DNSChanger, a piece of malware that re-routed vast swathes of Internet traffic through rogue DNS servers after users became infected, was shut down by the FBI late last year. But simply shutting down the servers altogether would have ‘broken’ many hundreds of thousands of computers still infected--rendering it difficult for them to get help via the Internet--so the FBI and ISC orchestrated a temporary fix, which is set to end on July 9th. This temporary fix has allowed infected computers to stay connected, but that’s coming to a close.
Now Google has rolled out a program to notify people when it detects that their computer is trying to reach those temporary DNS servers. If you use Google Search that will trigger the detection process and a message will appear saying that “you might be infected” if Google detects those temporary DNS servers. This mesage could be confusing because you might have thought you had disinfected your machine. So is it possible to have your computer only ‘halfway fixed?’
If, for example, you used a tool to remove the malware, would it necessarily restore the DNS settings you had before the infection, or would it just eliminate the infection and still leave your traffic re-directing to the soon-to-be-closed temporary DNS servers? If you want to check, you can open up your network interface settings (wired and/or wireless) and look at your DNS settings. While your Operating System may be different, on Windows 7 you can check it by viewing the Properties tab for your interface like this:
Then selecting IPv4 Properties from the next dialog box like:
Here you’ll see a tab for DNS settings like this:
If your system is set to "Obtain DNS server address automatically, this usually this means you’re okay, and that your DNS is getting its settings from your router/switch/access point. If your system is set to "Use the followng DNS server addresses" and you see entries for "Preferred DNS server" and "Alternate DNS server" make a note of those addresses and check them against the list below:
- 77.67.83.1 - 77.67.83.254
- 85.255.112.1 - 85.255.127.254
- 67.210.0.1 - 67.210.15.254
- 93.188.160.1 - 93.188.167.254
- 213.109.64.1 - 213.109.79.254
- 64.28.176.1 - 64.28.191.254
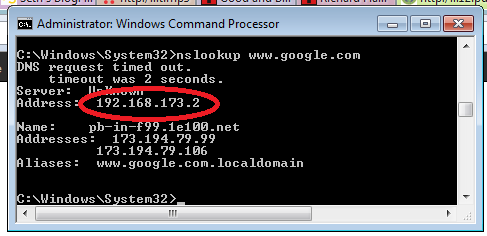
If your addresses are not in that list you should be fine. Another way to check is using nslookup, by opening up a command prompt (Windows 7: Start button -> Search programs and files -> type “cmd” and hit Enter) and then using nslookup like:
Notice my DNS server is 192.168.x.x – a non-publicly-routable address. Yours might vary a bit here, but 192.168.x.x addresses are very common on internal networks, as are 172.x.x.x and 10.x.x.x networks, so those are normal. Also you can see the last line showing the IP it thinks belongs to Google’s website. You can verify this by typing 173.194.79.106 (or whatever yours says, it will probably be different) directly into your browser and seeing if you see www.google.com, you should.
If, on the other hand, when you use nslookup you see any of the ranges of IP’s in the list above, that means you've got problems and need to fix your computer/router. If your router has been compromised, the effects can be more far-reaching because all the computers--including mobile devices which are Wi-Fi enabled--that are on your network will point to servers which soon won't work, because your local DNS is directing them to places it shouldn't. Don't worry, there's still time to fix it. You will need to follow the instructions for setting DNS in your router or Wi-Fi access point. If you don't have easy access to those instructions and cannot find them on the device maker's website, try this page at OpenDNS, a site that offers a wealth of free information on DNS settings (you may need to register to get to some of the information, but registration is free and in our experience they don't spam you).
This may be a pain to fix but don't wait, you need to get it fixed before the July 9th cutoff or devices on your network won't be able to reach vast swaths of the Internet, making it difficult to get help online.