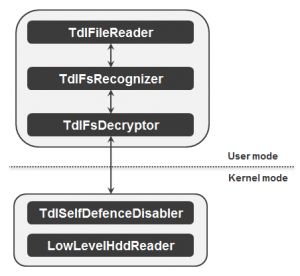
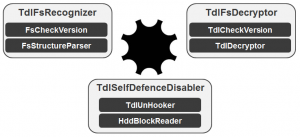
If you've been following the research we've been publishing (spearheaded by my Russian colleagues Aleksandr Matrosov and Eugene Rodionov) you'll be aware that the TDL rootkit family doesn’t make use of OS’s own file system. Instead, it implements its own hidden storage for the payload, configuration files and so on. The hidden storage is located at the end of the hard drive and encrypted either with RC4 cipher or by XOR-ing with a hex constant.
Recently, Aleks and Eugene released a new version of the tool they developed in the course of their research into the TDL family, which gives easy access to these hidden files. It handles TDL versions including TDL3/TDL3+, TDL4 (x86 and x64 versions), and the drivers and binary are all signed by ESET.
They've also released a video demonstration of how to make use of the tool, and another video on debugging the bootkit component of TDL4 with IDA and Bochs, as demonstrated at the recent CONFidence 2011 conference in Krakow.
How to use it
Run the tool with the following parameters:
tfd.exe [-v] [directory_to_save_files]
-v for verbose output;
directory_to_save_files - specify directory where content of the file system will be stored.
This tool requires administrative privileges (in order to load the driver).
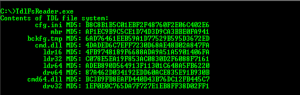
Output example: TdlFsReader.exe
And just as a reminder, there's more info on TDL3/4 on the white papers page:
The Evolution of TDL: Conquering x64
By Eugene Rodionov and Aleksandr Matrosov
Defeating x64: The Evolution of the TDL Rootkit
By Aleksandr Matrosov and Eugene Rodionov
TDSS part 1: The x64 Dollar Question
By Aleksandr Matrosov, Eugene Rodionov & David Harley
TDSS part 2: Ifs and Bots
By Aleksandr Matrosov, Eugene Rodionov & David Harley
TDSS part 3: Bootkit on the other foot
By Aleksandr Matrosov, Eugene Rodionov & David Harley
Rooting about in TDSS
By Aleksandr Matrosov & Eugene Rodionov
Article first published in Virus Bulletin, October 2010. Copyright is held by Virus Bulletin Ltd, but is made available on ESET's white papers page for personal use free of charge, by permission of Virus Bulletin.
David Harley CITP FBCS CISSP
ESET Senior Research Fellow