Virus Bulletin's Martijn Grooten has drawn my attention to a couple of interesting and highly relevant articles on the ongoing PC support scam issue, where someone calls you to tell you that you have a virus (or some other system issue) and offers to provide technical support (for a fee…) Martijn and I, along with Steve Burn and Craig Johnston, have been doing a lot of writing on this recently.
Firstly, Brian Krebs returns to the theme with his article Tech Support Phone Scams Surge: he summarizes a number of scam attempts that have been reported to him.
In one instance, an 11-year-old was persuaded to enter some numbers into the Run window. My guess is that the number in question is was probably a unique code to enable the scammer to get remote access through ammyy.com or something similar.
According to Krebs, his reader assumed the machine was compromised and would need to be reformatted. That is, I guess, a rational assumption, though in general the reports I've received suggest that scammers usually upload legitimate (but free and irrelevant) software rather than malware. On the other hand, as I reported in a recent blog, I have a reliable report of a scammer trying to install an (unknown) web link as a startup shortcut. Since it would be unusual for an 11-year-old to have a credit card or a PayPal account, it's possible that the scammer intended to leave some kind of backdoor access in the hope of establishing a more profitable contact later. However, it also occurs to me that a scammer might also try to leave some kind of access available on the victim's machine so that they can come back for another helping. However, I don't have information (apart from my conversations with Chris Hamer) as to whether such a compromise may have taken place, or as to how it might be implemented.
Krebs also includes reports suggesting that old people are being targeted. I'm not sure to what extent this is a deliberate strategy, since it's not clear how much information the scammers really have about their intended victims: quite a few of the many scammers who've called me are clearly using an outdated directory. However, it's clear that many types of scam are perpetrated by people who regard older people as easy prey, and I've blogged elsewhere an experience of my own with a scammer who assumed that I was even older than I am, and that my presumed advanced age meant that I was both lacking in technical knowledge and easy to intimidate.
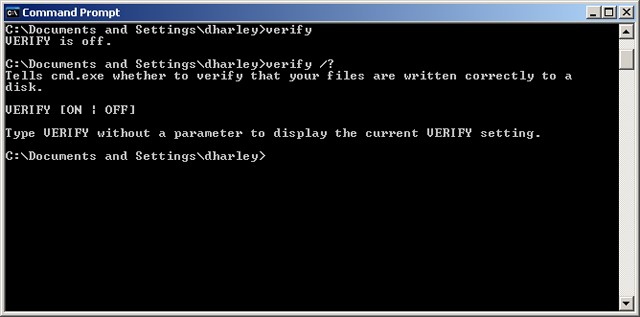
Kaspersky's David Jacoby has also recently put up an article relating his own experiences. While there's not much there that will be new to people who've been following this thread on ESET's ThreatBlog, it's a good, comprehensive article that addresses two issues of particular interest to me. Firstly, he confirms that the Task Manager ploy I reported here a while ago was by no means a one-off. (That's where they tell you that your CPU usage should be at 80-90%, and the fact that it's only registering at 3% means that all your CPU cycles are taken up by the malware. It's total rubbish, of course.) Secondly, he reports a new gambit (new to me at any rate) involving the misuse of a system utility (in this case, VERIFY). I thought it was worth expanding a little on that trick here.
As you can see from the minimal helpscreen shown in the screenshot, VERIFY is used (not very often, I suspect) as a check that files are being written to disk correctly. Unlike INF and PREFETCH, which will let you type any old rubbish - such as INF number of virus infections' - and simply ignore everything but their own names (see my article Support Scammers (mis)using INF and PREFETCH for more information on how those utilities are misused), VERIFY will put up an incorrect parameters message if you try to type in something like VERIFY Microsoft Licence . However, if you type it in with no parameter, it will simply tell you that VERIFY is off.' This just means that file-write verification is turned off (the default setting). According to Jacoby, however, the scammers tell their victims, however, that it means that your Windows licence (or something of the sort) isn't verified, so that security patches can't be applied. But of course, this and all your other problems can be fixed for a not-so-small fee.
VERIFY exists, as far as I know, in all current versions of MS-DOS and Windows. It may be worth knowing, though, that running just about any DOS command with the /? parameter will put up a helpscreen like this to tell you what the utility really does and how it works. It won't work with the INF or PREFETCH utilities, though, which are not recognized at the command-line, but does work with ASSOC, which is often misrepresented as indicating a licensing problem. While EVENTVWR (Event Viewer) is recognized at the command line, the /? parameter is disregarded: it just runs the utility, which is also misused by claiming that it shows malware or critical system errors.
I don't advise that you waste time on this kind of call: the circumstances under which Microsoft might contact you about a malware issue are very limited indeed. And I certainly don't advise that you let anyone connect remotely to your system unless you know exactly who they are and why they're doing it.
Still, it might be useful to you to know which utilities are currently being misused by scammers, and how to use the command line or the Help and Support option on the Start button to check out what a utility really does, if only so that you can advise other people.
David Harley CITP FBCS CISSP
ESET Senior Research Fellow