Sometimes it feels monumentally difficult to convince internet users to get smarter about their passwords.
One of the biggest problems is password reuse.
Most people use the same password for multiple websites. In some cases, users will use the same password for *every* website they access.
This leads to big problems. Because if you use the same password at website X, Y and Z... it only requires hackers to break into website X and steal its passwords for your accounts on website Y and website Z to also be put at risk.
Maybe X, Y and Z have done their homework, realised that it's important to build a secure, hardened website, and kept up to date with their software patches. Maybe they have great security in place and hackers' attempts to break in end in failure.
Well, there's still a problem. And that's the user's computer.
 If your computer has been infected by keylogging malware then a criminal hacker can easily hoover up your password, and try it out on the sites. Indeed, many banking Trojans do precisely this - effectively looking over your shoulder everytime you enter a password into an online form and grabbing it for later exploitation.
If your computer has been infected by keylogging malware then a criminal hacker can easily hoover up your password, and try it out on the sites. Indeed, many banking Trojans do precisely this - effectively looking over your shoulder everytime you enter a password into an online form and grabbing it for later exploitation.
Maybe you are running a top anti-virus product on your computer, and are diligent about keeping your security in place, are careful about what programs you install, and your software updates are always nice 'n' fresh.
Good for you. But there are still problems.
Because what's to stop you being phished? Are you smart enough to tell the genuine emails from the bogus ones? Are you sure?
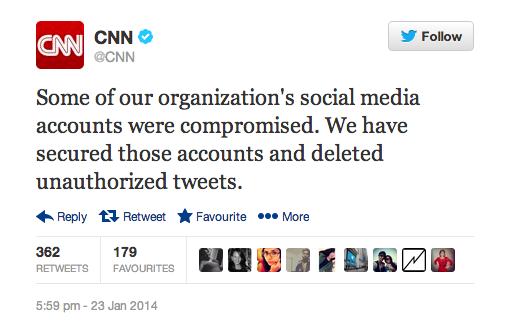
Because the staff at Forbes, CNN, Washington Post, and countless others certainly weren't.
They all got tricked by the Syrian Electronic Army, who forged emails to *look* like they were genuine, but where the links took staff to phoney phishing websites designed to steal login details and allow the hackers to deface websites and publish pro-Assad messages on Twitter.
However, it's possible that you are on the look out for phishing emails, and have learnt to be dubious of unsolicited messages or websites that ask unexpectedly for your login credentials to be re-entered.
But, as the last few days have proven, there's still a problem.
What if your computer *isn't* compromised by malware, and you *aren't* visiting a phishing website, and the website *is* set up properly using SSL to protect your communications, and yet you can *still* have your private information intercepted by hackers because your operating system has a bug in it.
 Right now that's the case with iPhones and iPads (if you haven't installed the iOS 7.0.6 update yet), and users running Mac OS X Mavericks (which doesn't yet have any official patch from Apple).
Right now that's the case with iPhones and iPads (if you haven't installed the iOS 7.0.6 update yet), and users running Mac OS X Mavericks (which doesn't yet have any official patch from Apple).
A critical security flaw in iOS and Mac OS X allows hackers to intercept what should have been secure communications between your Apple computing devices and the outside world.
When serious bugs like this existing in the operating system, it makes life too easy for online criminals to act as the man-in-the-middle, stealing what should have been secret information in transit.
While the world is waiting for an OS X fix from Apple (and updating its iPhones and iPads) what lessons can we learn from all of these problems?
Well, one message you should be hearing loud and clear by now is that passwords come with problems. Passwords can be stolen - by phishing, by malware, by hacking, via vulnerabilities.
For those online accounts which you really want to keep secured, a stronger form of protection is required.
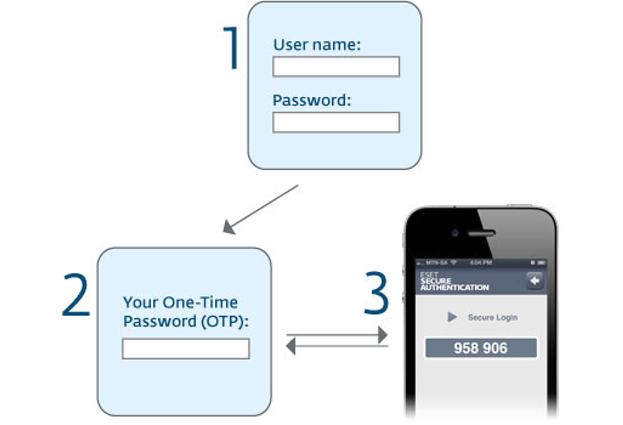
One obvious solution is two-factor authentication (2FA), which generates a unique one-time-password every umpteen seconds.
Everytime you login, a new one-time-password is required.
Even if your regular password is guessed, cracked or stolen by hackers, it won't be any use to the bad guys because they won't know what your one-time-password is.
Indeed, if you use something like a mobile phone app to automatically generate your one-time-password then it's always likely to be within easy reach, but a long way away from the clutches of the hackers.
When a website or service offers you the option of two-factor authentication please consider enabling the feature.
And, if you run an online service or provide systems so your staff can access company information remotely, why not consider offering two-factor authentication to reduce the risks?
Sites like Facebook, Google, Twitter, Dropbox and others do provide two-factor authentication to better secure accounts, but far too many still offer nothing for those who want a higher level of protection.
2FA may not be the magic bullet which kills all online criminal activity dead in its tracks, but it certainly makes life an awful lot harder for the hackers who want to break into your accounts.