This is the first of two blog posts on the malware family Win32/Boaxxe.BE whose end goal is to drive traffic to advertisement websites by using various click fraud techniques, and thus earn money from these websites as an “advertiser”. In the first of these two blog posts we will describe the ecosystem surrounding this operation, whereas in the second we will dig into the technical aspects.
In this blog post we will first describe the affiliate network distributing Win32/Boaxxe.BE binaries and then we will explain how it fits into a larger click fraud ecosystem. We will conclude with some prevalence statistics. (Note: This blog post’s title is based on a David Ogilvy quote.)
Binary Distribution
Our story starts in September 2013, when a website named partnerka.me opened. Simply put, this website’s business is to pay people – called affiliates – to infect users withWin32/Boaxxe.BE. When an affiliate registers himself, he gets access to the following panel (translations are between parentheses):
The “News” section provides the latest information on the state of the business. In the example shown here, the administrator advises the use of WebMoney as payment method.
The “Promo” page provides the affiliate with the program he has to distribute:
The binary is available either by direct download or through a download URL, currently in the form “web5.asia/promos/download?token=TOKEN&sub_id=SUB-ID”. TOKEN is a 20-byte long value identifying the affiliate. A SUB-ID value can also be set, so that the affiliate can distinguish between different groups of binaries in his statistics.
Below these download buttons is shown the binary’s detection ratio for thirty-four anti-malware programs. During our monitoring a new binary was usually provided every hour, in order to stay a step ahead of detection. As usual in this kind of race, new binaries are just a repackaging of the same payload.
Without digging into the technical details yet, it is worth mentioning that each binary contains an affiliate ID, allowing the C&C to credit the correct affiliate’s account whenever a new machine becomes infected. This affiliate ID is a 2-byte long value encoding a counter, which is simply incremented for each newly-registered person. According to the binaries we analyzed, after four months of activity around forty new affiliates were registered.
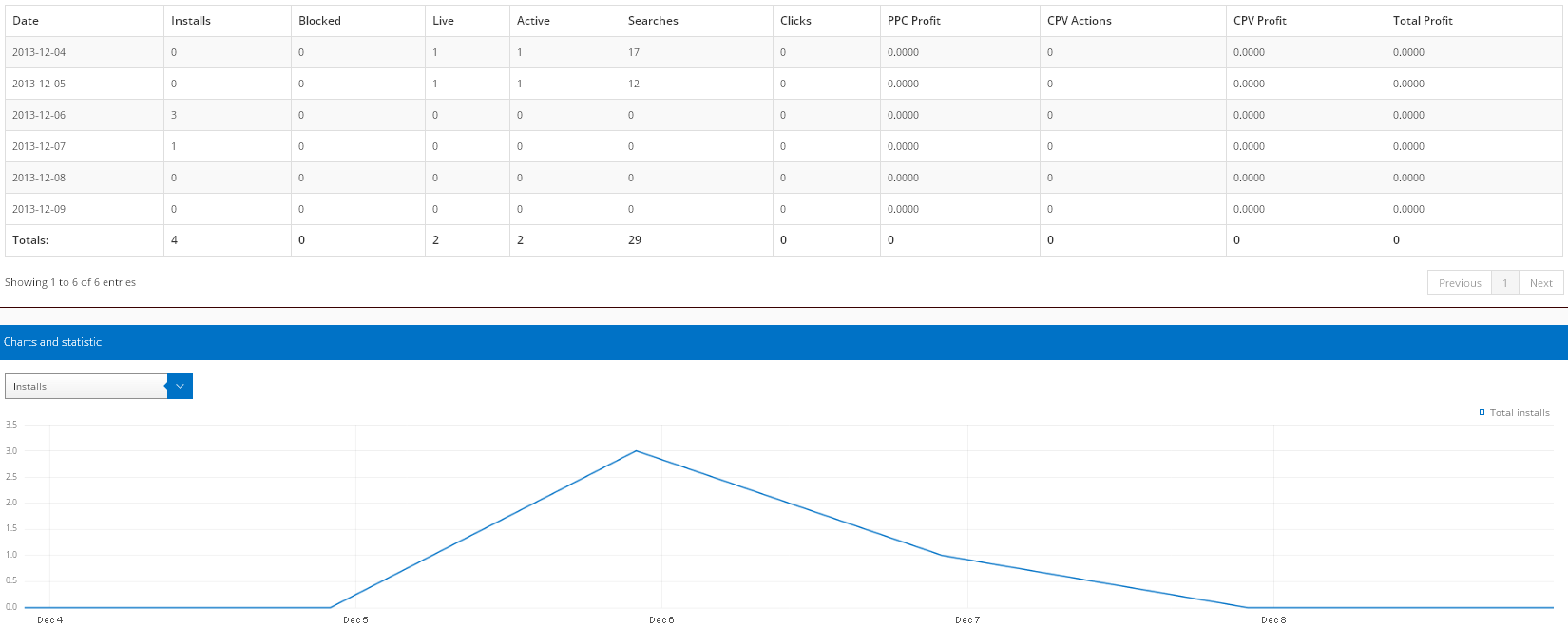
Then comes the “Statistics” page:
The Installs column simply counts number of installations, whereas the meaning of the Blocked column remains unclear; we have never observed a blocked machine in the wild. To understand the other columns it is important to state right now that Win32/Boaxxe.BE implements two different types of click fraud:
-
User-initiated click fraud: users entering keywords in search engines can be rerouted to related advertisement websites. This type of click fraud has already been seen in various malware families, like Win32/TrojanDownloader.Tracur or Win32/Goblin (a.k.a. Win32/Xpaj). Statistics related to this fraud are reported in the following columns:
-
Active: number of machines infected with Win32/Boaxxe.BE that browsed the Internet this day
-
Searches: number of keywords searched for by the infected users
-
Clicks: number of actual re-routings performed
-
PPC Profit: money earned by the affiliate through user-initiated click fraud
-
-
Automated click fraud:Win32/Boaxxe.BE has the ability to browse advertisement websites silently, without the user’s knowledge. Statistics related to this fraud are reported in the following columns:
-
Live: number of infected machines performing automated click fraud
-
CPV Actions: number of automated browsing actions performed
-
CPV Profit: money earned by the affiliate through automated click fraud
-
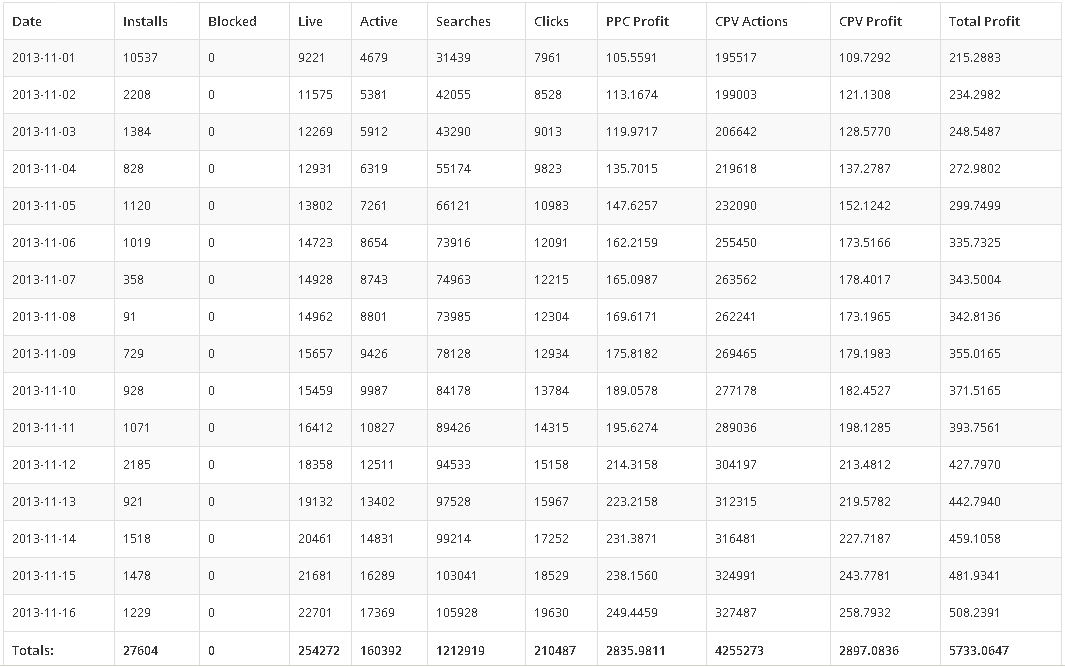
The website also provides an URL to a JSON object containing the statistics, in order for the affiliate to be able to process them himself. Interestingly, no authentication check is made when fetching this JSON object, which means one simply needs to know the 20-byte long token value of an affiliate to access its statistics. For example, we fetched the statistics for one affiliate who entered the network on 7th December, and since then achieved 3,332 installations for a total PPC Profit of around $50.00 and a CPV Profit of around $200.00. On a related note, an advertisement was displayed on some underground websites for this operation, supposedly showing statistics from an affiliate:
Unsurprisingly CPV Actions outnumbers Clicks, as automated click fraud does not necessitate user interaction and can be run continuously on infected computers. On the other hand the ratio CPV Actions / CPV Profit peaks at around $0.0005, whereas the ratio Clicks / PPC Profit is around $0.015, meaning the redirection of a real user is a much more lucrative operation than automated browsing.
Finally, the website contains a payment page and also a support service page to create a “ticket” for the website's operator.
Click Fraud Ecosystem
The image below summarizes the relationships between the different groups evolving in Win32/Boaxxe.BE’s ecosystem.
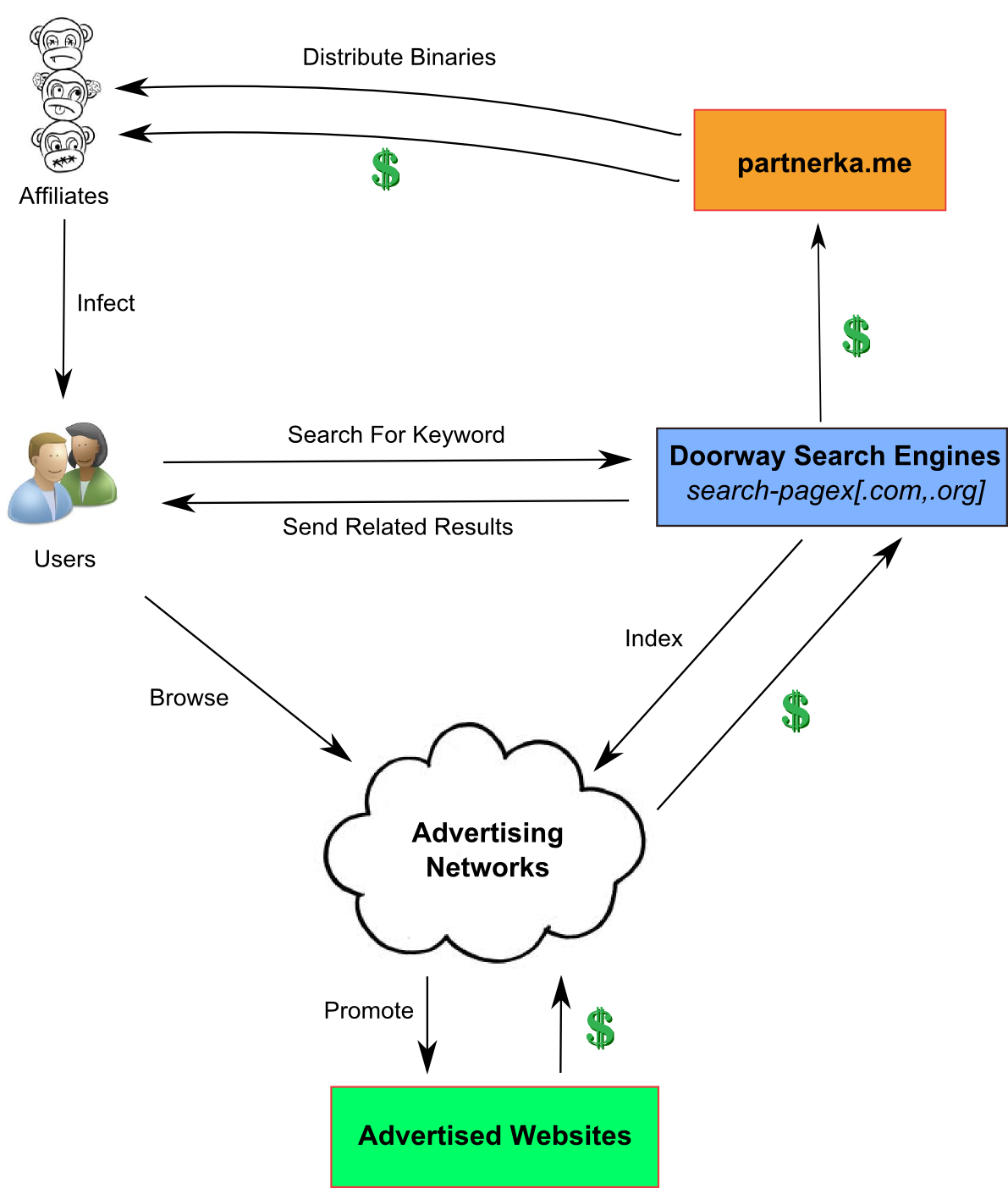
Figure 1 - Win32/Boaxxe.BE Ecosystem
As we just explained, binaries are distributed by partnerka.me to its affiliates, who are then in charge of infecting users. Once infected, these users will be forced to browse various advertisement websites, either automatically or during their search engines' browsing.
In order to do so, infected machines contact some doorway search engines that return for each keyword a list of related advertisement websites. The provided URLs usually start a chain of redirection through websites interconnected in an advertiser-publisher relationship (each website pay the previous one for the traffic it brings). We denote this websites chain an advertisement network.
At the end, advertised websites – which can be legitimate – pay back the advertisement networks for the traffic they brought. These networks take a commission and pay back the doorway search engines. Finally, partnerka.me receives the rest of the money, take its portion and pays its affiliates.
Thus the money trail follows a chain starting from the advertised website to the affiliate in charge of user infection. Another layer of complexity in this ecosystem is suggested by our belief that Win32/Boaxxe.BE binaries are not produced by the owners of partnerka.me themselves. We have indeed observed other Boaxxe versions in the wild, with some strong differences – like different protections or different modules’ implementations – but redirecting to the same advertisement networks.
Prevalence Statistics
The following graph shows the daily detections for Win32/Boaxxe.BE since the opening of partnerka.me in September 2013.
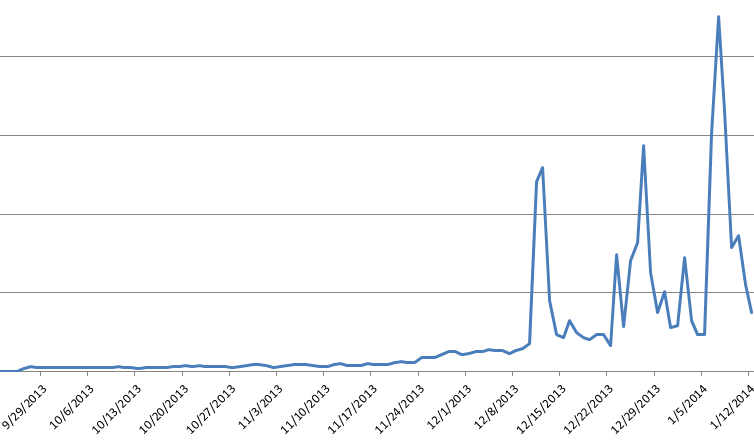
Figure 2 - Win32/Boaxxe.BE Daily Detections
We can observe the rise in importance of this malware family, which corresponds to the increased number of affiliates. The peaks occurring for the last two months correspond to the heavy activity of certain affiliates; for example one of them launched a massive spam campaign at the end of December.
In the next blog post we will present Win32/Boaxxe.BE technical details, with some surprises like the use of a custom DNS cache system. Stay tuned!