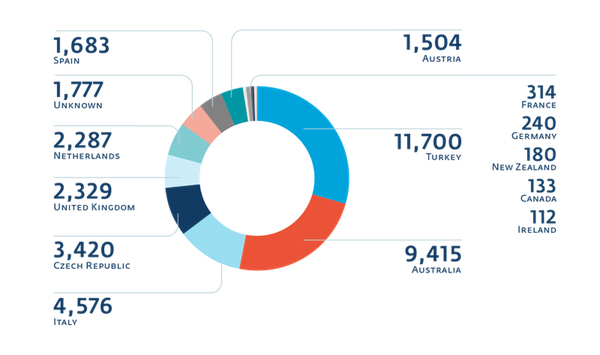
ESET researchers have determined that spam campaigns used to distribute TorrentLocker have only targeted specific countries.
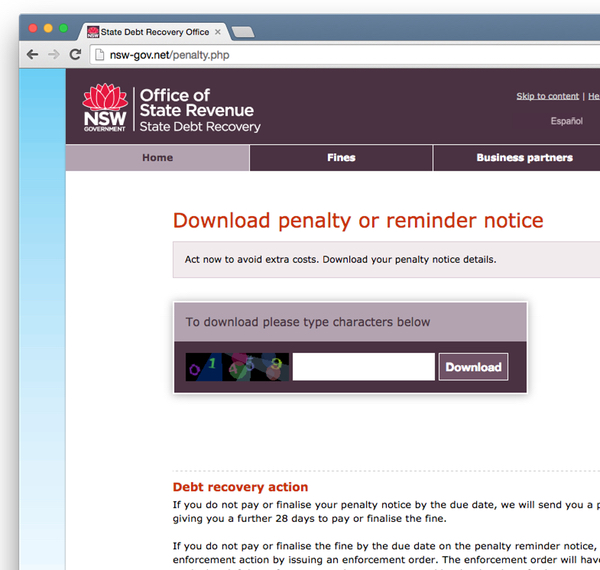
Typically, the malicious emails arrive in the form of a bogus message claiming to relate to an unpaid invoice, the delivery of a package, or a fine for an unpaid speeding ticket.
The following list of countries targeted by the malicious email campaigns is notable for its surprising exceptions (the United States, for instance, is nowhere to be seen):
- Australia
- Austria
- Canada
- Czech Republic
- Italy
- Ireland
- France
- Germany
- Netherlands
- New Zealand
- Spain
- Turkey
- United Kingdom
What the technical paper makes clear, however, is that the rewards to be made through the TorrentLocker malware are considerable. ESET's research indicates that even though a mere 1.45% of victims are paying the ransom (570 of 39,670 infected systems) that has still made the criminals between $292,700 and $585,401 in Bitcoins.
And, according to data gathered from TorrentLocker's C&C (command and control) servers, a jaw-dropping 284,716,813 documents have been encrypted to date.
One has to hope that a fair proportion of the victims have access to a recent, clean backup from which they can restore their precious data.
For much more detailed information about TorrentLocker, be sure to have a look at the technical white paper from ESET.




