Last week an epic security event took place in Russia – the PHDays’2012 conference. This event started last year as the first conference in Russia for security researchers focusing on deeply technical speakers – all the videos translated into English are already online here. This year, ESET Canada's Pierre-Marc Bureau presented a workshop on “Win32/Georbot. Understanding a malware and automating its analysis”, about reverse engineering the Georbot trojan. And I and my colleague Eugene Rodionov presented the results of our research into “Smartcard vulnerabilities in modern banking malware”.
Our presentation starts with a consideration of the evolution of the Carberp family of banking malware (we already discussed this in our CARO presentation in May).
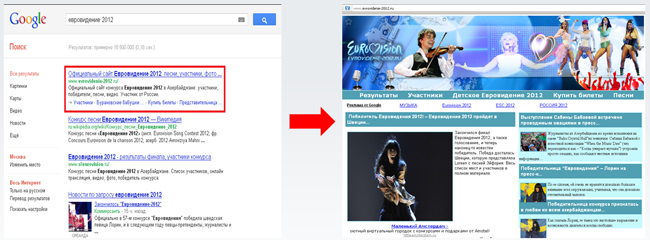
On the day before the conference I tracked blackhat SEO poisoning on the Russian Google search results page for requests relating to Eurovision 2012 in the Russian language.
The first Google search item returned is a redirect to a malicious webpage passing itself off as a legitimate site about Eurovision 2012. If a malicious JavaScript detected real user activity, the next step would be a redirection to a Nuclear Pack exploitation service.
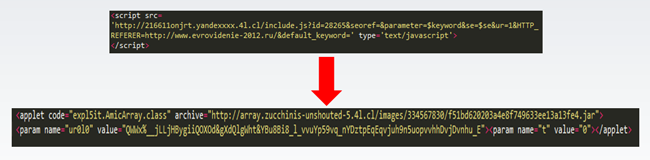
Nuclear Pack uses some interesting techniques for generating unique file names with exploitation vectors to bypass crawlers - if you can’t step all the way through the malicious redirection you can’t track all the logic that governs name generation). All java exploits here used layered obfuscation, and used applet parameters to implement the deobfuscation flow.
The second part of our talk was about attack techniques against client-bank systems. The most interesting part of presentation was about vectors for attacks on smartcards. In 2010 we already published a blogpost – “Dr. Zeus: the Bot in the Hat” – about the manipulation of APDU commands and hidden remote channels for controlling a smartcard device. This bot is still in the wild and ESET detects this family as Win32/Spy.Ranbyus (MD5: F2744552D24F7EA31E64228EB3022830). We have found functionality for covert smartcard manipulation in the code of the latest modifications too. The current C&C (Command & Control) has changed domain, to wh1tesun.info (80.79.117.171).
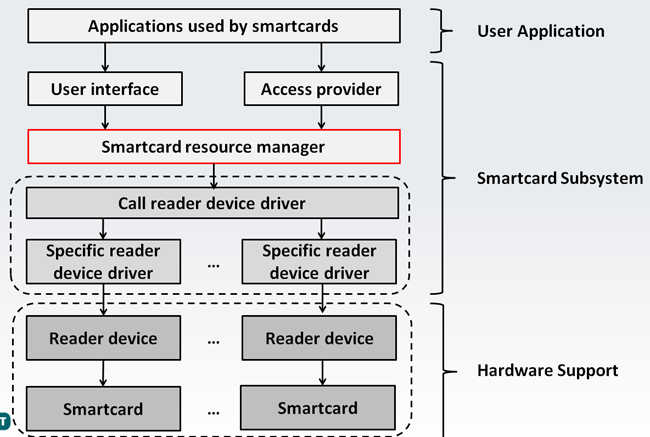
If Win32/Spy.Ranbyus finds an active smartcard or smartcard reader device on the infected machine, the bot sends this information to the C&C with a description of the type of smartcard it finds. All malicious smartcard manipulation works at the SmartCard API level.
The user authenticates to the smartcard device, and the bot sends a signal to the C&C. After that, the smartcard can be used remotely through the C&C by means of APDU command manipulation, allowing all typical smartcard workflow using the victim's credentials.
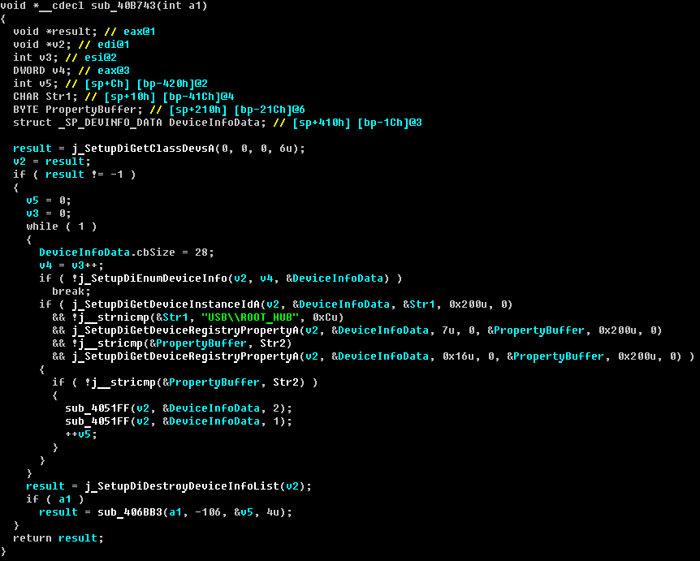
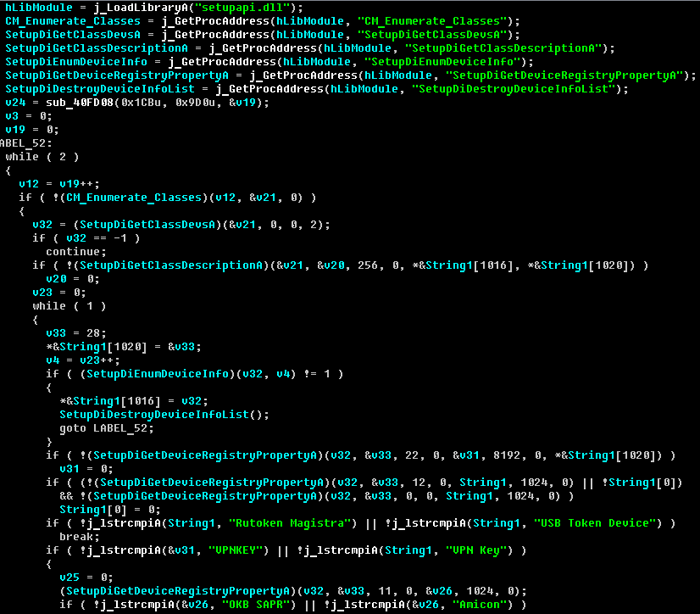
The next interesting case involving smartcards was detected at the beginning of this year. Hodprot, the latest Carberp cybercrime group, switched to using RDPdoor v4.2.x (MD5: 0E9CCECABA272942F1A4297E42D3BA43). This modification collects information about an infected system and devices in use by means of SetupApi.
Its activity is focused on smartcard devices used in Russian remote banking systems:
If a smartcard device is detected, the bot prepares a special description to send to the C&C:
[VendorId]:[ProductId]:[Revision]:[InfoRetrievedFromDevice]:[DeviceNameOrDescription]
Examples of the filled-in structure look like this:
0A89:0060:0102:06512119781D0E:Rutoken Magistra;
096E:0005:0290:065C62807A1C0E:USB Token Device;
0A89:0060:0102:06336059708D9E:Rutoken Magistra;
0CA6:00A0:0010:06024350706F87:USB Smart Card reader;
23A0:0002:0100:20BEA090712EC1:BIFIT ICCD Smart Card Reader;
2022:0008:1001::USB Smart Card reader;
A420:542A:0100::VPN Key;
0A89:0020:0200::Rutoken S;
RDPdoor collects a great deal of information about the infected system to facilitate the following analysis by the botmaster.
After analysis, the botmaster can send additional commands back to the bot for installing additional modules onto the infected system. If a smartcard device is detected, RDPdoor can install FabulaTech USB for Remote Desktop to implement remote control of smartcards on the infected machine.
The use of smart cards reduces the security risks of online transactions, but we see here some attacks that bypass smartcard security at the operating system API level in order to steal money.
Aleksandr Matrosov, Security Intelligence Team Lead