A little over a year ago we published our research on the ACAD/Medre worm, a malicious program that not just spread itself through Autodesk AutoCAD files and also send AutoCAD files via email servers located in China to a series of e-mail accounts. From looking at our LiveGrid™ telemetry, it appeared to be a case of industrial espionage because of the high concentration of detections in Peru. The paper was presented as a "last-minute presentation" in Virus Bulletin 2012, in Dallas.
A year after that presentation, security researchers from Autodesk, along with Microsoft, announced new features in AutoCAD to prevent malware in a presentation at Virus Bulletin 2013 in Berlin. In their paper, the researchers identify the main threats facing AutoCAD, including the ACAD/Medre worm. While it may just be a coincidence that Autodesk's presentation on improvements to AutoCAD security comes a year after ESET's ACAD/Medre one, it is still worth looking at this new presentation to see if worms like ACAD/Medre may continue to flourish in the new versions of Autodesk's programs.
The improvements made by Autodesk were distributed in two stages: First, with AutoCAD 2013 Service Pack 1, significant improvements were made, aimed at preventing the execution of malware. Subsequently, the improvements made to security were built into AutoCAD 2014.
So, with that in mind, just what are the improvements Autodesk made to AutoCAD? The most important one is related to the way in which AutoCAD handles its executable files, which use a .FAS or .LSP filename extension, and are used by virtually all malicious code for these platforms. In AutoCAD version 2013 SP1, new system variables have been introduced which can be configured to block the execution of these files, or to select trusted directories for their execution. So, if a business takes advantage of these features, a trusted directory could be defined for executable files that have been developed by the company, while denying everything else, such as files received from third parties and which may well contain malicious code like ACAD/Medre. These variables, AUTOLOADPATH and AUTOLOAD, configure AutoCAD's security to prevent threats from being loaded from untrusted directories. It is also possible to load AutoCAD from the command line using the "/nolisp" parameter, which sets the LISPENABLED variable to zero and runs AutoCAD in a kind of "safe mode" so that if any malicious LISP code is run, it will be unable to perform any actions when AutoCAD starts.
For AutoCAD 2014, some new options have been introduced. First of all, the names of some variables and command line parameters have changed:
-
the AUTOLOADPATH variable is now called TRUSTEDPATHS
-
the AUTOLOAD variable is now called SECURELOAD
-
the /nolisp option is now called /safemode
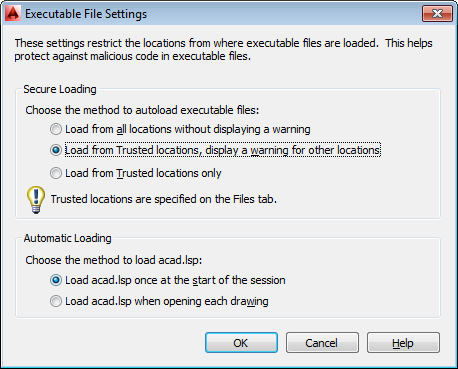
In addition to the features introduced in AutoCAD 2013 Service Pack 1 (with new names), the 2014 edition also includes a new option amidst the existing ones for executable files:
-
Always run executable files.
-
Run the executable files only from the trusted paths.
-
(New) Always run the executable files from trusted paths, but display a warning when run from another location.
In the next picture you can see these options in the AutoCAD 2014 configuration:
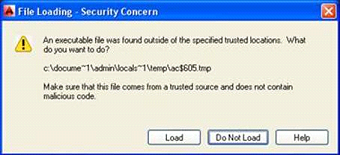
By making use of the new option, AutoCAD 2014 users will be prompted whether or not to run the executable file when an AutoCAD file is opened from an untrusted location:
At the Virus Bulletin talk, after showing these features, Microsoft's presenters showed tests performed with six variants of AutoCAD malware, including ACAD/Medre, which they identify as Blemfox), making use of the different settings offered by new versions of AutoCAD. In AutoCAD 2013, the results of the tests are quite evident:
-
The six variants of malware ran on AutoCAD 2013 with no service pack installed, or when SP1 was installed with default parameters .
-
No malware variant ran on AutoCAD 2013 SP1 when AUTOLOAD and AUTOPATH parameters were used, or the software was run with "/nolisp" parameter.
As seen in the demonstration, AutoCAD's new options are effective in stopping existing malware, but the default settings are not optimal in terms of safety. During the talk, it was explained that safer defaults were not enabled by default because (1) this instance is being used to test the suitability of the features for the 2014 release; (2) AutoCAD malware is not a massive issue (which is actually true); and (3) many users of AutoCAD make use of the functionality. This old security vs. usability dilemma is not unique to AutoDesk; it took several generations of operating system for Microsoft to disable functionality exploited by AUTORUN.INF-spreading worms like Conficker in Windows.
Tests using AutoCAD 2014 were more conclusive, since users are now prompted by default asking if they want to execute additional code or not. Threats are only executed when the user allows them to execute via the prompt and all malware was successfully blocked when the users chose "the right" option. Of course, this has both positive and negative points of view. On one hand, by using non-default configurations or denying execution when prompted, known malicious code for AutoCAD could not be run on this version. On the pessimistic side, will users deny the execution of safe code because a prompt warned them? The experiences with Microsoft's UAC varies in that the security depends on the user making the right click. How safe is this feature? Of course this is a relative concept, and one that is always subject to decisions of the part of the user. Therefore, the importance of raising awareness about potential security issues inside the program is a must.
While writing this post I thought about some of those phrases that are repeated daily and quite clearly describing what happens. There is a phrase alleged to be from Don Quixote by Miguel de Cervantes Saavedra (actually the phrase does not appear in this book in Spanish-speaking countries) that says something along the lines of "…dogs bark, it is a sign that we are riding" [on horses, of course]. The phrase refers that when you are riding a horse, it is good to listen for the dogs, as it is a sign that you are moving forward. At the end of the day, we are glad that published research results in software companies improving the safety of their products. It is important that product security is continueously evaluated and enhanced to mitigate new threats but also to prevent new ones.
"Better than nothing" is another phrase often heard daily? I thought about this while listening to the presentation: If security depends solely on the user choosing the right option, is it good or bad security? Although it sounds right, the phrase is pretty true: It's still better than nothing. In previous versions of AutoCAD, security was dependent on the user and it and was impossible to block these kind of threats in the software where the only defense is to rely on malware detection.
While security purists would prefer that the default settings completely deny the execution of all executable files, the counterarguments to this approach that were presented by Autodesk are quite convincing: the relatively small number of existing malware families and infection reports do not justify such strong security measures that they begin to limit functionalities in the product. Undoubtedly, while making this concession of security to usability, it is still important to be on the lookout for new threats that may arise, continue providing protection against these threats and create awareness among users so that they know the difference that one simple click that can make between being infected or not infecting their system. As Spider-Man's Uncle Ben told him, "With great power there must also come - great responsibility!"
Sebastián Bortnik
Education & Research Manager for ESET Latin America
Sources:
- “A Panoply of Protection: new security and anti-malware measures in AutoCAD”, Virus Bulletin Paper by Eileen Sinnott (Autodesk) and Raymond Roberts & Jakub Kaminsky (Microsoft).
- AutoCAD 2013 SP1 Security Controls: http://usa.autodesk.com/adsk/servlet/ps/dl/item?siteID=123112&id=20327810&linkID=9240617
- Commands for Protecting Against Malicious Code Reference: http://docs.autodesk.com/ACD/2014/ENU/index.html?url=files/GUID-C6DCBFE5-25F6-4387-BD02-B021FA06E3FD.htm,topicNumber=d30e104550
- Executable File Settings Dialog Box: http://docs.autodesk.com/ACD/2014/ENU/files/GUID-8EB6C0AD-8657-490B-8E69-C424FC1568A8.htm
- About Protecting Against Malicious Code: http://docs.autodesk.com/ACD/2014/ENU/index.html?url=files/GUID-9C7E997D-28F8-4605-8583-09606610F26D.htm,topicNumber=d30e104297