The authors of Win32/Qbot (a.k.a. Qakbot) are back with new variants of this infamous malware, and this time the binaries are digitally signed.
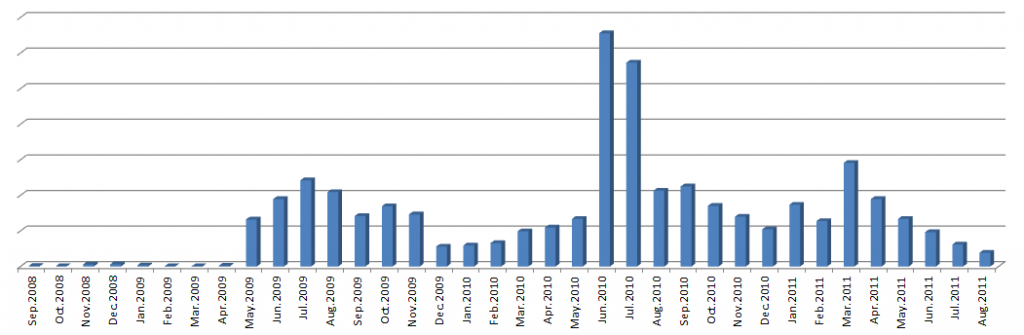
Qbot is a multifunctional trojan that has had some significant impact in the past. It has also been around a while, with the first variants dating as far back as spring 2007, with more massive distribution starting two years later in 2009. The following figure shows the relative detection ratio of all Qbot variants over time.
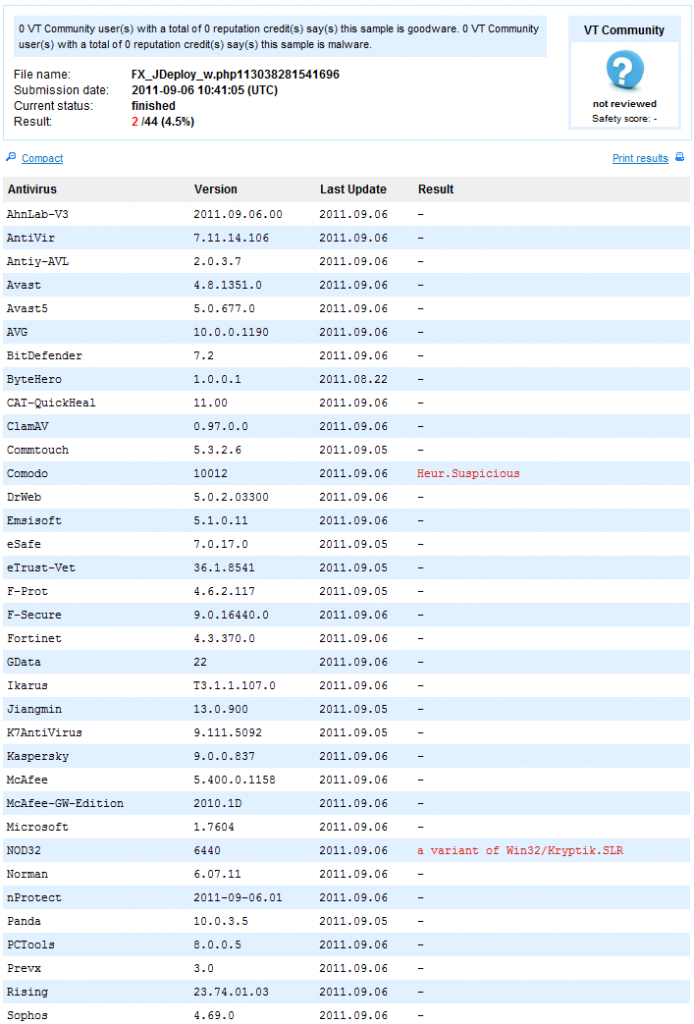
There have been some new variants in late spring this year and since then the developers of Qbot have been quiet…until now. It seems that they have come back from their summer vacations and pushed out a new release. Two weeks ago we caught the latest version with our advanced heuristics. What’s interesting is that the authors first tried releasing the trojan without packing it. That probably wasn’t very successful, so they added a layer of protection provided by a packer. Our sample collection system even shows that the Qbot authors have experimented a little with different packer combinations. The latest packed version was detected by ESET (again heuristically) under the name Win32/Kryptik.SLR two days ago. While the resemblance of the detection name to the McLaren supercar is purely coincidence, the authors of Qbot have had much better success this time, as the following VirusTotal screenshot shows.
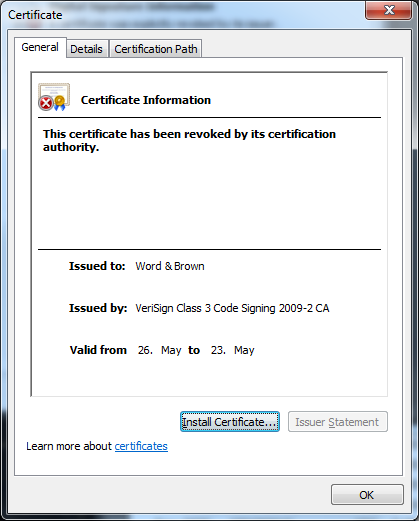
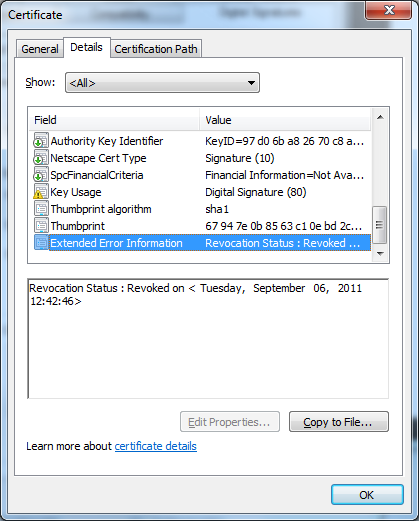
Another interesting finding is that this packed variant is digitally signed. The Qbot authors are using a certificate probably stolen from a company called Word & Brown. Fortunately, at the time of this writing the certificate has been revoked by VeriSign.
A quick analysis shows that the code of this Qbot version has been rewritten, but the functionality remains very similar to the previous versions. As a reminder, Qbot’s main purpose is stealing different types of sensitive information, including:
- Various user names and passwords
- Keystrokes
- Cookies
- Digital certificates
- Visited URLs
- And much more…
It features a backdoor, which enables the bot to be controlled remotely, update itself, download and run other executables on the infected system. It can also insert malicious IFRAME tags into webpages, has the possibility to block access to domains containing certain keywords (which it uses as an anti-AV feature), and can be used for man-in-the-middle attacks against victims’ online banking systems. Win32/Qbot uses rootkit techniques to hide its presence in the operating system and also has characteristics of a worm, as it can spread through network shares and removable drives.
The functionality of Qbot is quite extensive and also expandable. More detailed technical write-ups of previous versions can be found here: Win32/Qbot.AN and here: Win32/Qbot.AU.
We will continue monitoring this threat and provide more interesting information when it comes up. Meanwhile, our detection team is working on providing the most effective protection for our customers. The latest variant of Qbot is generically detected by ESET security software as Win32/Qbot.AY.
Robert Lipovsky
Malware Researcher