We still have comments and reports coming in from our blog readers concerning the ongoing problem with scammers, almost invariably based in call centres in India, trying to persuade them that their PCs are infected with viruses or compromised by hackers. Here are some thoughts in response to a recent comment to one of my earlier blogs on the timeworn topic of the support scam.
The intended victim was influenced by recent reports relating to the recent Internet Explorer bug into believing that it was possible that his machine had been infected as a consequence of that bug, and the scammer used the old ASSOC trick to convince him that one of the lines displayed by ASSOC showed his computer’s ‘unique ID’:
.ZFSendToTarget=CLSID\{888DCA60-FC0A-11CF-8F0F-00C04FD7D062}
ASSOC is a command that displays the program and/or functionality ASSOCiated with a specific file type. This particular CLSID is frequently misrepresented by scammers as being a unique identifier of the victim’s system and/or a license ID for the Windows operating system. In fact, a CLSID is an identifier that is unique not to a particular PC, but to a COM class object, which means that it will be the same on any Windows system where that object can be found. In other words, there are many millions of Windows computers where running the ASSOC command will show exactly the same text somewhere in its display. It does not represent a unique ID string for either the PC or for a specific installation of Windows. (Indeed, our reader subsequently found the same string on his other PC, as you’d expect.)
Typical ASSOC output: the string the scammers like to use is flagged in red
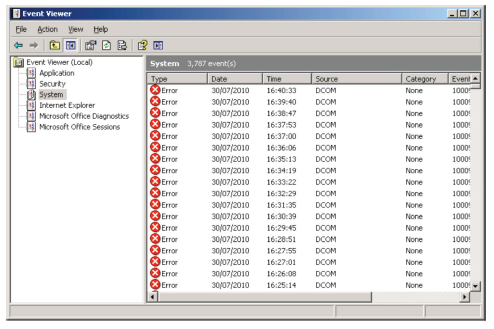
Next, the scammer persuaded him that there were problems on his PC by asking him to run EVENTVWR to prove that there were ‘problems’ on the system. Event Viewer is a tool that keeps a system log. It will take you to a screen that shows you various system events, some of which will indeed be problems, though they’re usually transient errors and glitches that have already come and gone.
Typical Event Viewer Output
As is usually the case, the scammer was misrepresenting log entries as something more serious in order to persuade the intended victim to install remote access software such as AMMYY or TeamViewer to allow the scammer – or one of his ‘technician’ friends – to access the victim’s machine. When the scammer showed him the Windows ‘process tree’ – I guess using Task Manager – it was claimed that the running process csrss.exe was a Trojan being exploited by Mexicans to gain access to the PC and to the victim’s internet. (What the residents of Mexico have done to deserve such a slur, I can’t imagine, but at least I finally have an excuse to use the expression ‘Mexican Standoff’ in a blog title, even if the analogy is a bit strained.) In fact, while Trojans masquerading as csrss.exe are not unusual, the (real) file is the user mode part of the Client/Server Runtime Subsystem, an essential Windows system service. In other words, you need it to be running.
The scammer used the netstat utility to ‘prove’ his assertion, presumably with output something like this:
C:\>netstat -n
Active Connections
Proto Local Address Foreign Address State
TCP 192.168.1.76:64617 173.194.66.125:5222 ESTABLISHED
TCP 192.168.1.76:64694 23.62.2.51:443 ESTABLISHED
TCP 192.168.1.76:64996 31.13.72.65:443 ESTABLISHED
TCP 192.168.1.76:64997 70.167.14.17:443 ESTABLISHED
TCP 192.168.1.76:65041 173.252.102.241:443 ESTABLISHED
This type of output has been used before by scammers to suggest that entries under ‘Foreign Address’ represent some sort of external attack. In fact, they simply represent legitimate connections between the local machine (in this case 192.168.1.76) and various remote systems.
In this case, fortunately, the intended victim realized that he was being scammed and denied the scammer further access.
On a related note…
For anyone who remembers an article I put up here – Facebook Likes and Cold-Call Scams – with Martijn Grooten of Virus Bulletin and Steve Burn of Malwarebytes and concerning dubious advertising on Facebook and elsewhere by tech support sites, you may be interested in articles here and here. They’re concerned with an initiative involving Facebook and others to reduce the impact of false advertising by tech support scammers who’ve gone beyond cold-calling to trying to attract people who are actively looking for help.
And an Ars Technica article – Inside the US government’s war on tech support scammers – describes how an FTC (Federal Trade Commission) investigator gathered evidence that helped towards getting a temporary restraining order against a company called PCCare247. An interesting variation on the netstat gambit described above was used by the scammer in the conversation recorded here. Having gained access to the supposed victim’s PC, he flagged a connection with a system outside the US with netstat that, according to him, showed that the PC was being hacked remotely. You won’t be surprised that the FTC concluded that:
This was a brazen lie; forensic examination would later conclude that the single connection displayed by netstat was in fact the remote access tool that Yakeen was using at that moment to control Novick’s machine.
TREE with low-hanging fruit
The article also cites an instance of the tree command being misused as evidence of the presence of malware. According to a comprehensive list of misused utilities published by our friends at Malwarebytes, the DOS commands dir and tree are frequently misrepresented as performing a full virus scan. As most readers of this blog will know, all they actually do is give listings of files and directories. Clearly, there are lots of computer users nowadays who have never seen an MS-DOS command prompt and don’t know about what we computing dinosaurs regard as basic DOS commands. It seems that support scammers are finding – or at least hoping to find – victims who can be conned using the most primitive of gambits because they don’t have decades of experience of command-line utilities.
Typical Output from DIR
Conclusion: Avoiding the Gobbledygook
We can’t expect the average user to learn all about legacy utilities left over from obsolescent operating systems. But they can usually bypass these attempts to blind them with pseudo-science and technical-sounding gobbledygook by remembering a handful of basic rules.
- Don’t allow anyone who rings you out of the blue to connect to your PC for any reason. It’s like meeting someone in the street and having them tell you that you have mice under your floorboards, but if you give them your house keys and credit card they’ll go and sort it out for you.
- Don't believe them when they say they know about the health of your PC. Tech support scammers don’t really know anything about your system, any more than someone you pass in the street knows about the state of your house. They may know your name and address – they can get that info from directories and marketing lists – but they don’t know anything else. All the CLSID and DIR nonsense is to con you into trusting the untrustworthy, by convincing you that they know more than they really do.
- Don't take it for granted that any stranger who calls you out of the blue is the person they claim to be. If they claim to be representing your provider, or Microsoft, or your bank, it’s their responsibility to provide proof of their identity. Even if they give you information that you believe only your provider would know, consider calling the organization concerned back on a phone number you know to be genuine.
*That's DOS as in Disk Operating System and, specifically, MS-DOS (Microsoft's pre-Windows operating system for PCs), not Denial of Service. Though that could apply too.
David Harley
ESET Senior Research Fellow