LastPass has gone public about a couple of security holes that were found in its popular online password management software.
That's enough to send a shiver down the spines of the many internet users who trust the service to store its passwords securely, but the company says that there is no need to panic.
In a blog post entitled "A note from LastPass", the company has given brief details of the flaws found in its password manager for Chrome, Firefox, Opera and Safari.
(By the way, do you feel as cynical as me about how some vendors reporting security vulnerabilities in their products love to downplay the seriousness by not referring to any words like "security" or "vulnerability" in the headlines of their advisories?)
Bookmarklet vulnerability
The first vulnerability isn't really in the main LastPass product at all, but instead in an add-on known as Bookmarklets.
LastPass Bookmarklets are small snippets of JavaScript code that install as a bookmark of "favourite" in your browser.
Chances are that you would only be using Bookmarklets if you wish to integrate LastPass more tightly with the mobile Safari browser on iOS, or if you weren't using one of the major browsers that LastPass officially supports.
If you click on a Bookmarklet, you can execute code on the webpage that you're viewing. That could, of course, be useful if there is a login form on the webpage and no other easy way to access your password manager, but what happens if the webpage you are running the code on is itself malicious?
Zhiwei Li, a security researcher at UC Berkeley, found a method by which (if a user clicked a bookmarklet while visiting an untrustworthy website) passwords for other sites could be extracted from LastPass and put in the hands of criminal hackers.
A research paper by Zhiwei depicts an untrustworthy site tricking a Bookmarklet into revealing the user's Dropbox password - although this could actually be repeated to extract every password stored in a victim's LastPass vault.
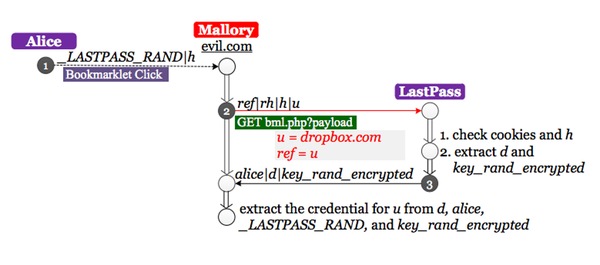
LastPass says that Bookmarklets are "actively used by less than 1% of the user base", and is keen to underline that the threat is small, and that it has seen no evidence of malicious exploitation:
"If you are concerned that you’ve used bookmarklets before September 2013 on non-trustworthy sites, you may consider changing your master password and generating new passwords, though we don’t think it is necessary."
One Time Password (OTP) vulnerability
In this targeted attack, Zhiwei showed that it might be possible to exploit LastPass's One Time Password (OTP) feature - normally used when a user is logging into their LastPass vault on a computer that they do not trust (such as one that is shared with other users), and that might be harbouring keylogging spyware.
OTPs self-destruct after one use, so even if a malicious hacker grabs the one you use to access your passwords - it shouldn't be any use to them.
However, Zhiwei demonstrated that if an attacker knew their victim's LastPass username they could exploit the feature to extract a directory of all the sites for which the user was storing passwords in LastPass. Fortunately, it wouldn't give hackers access to a users' actual passwords, but it would allow them to make off with an encrypted copy of the password database and allow them to delete credentials stored in the database.
"Regarding the OTP attack, it is a “targeted attack”, requiring an attacker to know the user’s username to potentially exploit it, and serve that custom attack per user, activity which we have not seen. Even if this was exploited, the attacker would still not have the key to decrypt user data. If you’d like to check your current OTPs you can do so here"
 The good news is that the people who found the security vulnerabilities were Zhiwei and his fellow researchers at UC Berkeley, rather than a cybercriminal. Zhiwei is said to have acted responsibly with the information, and - according to LastPass's statement - the company "doesn't have any evidence they were exploited by anyone beyond [Zhiwei] and his research team."
The good news is that the people who found the security vulnerabilities were Zhiwei and his fellow researchers at UC Berkeley, rather than a cybercriminal. Zhiwei is said to have acted responsibly with the information, and - according to LastPass's statement - the company "doesn't have any evidence they were exploited by anyone beyond [Zhiwei] and his research team."
What strikes me as a little unusual about the disclosure of these vulnerabilities is that they were first reported (and indeed patched) back in the fall of last year. It has taken almost a year for them to become public.
LastPass says that Zhiwei only tested the exploits on dummy LastPass accounts, and because it found no evidence of malicious exploitation, and addressed the issues immediately, the company refrained from discussing the research until after it had been published.
All LastPass users should be grateful that the company addressed the security vulnerabilities so quickly, and feel reassured that there is no evidence that anyone's password vaults were compromised.
Although flaws and issues are found from time to time with password managers, as detailed in Zhiwei's research which looks at other password management products besides LastPass, I remain a strong believer that for the typical computer user decent password management software is going to be a more secure way of living a life online than relying on their brain and common sense to generate and keep secure their passwords.
Get yourself a password manager, choose a strong, hard-to-crack master password, enable two factor authentication and start taking your online privacy more seriously.
What do you think? Do you trust password management software? Or do you prefer to manage your passwords in a different way? Let us know your opinion by leaving a comment below.




