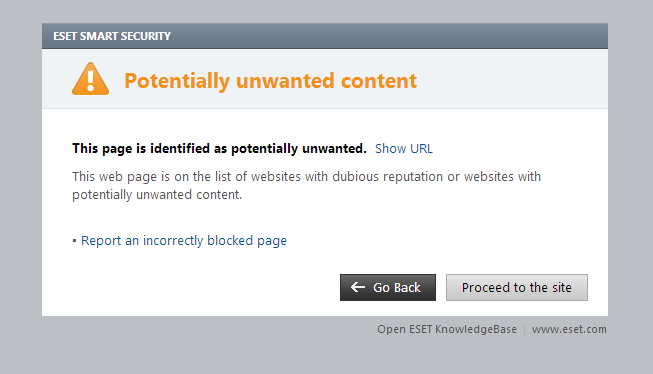
If you’re a regular reader, you may have noticed that I’ve written a lot about support scams on this blog. So while I couldn’t resist yet another, based on a twist flagged by Paul, commenting on one of my articles here, this one went up on Graham Cluley’s blog. Paul’s comment told us how he was cold-called by a scammer who tried to convince him, using the well-known ASSOC/CLSID ploy, that he (the scammer) really knew something about Paul’s PC, and that Paul should run some remote access software linked via a web site calling itself the Windows Service Center. Fortunately, Paul declined to run the software without checking it with security software, and the scammer lost his temper, thus pretty much giving the game away. It's worth bearing in mind, though, that for this part of the scam, the fraudster usually directs the victim to a legitimate program like AMMYY, so security software won't detect it as malware, though it may detect it as Possibly Unwanted (as ESET does the site in question) or Possibly Unsafe.
What happened when Paul told us about it is recounted in more detail in the article on Graham’s blog.
Sadly, by the time this article goes up, Wimbledon will be over, so this is my last chance to get in a topical pun or two about service games and double faults. (And I still haven’t seen a tennis scam, by the way.) Nevertheless, this particular ball is still in play. This morning, I received a phone call from ‘Talia’ (I think), representing the Computer Support Unit, about my Windows computer. When I asked her which Computer Support Unit that would be, she told me it was the Windows Service Center. It’s not often I get the chance to say “You mean the scam site that just got closed down?” Strangely, the phone went down at that point.
Hat tips here to my colleague Aryeh Goretsky, who actually got in touch with the site provider whose services were being misused in this particular scam to alert it to the misuse of the subdomain, and also to webs.com for their timely action. But let’s not get too bullish about this: it’s all too likely that this ploy will be tried again, using more than one provider and similar official-sounding site names and domain names. So the essential point to take away from this is not ‘avoid the Windows Service Center’ but ‘be aware that it’s very easy to register a site name that sounds more legitimate than it really is.’
On the other hand, it’s probably even more important to realize how unwise it is to give remote access to your PC to anyone who asks for it, just because they ring you out of the blue and claim they can help you with a PC problem you almost certainly don’t have.
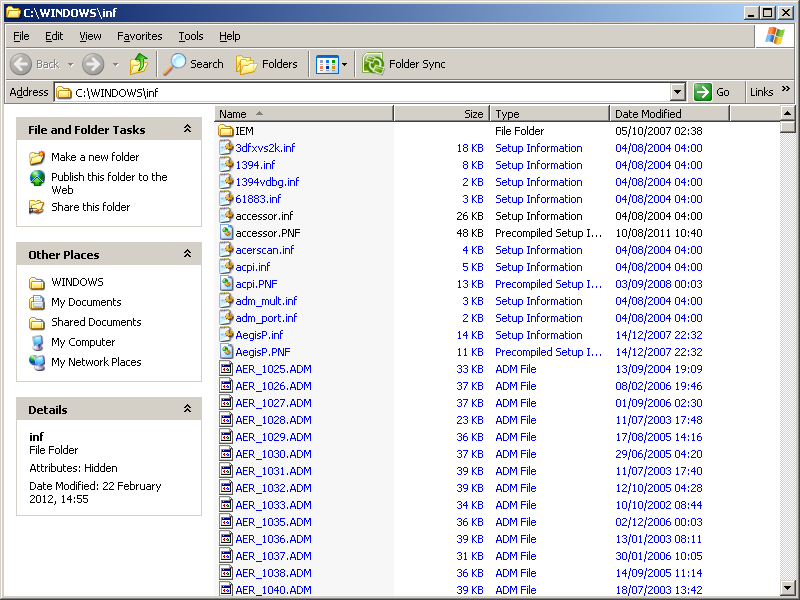
Just to end on a note of (slightly sour) amusement, Tyler, who commented on another of my support scam blogs (about other gambits used by support scammers to persuade their victims that they have a virus infection - Support Scammers (mis)using INF and PREFETCH), tells us that a scammer who called him tried to persuade him that INF stands for infection. It doesn’t, of course, and has nothing to do with detecting viruses. It actually shows the contents of a folder normally named C:Windows\Inf and contains files used in installing the system.
You can find most of the information you’re ever likely to need (and more) about support scams and the misuse of the Windows brand and utilities, by checking out some of the links on the AVIEN scam resources page. You might also enjoy another article I contributed to Graham’s blog linking to some articles by Dr Alan Solomon recounting how he’s been messing with the heads of support scammers who’ve been unlucky enough to find his phone number.
David Harley
ESET Senior Research Fellow