UPDATE #1 Randy Abrams has posted a follow-up article, Anatomy of a Biting Bunny – The Infected Microsoft Catalog Update with additional information about how update services work, why they might distribute third-party code and what might be done to prevent malware from being distributed on services like Microsoft's Windows Update in the future. 7-FEB-2011.
Last week, we received a report from a customer who reported that NOD32 had prevented a Trojan from infecting a mobile user's computer. While that is not unusual in and of itself, what was notable was the source of the infection: Microsoft's own Update Catalog.
As you may be aware, Microsoft not only provides updates for its own operating system and applications, but they also provide hundreds of thousands of device drivers as well. A device driver is a specialized piece of software that allows an operating system to use a particular device, like a printer or a mouse. While Microsoft does write some of these device drivers themselves, many of these are very basic and provide rudimentary functionality: It is up to each hardware manufacturer to create device drivers which take full advantage of whatever additional features they have designed. In the case of a video card, this might be support for additional screen resolutions and color depths and 3-D graphics acceleration. In order to ensure that customers have the best experience possible with Windows, Microsoft hosts these device drivers written by third-parties in their Update Catalog, so that when a computer running Windows checks for updates, it can download the latest device driver software for its hardware.
In this case, though, the device our customer plugged into his notebook appears to have been an Energizer® DUO USB Battery Charger, which is an AC and USB charger for rechargeable NiMH batteries. In case that device sounds familiar, perhaps you recall this web page from 2010: US-CERT Vulnerability Note VU#154421: Energizer DUO USB battery charger software allows unauthorized remote system access discussing how the battery charger shipped with management software for Microsoft Windows also installed an unwanted Win32/Arurizer remote access trojan.
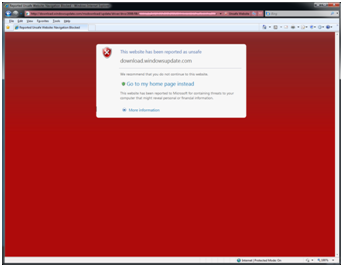
Preliminary analysis of the file indicated this was not a false positive alarm, i.e., an incorrect report of a threat when none was actually present, and Microsoft was notified, who not just promptly removed the file from their Update Catalog, but have even blocked access to the web page that used to host through Internet Explorer's SmartScreen Filter, as you can see from this screen capture:
From previous experience, we know that Microsoft goes to extraordinary lengths to screen third-party content provided for distribution through their Update Catalog, so it is somewhat bewildering to see it hosting malicious software, especially such an older threat. We were, however, quite impressed at Microsoft's prompt response in removing the malicious file.
IT managers and consumers rely on Microsoft update services like Microsoft Update to detect and apply patches and security fixes for operating systems and applications, and consider it a safe and trusted source. It is important to remember, though, that although a file may be downloaded from Microsoft, it may not be written by them, especially in the case of a device driver.
I would like to point out, though, that this could have happened with another vendor: Centralized update services for operating systems are not unique to Microsoft. Many developers provide such services for computers running their operating systems and, increasingly, so do the vendors of smart phones as well. While operating system vendors routinely check for threats in new device drivers provided to them by third-parties, it would probably be a good idea if they periodically scanned their existing catalogs, too, regardless of how old they are.
As previously mentioned, we view this as more of a statistical aberration than the norm, but do want to remind people that it is important to take adequate precautions when downloading files, even if they are from a trusted source like Microsoft.
Aryeh Goretsky, MVP, ZCSE
Distinguished Researcher
Distinguished Researcher