In this post, we will examine a fake antivirus program which tries to convince users that their systems are compromised in an attempt to trick them into calling an online PC support helpline. During our research, we uncovered a registered company that seems to have highly-questionable marketing practices.
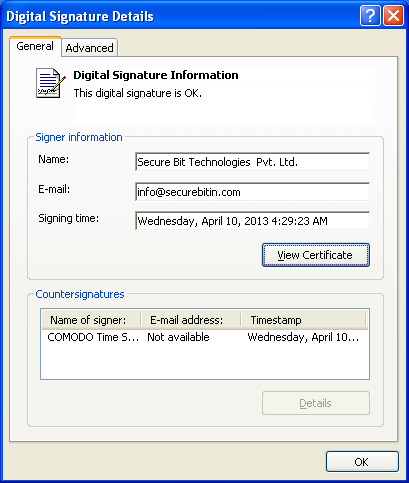
This fake antivirus program, detected by ESET as MSIL/LockScreen.EC, is signed with a valid code-signing certificate*. This certificate belongs to Secure Bit Technologies, a company registered in New Delhi, India.
What makes this sample particularly interesting is that it bundles two types of scams used together in one program: a fake antivirus and a lock screen. Fake antivirus programs typically deceive users into paying money for fake or simulated removal of malware. Lock screen malware “locks” the screen of a computer by preventing the user from seeing any window but the lock screen until a fee is paid. It can be very hard to do anything with the computer once the screen is locked as different mechanisms are used to prevent the user from bypassing the lock screen.
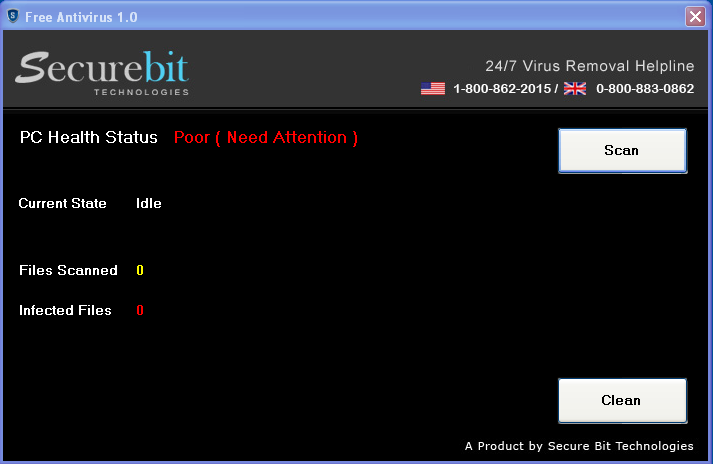
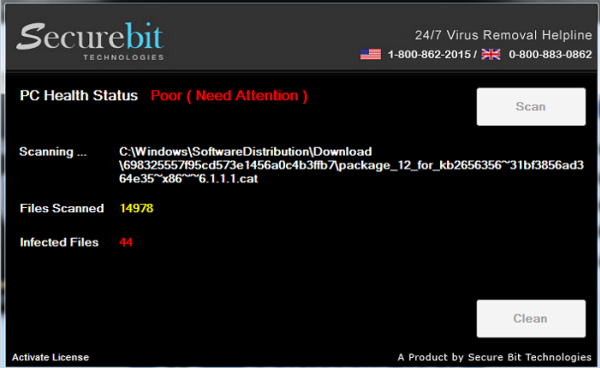
This new hybrid scam program immediately reports a “PC Health Status” as “Poor” when run, regardless of what the real state of the computer is:
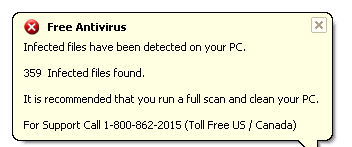
Once the program is installed, it displays a popup balloon on the screen every minute stating that it found malicious files on the system.
In the message, the user is lured into calling a toll-free telephone number to resolve these issues. The phone number is also prominently displayed in the main program window.
The SecureBit scanner continues to find infections as it runs, even on a freshly installed version of Windows 7 that has no malicious code on it.
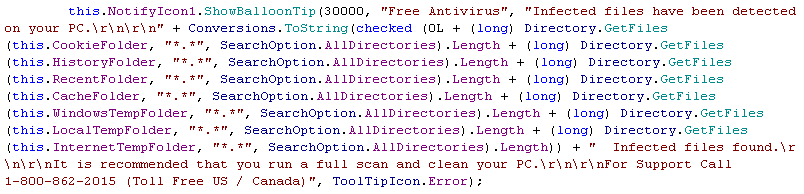
Clearly, the report of “infected” files is falsified and is actually derived from the number of files present in various directories on the infected computer. The screenshot below shows the code used to perform the calculation:
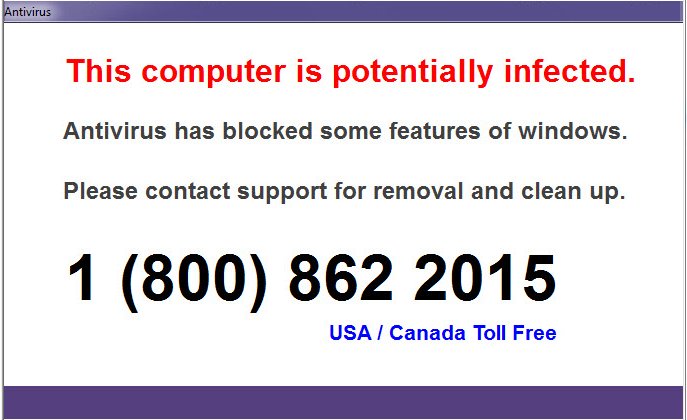
If the user does not register the product’s authors within a specific amount of time, the malware will then lock the screen with a message requiring the user to call the author’s helpline in order to regain access to their own computer.
We have seen an evolution in the lock screen techniques used by the group behind this malware. The first sample we examined had a ten (10) minute interval before locking the screen and would just prevent other windows from being seen. The latest version we analyzed was more aggressive, allowing only two (2) minutes before locking the screen and terminating the explorer.exe process to further prevent access to the Desktop.
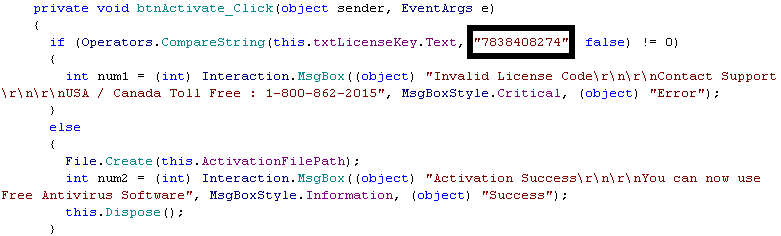
While killing the malware process is quite easy using the Task Manager, it might well trick some people into calling the helpline. The program remains persistent by creating a shortcut in the Startup folder of the Start Menu, so this threat is easily removed by deleting the shortcut. Interestingly enough, the registration key for the product is actually hardcoded in the binary:
Analysis did not reveal any networking capabilities built into this malware. It seems that the sole purpose of this program is to get the infected users to call the helpline. This malware is publicly available from hXXp://freeantivirusglobe.com. This domain was first registered on April 2, 2012.
The behavior of this program is clearly malicious. While trying to determine whether the program was digitally signed with a stolen certificate, additional information was gathered on Secure Bit Technologies. It seems that this company is selling all kinds of services, ranging from web hosting to web design and online support. What is odd is that the helpline number shown in those websites is the same as the one displayed in the fake AV malware. Could it be that this company is actually using malware to try to get people to call their online support?
I placed a call to the toll free number in order to see what kind of support I would get. I was assigned a technician who told me that their product had detected some infected files on my computer. He offered help to clean my system and install some security product for $49.99. This behavior is identical to the support scam business we have seen in the past, except for this new way to reach out to people without cold-calling them, perhaps influenced by recent US legal action against the classic cold-call support scammers.
We also found another binary signed with the same certificate which is advertised as a PC cleaning program. At the time of this writing, the program is still available publicly at CBS Interactive’s (formerly C|Net’s) Download.Com web site (hXXp://download.cnet.com/windows/secure-bit-technologies/3260-20_4-10269493.html). While this program does not appear to be malicious, it displays the same toll free telephone number.
Since Secure Bit Technologies distributes its software through the web, it is understandable that they have chosen to digitally sign their applications. Microsoft’s SmartScreen algorithm ranks signed applications with a higher reputation, so that users will see fewer warnings when downloading them with Internet Explorer. Users will also see fewer warnings when installing and running the software. The fact that Secure Bit Technologies uses their certificate to sign other, non-malicious binaries, helps increase the overall reputation of applications signed by it and thus are more likely to be regarded as trustworthy by Microsoft.
In recent years, we have seen an increase in the amount of digitally-signed malware. Of course, to get a code signing certificate, one must apply for it. In some cases, defunct companies are used in the application. Other times, code signing certificates get stolen. In other cases, firms with shady business practices are able to get their hands on a code signing certificate.
*Comodo was notified that one of their code-signing certificates was being used maliciously and they promptly revoked it.
Hashes
MSIL/Lockscreen.EC:
sha1 hash: 01fb427fb74fbc4acd10bc51e2cc04bd7af3ee65