[Update: second screenshot was removed temporarily to remove the URL, and is now replaced with a cropped version.]
There are things almost as certain as death and taxes: crime is one of them. And there are certain events that always seem to trigger certain kinds of cybercrime. One is disaster, natural or man-made. So my colleague Urban Schrott has called attention to the likelihood of scams piggybacking the serious impact of ‘Superstorm’ Sandy on the East Coast of the US, and the FTC has some good advice on spotting charity scams. And this type of scam has been addressed in the Threatblog quite a lot before, so I won’t go belabour the point about Sandy-related 419s, phishing attacks, Blackhat SEO, and even out-and-out hoaxes with no apparent cash motive. This graphic, featured in Urban’s blog, is actually a doctored still from the disaster movie The Day After Tomorrow, and the Huffington Post noted last week that the number of sites registered with names potentially associated with the hurricane had already reached 1,100.
 Then there’s the release of new technology. We tend to expect to see all significant new technology become the subject of social engineering attacks, though personally I would not be at all disappointed if that failed to happen for once. But I’m not holding my breath. We’ve already seen scams specific to the new iPad mini (but ‘free iPad’ scams via Facebook apps, email, SMS and so on, are a persistent feature of the threatscape, not surprisingly given the popularity of tablets in general and that particular product specifically). Then there’s Windows 8. While I agree with Aryeh that there are lots of good things in the latest version of Windows, security-wise – I have to, as he’s far more knowledgeable on Windows internals than I am! – the fact is that there is much more to being safe online than the operating system, though having a well-secured and maintained OS is no bad thing.
Then there’s the release of new technology. We tend to expect to see all significant new technology become the subject of social engineering attacks, though personally I would not be at all disappointed if that failed to happen for once. But I’m not holding my breath. We’ve already seen scams specific to the new iPad mini (but ‘free iPad’ scams via Facebook apps, email, SMS and so on, are a persistent feature of the threatscape, not surprisingly given the popularity of tablets in general and that particular product specifically). Then there’s Windows 8. While I agree with Aryeh that there are lots of good things in the latest version of Windows, security-wise – I have to, as he’s far more knowledgeable on Windows internals than I am! – the fact is that there is much more to being safe online than the operating system, though having a well-secured and maintained OS is no bad thing.
Secure as Windows 8 seems to be – though it’s clear that the search for ways in which to compromise it has been underway since long before its public release, and there are already reports of exploits – it has already been used extensively for social engineering attacks of various kinds. Trend Micro has sounded the alarm on fake anti-virus passing itself off as a Win8-specific security program, and both Trend and Sophos have flagged email messages offering a ‘free upgrade’ to Windows 8.
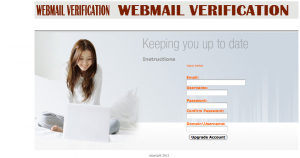 However, the link in one such email takes you to a form that looks a lot like this. I got this screen capture yesterday, several days after the articles by our friends at Sophos and Trend Micro so it would seem the phishing scam, unlike the storm, has not yet passed. If you complete the form, your information is redirected to an unknown address. And you may notice that the form doesn’t mention Windows 8: it’s so generic that it could be used for almost any scam, with a little bit of careful social engineering in the initial phishing message. (The phish message flagged by Trend and Sophos is actually pretty unconvincing.)
However, the link in one such email takes you to a form that looks a lot like this. I got this screen capture yesterday, several days after the articles by our friends at Sophos and Trend Micro so it would seem the phishing scam, unlike the storm, has not yet passed. If you complete the form, your information is redirected to an unknown address. And you may notice that the form doesn’t mention Windows 8: it’s so generic that it could be used for almost any scam, with a little bit of careful social engineering in the initial phishing message. (The phish message flagged by Trend and Sophos is actually pretty unconvincing.)
But here’s a slightly different angle of attack. Vicki, who quite often comments on our blogs, told me today that “...a friend of mine recently received a call from a female who sounded foreign ... who claimed Microsoft was having them call everyone about a nasty virus all people with Windows 7 were experiencing...”
As it happens, I’ve heard about (and received) calls rather like that before. We’ve already mentioned here that support scammers from India used a spike in detections of Quervar/Dorifel in the Netherlands to offer ‘help’ to people in that region with disinfection, and I’ve received calls here in the UK from scammers who claimed that they could help me with a virus that was epidemic in this region, though they were unable to tell me which virus.
Can we expect scam calls like the one Vicki’s friend received, offering help with a Windows 8 virus or perhaps with other Windows 8 problems? I don’t know, but it’s certainly far from impossible. As more people get to hear about the older forms of the scam, the scammers are likely to seek new variations, and it’s a short step from 7 to 8...
David Harley CITP FBCS CISSP
ESET Senior Research Fellow




