Greetings Dear Reader,
We have published guidance material previously on passwords and passphrases, some are blogs and some are lengthier depending on your liking (link & link). Even still it is always good practice to reinforce sensible password techniques. For this blog, I plan on sharing an analogous self-ritual, and one that relies on a third party application and share examples. Such an application falls under the “password manager” category of software. Many exist across the various platforms, and I highlight a few here well known that come to mind from a larger list (alternate):
There are other options for password managers such as IronKey's which is a secure thumb drive. Please note, I am not looking into the quality of these password managers or how safe they are, nor am I endorsing them. That is perhaps a topic for another time. Let us now turn our focus to the my analogous password/passphrase methodology.
Using one of these managers, these are the things which I pay attention to:
- Strong Master Password
- Create a strong password for the 'master', the one that opens up the password manager. This is probably one of the strongest if not *the* strongest since my passwords are stored in it.
- Randomize Passwords
- Use the manager to create random passwords set at the upper limit for the location you are creating it for. So, if a site says the maximum length for a password is 20 characters, then I set it to 20.
- Also consider what account your password is protecting. Gaming? Online Banking? The beauty of a password manager is, one may create strong maximum length passwords for all accounts, and simply use the manager to reclaim your password when logging in.
- 1:1
- Create one password for one account. Dot not resuse elsewhere.
- Usernames
- Consider randomizing your username depending on what you are protection. For instance, online banking. And follow the same maximum length suggestion noted earlier.
- SQ/SA
- When creating a secret question secret answer pair, apply the same technique as above. Create a random secret answer making it harder for would-be attackers to break.
This may seem like a lot to "remember"; however, if employed through a trusted password manager one can simply enter the Master Password and access one's list of accounts easily. A few security gurus I know and trust use these types of rituals, and have for years with success.
However, the buck does not end with this ritual. One must be careful to run quality security software to catch keyloggers and malicious applications that steal data and take desktop screenshots. Being infected may usurp these password practices. So again and again, be careful!
Now on to some graphics. Using KeePass 1.0 as an example and pulling from their available screen shots:
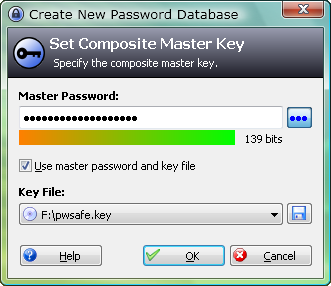
The following is an example of how KeePass implements the "Strong Master Password" item. It has a feature that shows how "strong" your master password is (be sure to have secure backups of your Key File just in case your master is lost or crashes).
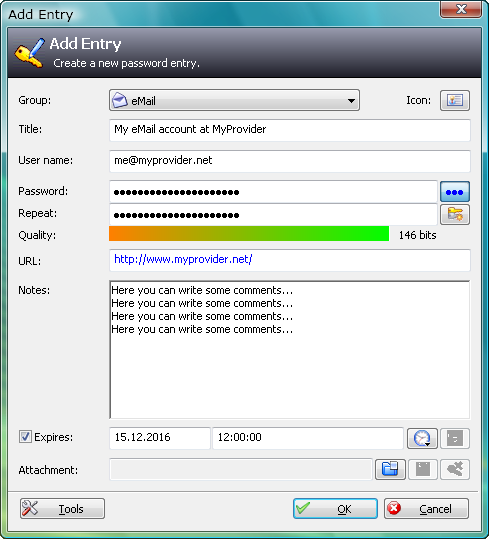
Here is an example of creating a new username and password account pair. It has the same graphic feature to depict how "strong" your password is. Within one may store items such as the Secret Question/Secret Answer pair.
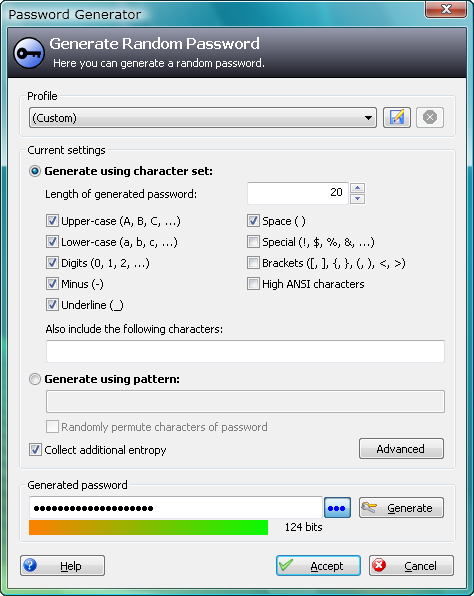
This next screen we observe shows the various options to create a random password. One may set the length of the password, and enable certain character sets for the creation of the password. If a site permits Special Characters for example, the suggestion is to check it and use it for the generation piece. Such a randomized generated password makes it harder for brute force dictionary attacks to guess.
Other password managers cited above or linked to have similar features and functionality. They just may go about securing your information similarly or differently. Again, a potential topic for another time.
In the end, I like this technique because it promotes uniqueness in passwords, randomness, and the ability to store the information securely.
So what does a 20 character limit strong random password look like? Here are some examples I generated just to share (the applications generate these too):
- -=E7%S=#e,x(qx_z2!Qw
- a@s%I4$3z7@K!F3s:K&|
- @HM4/2_#:x+9Q [551W8
- YC57_UIu4_IPt4$({_-9
Reminder, these may also be used uniquely as usernames as well depending on where you'd like to deploy such a strategy. So don't use such as username then as your password, create a unique password. Example:
Username: 48N18RQ1o9XM1Xi84KLs
Password: 8O9N6[yBNSkG%/8r!:[g
I hope that this technique was understandable and easily digestable. It is just one format that may be followed and I am sure others exist that may or may not suit your requirements. If you have advice and are willing to share, feel free to email me or post a comment to the blog. Afterall, we're all here to learn from each other.
For more light reading Securing our eCity has published a list of password pitfalls, a good read to print out and share as well. These practices may be applied to virtually any type of account, some notably Facebook and LinkedIn social networking sites.
Read about Privacy Guides I wrote on Facebook and LinkedIn.
Cheers!
Paul Laudanski, Director of CTAC