What is ransomware?
Ransomware is the generic term for any malicious software that, as its name suggests, demands a ransom be paid by the computer's user.
Why would you want to pay a ransom?
Because the ransomware has done something unpleasant to your computer, and potentially to your data.
For instance, it might have encrypted your documents and demanded that you pay a ransom to unlock access to them. This type of ransomware is known as a filecoder.
The most notorious filecoder is Cryptolocker. (Numerous versions of this are detected by ESET antivirus products as Win32/Filecoder).
How would my computer get infected by ransomware like Cryptolocker?
A typical method of infection would be to open an unsolicited email attachment or click on a link claiming to come from your bank or a delivery company.
There have also been versions of Cryptolocker seen which have been distributed via peer-to-peer files-sharing networks, posing as activation keys for popular software like Adobe Photoshop and Microsoft Office.
If your computer becomes infected, Cryptolocker hunts for a wide range of file types to encrypt - and once its dirty work has been done, displays a message demanding you electronically transfer the cash to have the files decrypted.
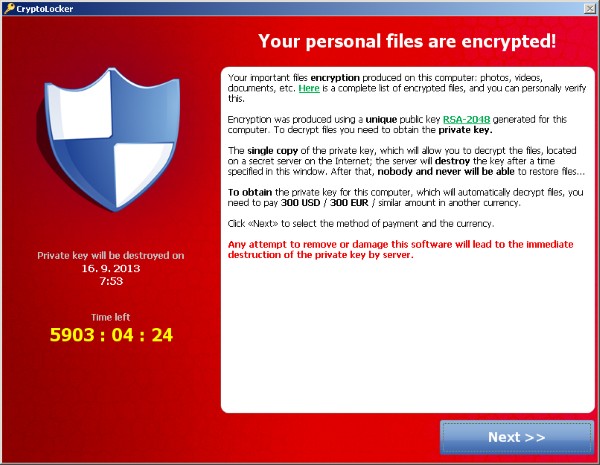
In some cases, the lockscreen may even include a live feed of what your computer's webcam is currently looking at.

It is unnerving to unexpectedly see yourself sitting in front of your computer, and might help to trick less technical users into believing that they really are being observed by the authorities.
I've also heard of scareware. What's that?
Scareware is software that tries to scare you into taking a particular course of action.
Most commonly, scareware will pretend to be an anti-virus product that displays a warning of security issues on your computer or smartphone in an attempt to trick you into paying the scammers or downloading further dangerous code from the net.
In some cases the fake anti-virus might actually present itself with the name of a genuine security firm, in an attempt to increase the number of people who are duped into making a bad decision.
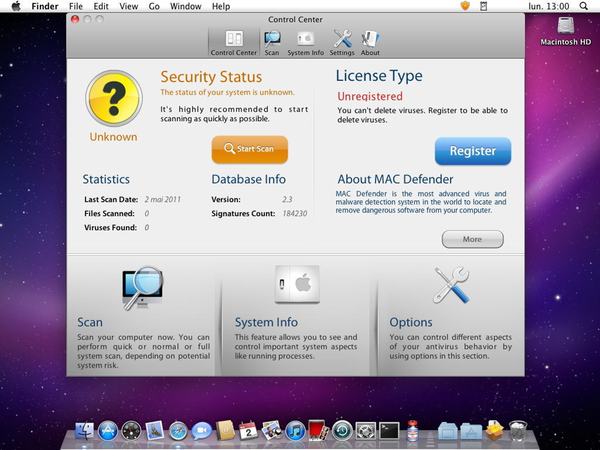
Like ransomware, scareware can be written for any operating system. Ironically, some instances of fake anti-virus scareware have had more impressive user interfaces than the legitimate products they are attempting to ape!
In a sinister development, some scareware - if unsuccessful frightening you into making an unwise purchase - might resort to ransomware tactics to demand money with more obvious menace.
What happens if, after my computer gets hit by ransomware, I don't pay up?
In the case of many ransomware attacks there is a deadline for payment - and if you don't pay up in time you could permanently lose access to your files.
Is file-encrypting ransomware the only kind of ransomware?
No, there is also lockscreen ransomware. That's a type of ransomware that locks your computer, preventing you from doing anything with it until a ransom has been paid.
Lockscreen malware might use underhand psychological tricks to hurry you into paying.
For instance, sometimes the lockscreen message might pretend to come from your country's police force, and claim that the authorities are demanding you pay a fine because images of child abuse, zoophilia, or evidence of visiting illegal websites and pirated software has been found on your computer.
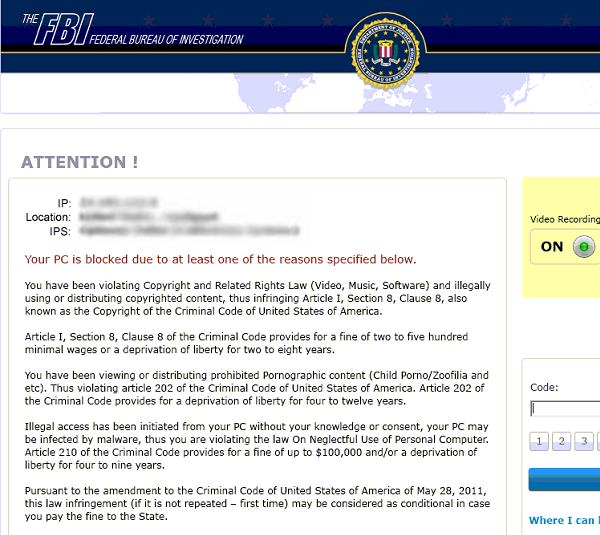
One of the most commonly encountered families of ransomware that locks users' computers while posing as a message from the authorities is Reveton.
And do people actually pay the ransom?
Yes, in many cases they do.
Imagine if you didn't have a verified backup from which you can restore your sensitive or company files. You might very well think it is worth spending a few hundred dollars to regain access to your data.
Corporate users may not care as much about lockscreen malware (after all, they hopefully have backups and access to other hardware), but it's easy to imagine how home users could be scared by the fake police threats or the mention of child abuse images into paying the ransom rather than taking their computer to their local computer repair shop.
So does paying the ransom decrypt your data?
Yes, generally it does restore access your data If you think about it, that's good business sense by the criminals. If word got around that the attackers don't keep their side of the bargain, nobody would ever pay the ransom.
However, paying the ransom doesn't mean that you're safe and out of the woods. The criminals might leave malware on your computer, and now know that you are the kind of person who is prepared to pay hard cash to regain access to their computer or data. In short, you could be targeted again in the future.
So if I am a victim of ransomware, should I pay the ransom?
We wouldn't recommend it. Remember, there is nothing to stop the criminals behind the attack from demanding more money from you. If you pay the ransom you are helping create a new market for online criminals, which might lead to more ransomware and other cybercriminal attacks in future.
Instead, learn from the lesson by putting better protection in place and ensure that you have a proper backup regime to recover your essential files should you be unlucky enough to be hit again.
Can't my antivirus simply remove a ransomware infection?
Yes, in most cases good security software should be able to remove ransomware from your computer. But that isn't the end of your problems.
Because, if the ransomware which infected your computer was a filecoder your files are still encrypted. Security software might be able to decrypt your sensitive information if a simple filecoder was used in the attack, but files hit by a more sophisticated example of ransomware like Cryptolocker are impossible to decrypt without the right key.
Prevention is the best medicine.
So, filecoders which encrypt your sensitive files are worse than Lockscreen malware?
Yes, in most situations file-encrypting ransomware is probably harder to recover from than other forms of ransomware. However, if you have a backup that wasn't impacted by the attack it shouldn't be too difficult to be up and running again quickly.
Frankly, the worst malware is the one that has infected *your* computer!
Is filecoder ransomware on the rise?
You have probably guessed the answer to this one.
Yes, there is more and more file-encrypting malware seen by ESET researchers all the time - and has been a steady rise over the last year.
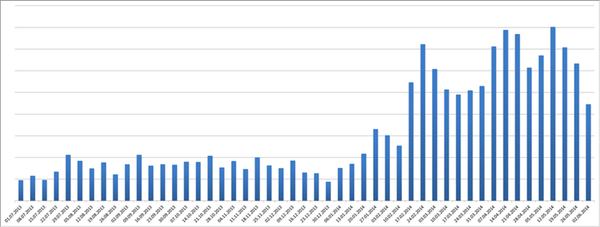
Growth in Filecoder prevalence since July 2013
What operating systems have been hit by ransomware attacks?
 In theory, there's nothing stopping online criminals from writing ransomware for any operating system - but the majority of the attacks have targeted Windows users. Cryptolocker, for instance, has only been seen for the Windows platform.
In theory, there's nothing stopping online criminals from writing ransomware for any operating system - but the majority of the attacks have targeted Windows users. Cryptolocker, for instance, has only been seen for the Windows platform.
However, ESET researchers recently detected Android/Simplocker, the first file-encrypting Trojan to demand a ransom from Android users via a control centre hidden on the anonymized Tor Network.
Clearly things are getting more sophisticated in the world of ransomware, even on smartphones.
So smartphones could be at risk too?
Correct. Of course, the malware threat is much smaller on even jailbroken iOS devices than it is on Android.
We Live Security's Rob Waugh has put together a great guide about how to keep your Android device safe from ransomware.
Where can I learn more about ransomware?
Further reading:
- ESET Analyzes First Android File-Encrypting, TOR-enabled Ransomware
- Android malware: how to keep your device safe from filecoders (and everything else)
- GameOver Zeus and Cryptolocker: Law enforcement hits gang responsible
- “Tens of millions” at risk from Filecoder due to “mass email spam event” targeting small businesses, British police agency warns
- Back up now! Warning over new wave of Filecoder infections hitting U.S.
- Don’t pay up! How to avoid ransomware threats – and how to fight back
- American law firm admits entire server of legal files fell victim to Cryptolocker
Podcasts:
- Listen to this five minute podcast by ESET expert Aryeh Goretsky, where he even sheds light on the AIDS Information Trojan seen in 1989, probably the very earliest example of ransomware.




