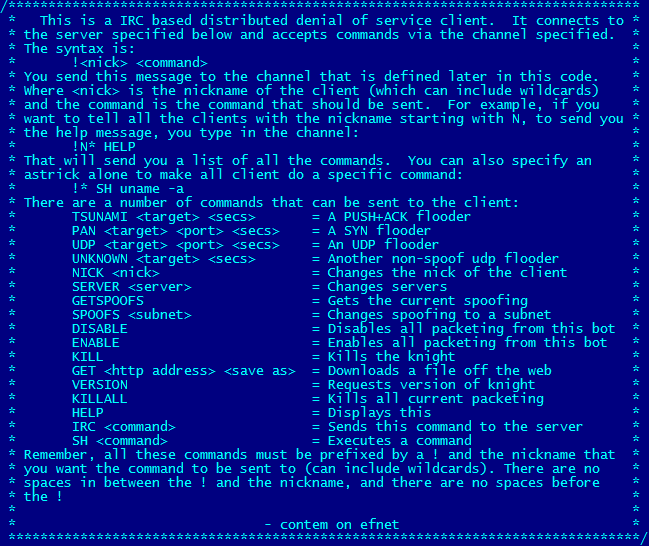
We’ve just come across an IRC controlled backdoor that enables the infected machine to become a bot for Distributed Denial of Service attacks. The interesting part about it is that it’s a Mach-O binary – targeting Mac OS X. ESET’s research team compared this to samples in our malware collection and discovered that this code is derived from something we’ve seen before. It is actually an OS X port of the Linux family of backdoors that we have been detecting since 2002 as Linux/Tsunami.
The analyzed sample contains a hardcoded list of IRC servers and channel that it attempts to connect to. This client then listens and interprets commands from the channel. The list of accepted commands can be seen in the following comment block from the C source code of the Linux variant.
In addition to enabling DDoS attacks, the backdoor can enable a remote user to download files, such as additional malware or updates to the Tsunami code. The malware can also execute shell commands, giving it the ability to essentially take control of the affected machine.
In terms of functionality, the Mac variant of the backdoor is similar to its older Linux brother, with only the IRC server, channel and password changed and the greatest difference being that it’s a 64-bit Mach-O binary instead of an ELF binary.
ESET security software (including ESET Cybersecurity for Mac) detects the malware as OSX/Tsunami.A.
Robert Lipovsky
Malware Researcher