If you run a website on a Linux server or are responsible for the security of your company's Unix servers, there's something very important you should do right now.
Researchers at ESET, in collaboration with CERT-Bund, the European Organization for Nuclear Research (CERN), the Swedish National Infrastructure for Computing and other agencies, have uncovered a widespread cybercriminal operation that has seized control of tens of thousands of Unix servers.
And if your system is found to be infected, experts strongly recommend you re-install the operating system, and consider all credentials used to log into the machine as compromised. In short, if you are a victim, all passwords and private OpenSSH keys should be changed.
The attack, which has been given the name "Windigo" after a mythical creature from Algonquian Native American folklore, has resulted in over 25,000 Unix servers being hacked, resulting in 35 million spam messages being sent each day from compromised machines.
That would be bad enough, normally.
But in this case, malicious hackers have also been using hijacked web servers to infect visiting Windows PCs with click fraud and spam-sending malware, and display dating website adverts to Mac users.
Even smartphone users don't escape - finding their iPhones redirected to X-rated content, with the intention of making money for the cybercriminals.

ESET's security research team has published a detailed technical paper into "Operation Windigo", and says it believes that the cybercrime campaign has been gathering strength, largely unnoticed by the security community, for over two and a half years.
"Over 35 million spam messages are being sent every day to innocent users' accounts, clogging up inboxes and putting computer systems at risk. Worse still, each day over half a million computers are put at risk of infection, as they visit websites that have been poisoned by web server malware planted by Operation Windigo redirecting to malicious exploit kits and advertisements," said ESET security researcher Marc-Étienne Léveillé.
In its attempt to hijack servers and infect computers, Windigo uses a complex knot of sophisticated malware components including Linux/Ebury (an OpenSSH backdoor and credential stealer that was the subject of a detailed investigation by ESET researchers earlier this month), Linux/Cdorked, Perl/Calfbot, Linux/Onimiki, Win32/Glubteba.M, and Win32/Boaxxe.G.
During a single weekend, ESET researchers observed more than 1.1 million different IP addresses going through part of Windigo's infrastructure, before being redirected to servers hosting exploit kits.
An analysis of the visiting computers revealed a wide range of operating systems being used.
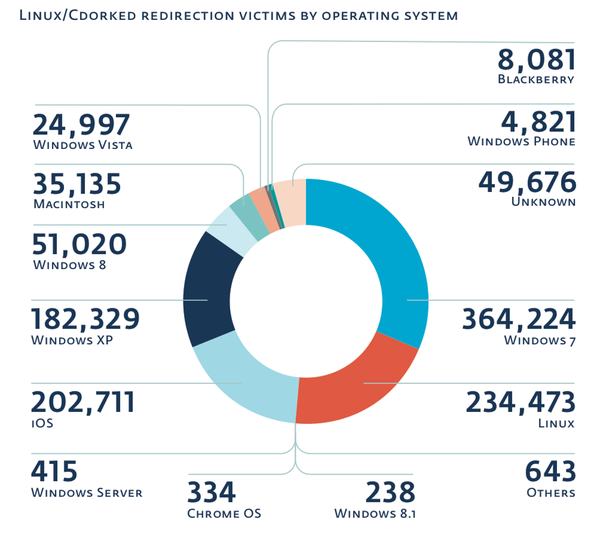
This in itself threw up some light relief, as researchers discovered that "23 people apparently still browse the Internet on Windows 98, and one person even does it on Windows 95."
Léveillé and his fellow researchers are appealing for Unix system administrators and webmasters to run the following command which will tell them if their server is compromised or not:
$ ssh -G 2>&1 | grep -e illegal -e unknown > /dev/null && echo "System clean" || echo "System infected"
That single Unix command should quickly tell you if your system is seriously compromised or not by Windigo, and whether you need to take steps to clean-up and better protect your servers in future. Further details on how to tell if your server has been compromised are available included in ESET's technical white paper on Operation Windigo [PDF].




